Question: I need help to figure this out. MISonline Information Security Risk Management Mini-Problem-1 YBO Inc. has an average size infrastructure. Some of its services are
I need help to figure this out.
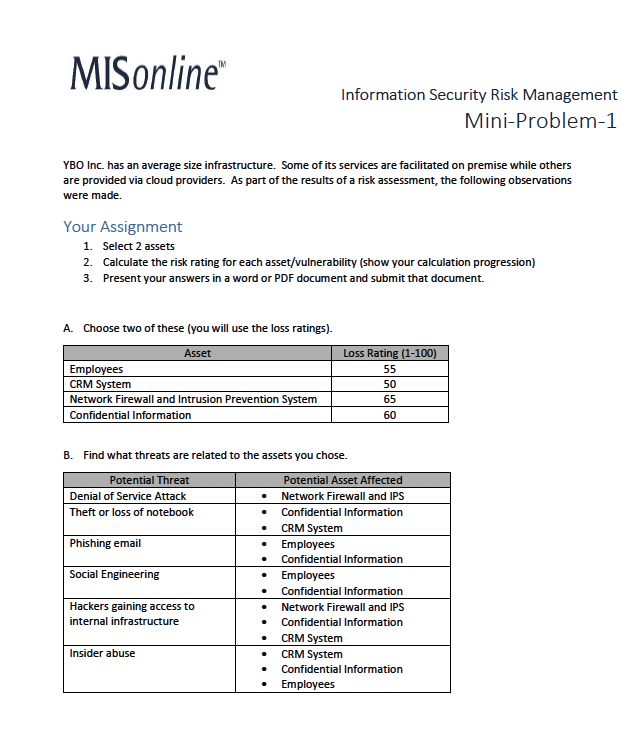
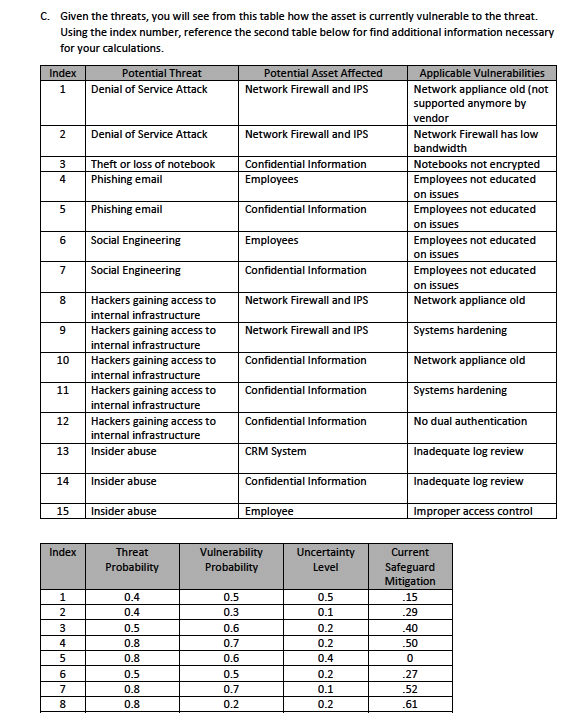
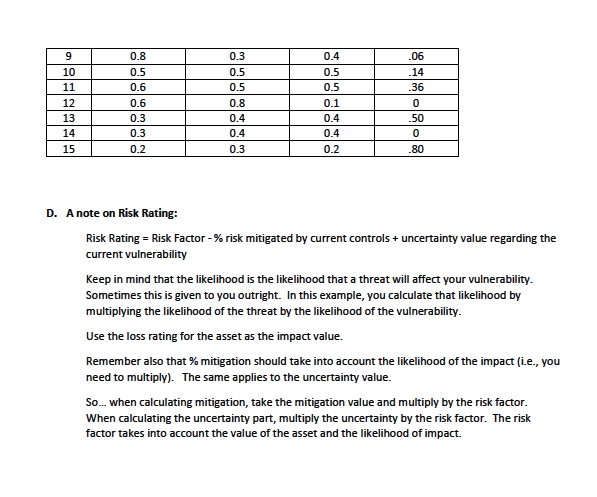
MISonline Information Security Risk Management Mini-Problem-1 YBO Inc. has an average size infrastructure. Some of its services are facilitated on premise while others are provided via cloud providers. As part of the results of a risk assessment, the following observations were made. Your Assignment 1. Select 2 assets 2. Calculate the risk rating for each asset/vulnerability (show your calculation progression) 3. Present your answers in a word or PDF document and submit that document. A. Choose two of these (you will use the loss ratings). Asset Loss Rating (1-100) Employees 55 CRM System 50 Network Firewall and Intrusion Prevention System 65 Confidential Information 60 B. Find what threats are related to the assets you chose. Potential Threat Potential Asset Affected Denial of Service Attack Network Firewall and IPS Theft or loss of notebook Confidential Information CRM System Phishing email Employees Confidential Information Social Engineering . Employees Confidential Information Hackers gaining access to Network Firewall and IPS internal infrastructure Confidential Information CRM System Insider abuse CRM System Confidential Information EmployeesC. Given the threats, you will see from this table how the asset is currently vulnerable to the threat. Using the index number, reference the second table below for find additional information necessary for your calculations. Index Potential Threat Potential Asset Affected Applicable Vulnerabilities 1 Denial of Service Attack Network Firewall and IPS Network appliance old (not supported anymore by vendor 2 Denial of Service Attack Network Firewall and IPS Network Firewall has low bandwidth 3 Theft or loss of notebook Confidential Information Notebooks not encrypted Phishing email Employees Employees not educated on issues 5 Phishing email Confidential Information Employees not educated on issues 6 Social Engineering Employees Employees not educated on issues 7 Social Engineering Confidential Information Employees not educated on issues 8 Hackers gaining access to Network Firewall and IPS Network appliance old internal infrastructure 9 Hackers gaining access to Network Firewall and IPS Systems hardening internal infrastructure 10 Hackers gaining access to Confidential Information Network appliance old internal infrastructure 11 Hackers gaining access to Confidential Information Systems hardening internal infrastructure 12 Hackers gaining access to Confidential Information No dual authentication internal infrastructure 13 Insider abuse CRM System Inadequate log review 14 Insider abuse Confidential Information Inadequate log review 15 Insider abuse Employee Improper access control Index Threat Vulnerability Uncertainty Current Probability Probability Level Safeguard Mitigation 0.4 0.5 0.5 15 0.4 0.3 0.1 29 3 0.5 0.6 0.2 40 0.8 0.7 0.2 .50 0.8 0.6 0.4 0 0.5 0.5 0.2 -27 0.8 0.7 0.1 .52 8 0.8 0.2 0.2 .610.8 0.3 0.4 06 10 0.5 0.5 0.5 14 11 0.6 D.5 0.5 36 12 0.6 0.8 0.1 0 13 0.3 0.4 0.4 50 14 0.3 0.4 0.4 0 15 0.2 D.3 0.2 80 D. A note on Risk Rating: Risk Rating = Risk Factor - % risk mitigated by current controls + uncertainty value regarding the current vulnerability Keep in mind that the likelihood is the likelihood that a threat will affect your vulnerability. Sometimes this is given to you outright. In this example, you calculate that likelihood by multiplying the likelihood of the threat by the likelihood of the vulnerability. Use the loss rating for the asset as the impact value. Remember also that % mitigation should take into account the likelihood of the impact (i.e., you need to multiply). The same applies to the uncertainty value. So.. when calculating mitigation, take the mitigation value and multiply by the risk factor. When calculating the uncertainty part, multiply the uncertainty by the risk factor. The risk factor takes into account the value of the asset and the likelihood of impact
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


