Question: i. What is this code used for? ii. How many bits is it using? Q4: Encryption: 1. import javax.crypto.Cipher; 2. import javax.crypto.KeyGenerator; 3. import
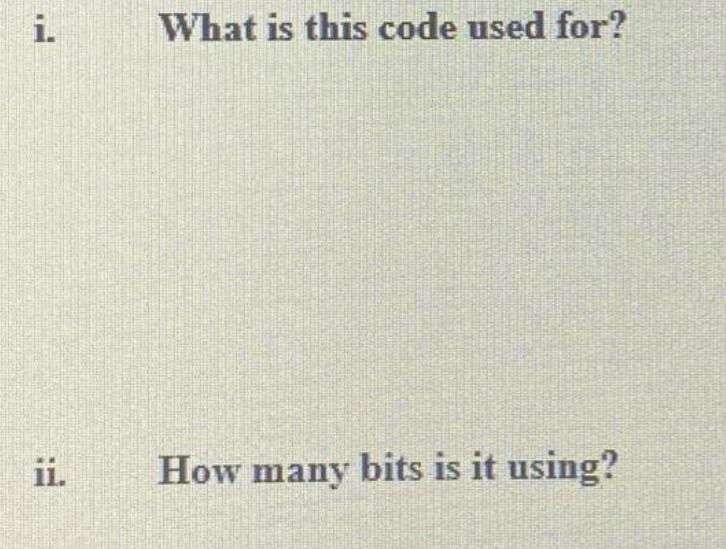
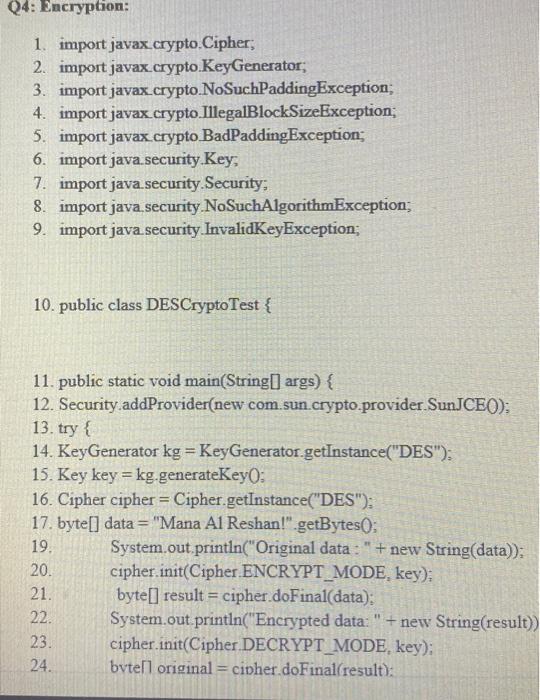
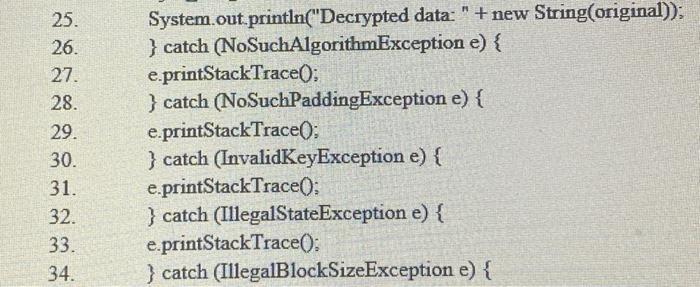
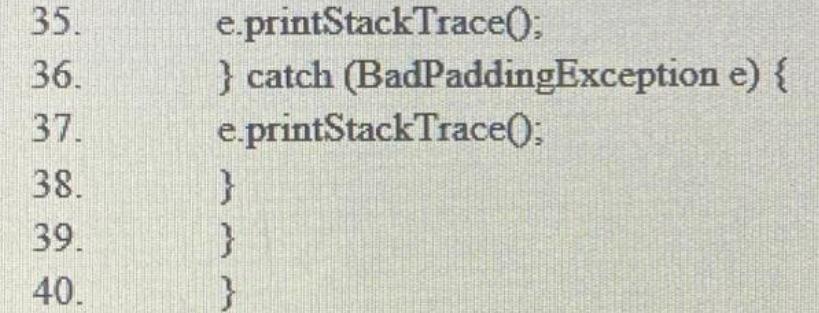
i. What is this code used for? ii. How many bits is it using? Q4: Encryption: 1. import javax.crypto.Cipher; 2. import javax.crypto.KeyGenerator; 3. import javax.crypto.NoSuchPaddingException; 4. import javax.crypto.IllegalBlockSizeException; 5. import javax.crypto BadPaddingException; 6. import java.security.Key; 7. import java.security.Security; 8. import java security NoSuchAlgorithmException; 9. import java.security InvalidKeyException; 10. public class DESCryptoTest { 11. public static void main(String[] args) { 12. Security.addProvider(new com.sun.crypto.provider.SunJCE()); 13. try { 14. KeyGenerator kg = KeyGenerator.getInstance("DES"); 15. Key key = kg.generateKey(): 16. Cipher cipher = Cipher.getInstance("DES"); 17. byte[] data="Mana Al Reshan!".getBytes(); 19. 20. 21. 22. 23. 24. System.out.println("Original data : " +new String(data)); cipher.init(Cipher ENCRYPT_MODE, key); byte[] result = cipher.doFinal(data); System.out.println("Encrypted data: " + new String(result)) cipher.init(Cipher DECRYPT_MODE, key); bvtell original= cipher.doFinal(result): 25. 26. 27. 28. 29. 30. 31. 32. 33. 34. System.out.println("Decrypted data: " + new String(original)); } catch (NoSuchAlgorithmException e) { e.printStackTrace(); } catch (NoSuchPaddingException e) { e.printStackTrace(); } catch (InvalidKeyException e) { e.printStackTrace(); } catch (IllegalStateException e) { e.printStackTrace(); } catch (IllegalBlockSizeException e) { 35. 36. 37. 38. 39. 40. e.printStackTrace(); } catch (BadPaddingException e) { e.printStackTrace(); } } bod }
Step by Step Solution
There are 3 Steps involved in it
This Java code appears to be a simple example of using the DES Data Encryption Standard algorithm for encryption and decryption Heres a breakdown of t... View full answer

Get step-by-step solutions from verified subject matter experts


