Question: i need python code to connect matlab code with application server to send the result of machine learning to the application server please quickly as
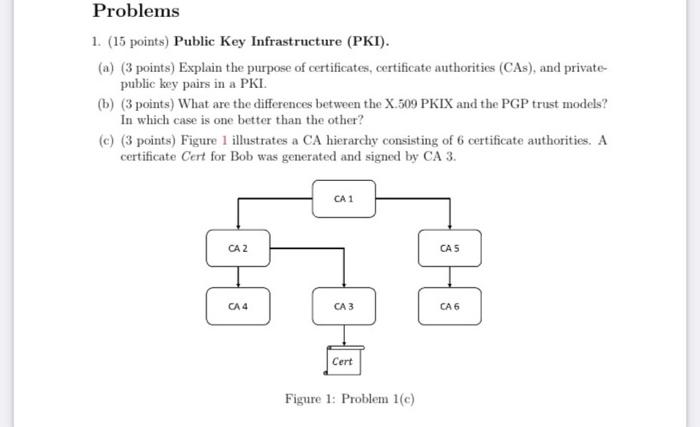
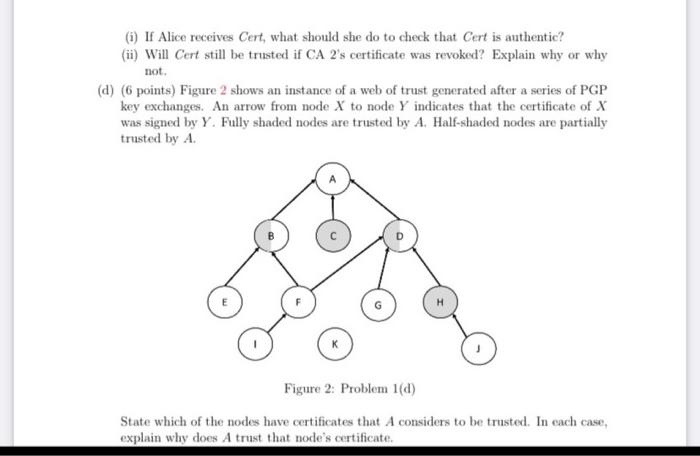
Problems 1. (15 points) Public Key Infrastructure (PKI). (a) (3 points) Explain the purpose of certificates, certificate authorities (CAs), and private public key pairs in a PKI (b) (3 points) What are the differences between the X.509 PKIX and the PGP trust models? In which case is one better than the other? (c) (3 points) Figure 1 illustrates a CA hierarchy consisting of 6 certificate authorities. A certificate Cert for Bob was generated and signed by CA 3. CA 1 CAZ CAS CA 4 CA 3 CA 6 Cert Figure 1: Problem 1(c) (1) If Alice receives Cert, what should she do to check that Cert is authentic? (ii) Will Cert still be trusted if CA 2's certificate was revoked? Explain why or why not. (d) (6 points) Figure 2 shows an instance of a web of trust generated after a series of PGP key exchanges. An arrow from node X to node Y indicates that the certificate of X was signed by Y. Fully shaded nodes are trusted by A. Half-shaded nodes are partially trusted by A. Figure 2: Problem 1(d) State which of the nodes have certificates that A considers to be trusted. In each case, explain why does A trust that node's certificate Problems 1. (15 points) Public Key Infrastructure (PKI). (a) (3 points) Explain the purpose of certificates, certificate authorities (CAs), and private public key pairs in a PKI (b) (3 points) What are the differences between the X.509 PKIX and the PGP trust models? In which case is one better than the other? (c) (3 points) Figure 1 illustrates a CA hierarchy consisting of 6 certificate authorities. A certificate Cert for Bob was generated and signed by CA 3. CA 1 CAZ CAS CA 4 CA 3 CA 6 Cert Figure 1: Problem 1(c) (1) If Alice receives Cert, what should she do to check that Cert is authentic? (ii) Will Cert still be trusted if CA 2's certificate was revoked? Explain why or why not. (d) (6 points) Figure 2 shows an instance of a web of trust generated after a series of PGP key exchanges. An arrow from node X to node Y indicates that the certificate of X was signed by Y. Fully shaded nodes are trusted by A. Half-shaded nodes are partially trusted by A. Figure 2: Problem 1(d) State which of the nodes have certificates that A considers to be trusted. In each case, explain why does A trust that node's certificate
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


