Question: Implementation of Cryptographic Algorithms Assigned: Nov. 11, 2017 Due: Nov. 19, 2017 In this assignment, you will gain better understanding of cryptography by implementing a
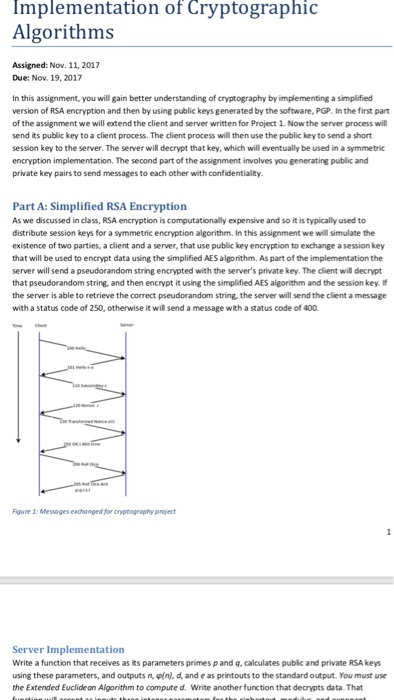
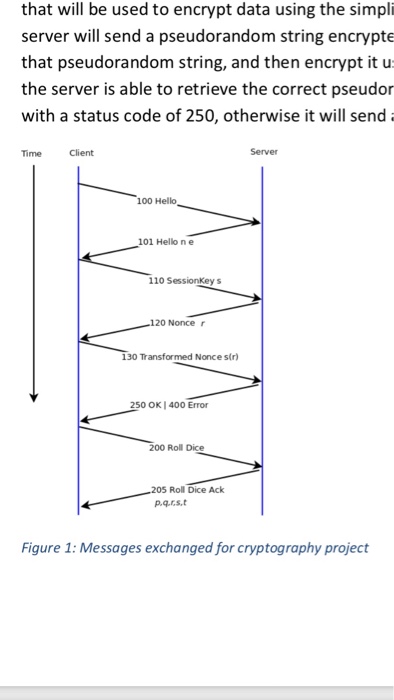




Implementation of Cryptographic Algorithms Assigned: Nov. 11, 2017 Due: Nov. 19, 2017 In this assignment, you will gain better understanding of cryptography by implementing a simplified version of RSA encryption and then by using public keys generated by the software, PGP. In the first part of the assignment we will extend the client and server written for Project 1. Now the server process will send its public key to a cient process. The dlient process will hen use the public key to send a short session key to the server. The server will decrypt that key, which will eventually be used in a symmetric encryption implementation. The second part of the assignment involves you generating public and private key pairs to send messages to each other with confidentiality. Part A: Simplified RSA Encryption As we discussed in class, RSA encryption is computationally expensive and so it is typically used to distribute session keys for a symmetric encryption algorithm. In this assignment we will simulate the existence of two parties, a client and a server, that use public key encryption to exchange a session key that will be used to encrypt data using the simplified AES algorithm. As part of the implementation the server will send a pseudorandom string encrypted with the server's private key. The client will decrypt that pseudorandom string, and then encrypt it using the simplified AES algorithm and the session key. f the server is able to retrieve the correct pseudorandom string, the server will send the client a message with a status code of 250, otherwise it will send a message with a status code of 400. Figure I: Messages exhanged for cryptography project Server Implementation Write a function that receives as its parameters primes p and q, calculates public and private RSA keys using these parameters, and outputs, (nd, and e as printouts to the standard output. You must use the Extended Euclide an Algorithm to compute d. Write another function that decrypts data. That Implementation of Cryptographic Algorithms Assigned: Nov. 11, 2017 Due: Nov. 19, 2017 In this assignment, you will gain better understanding of cryptography by implementing a simplified version of RSA encryption and then by using public keys generated by the software, PGP. In the first part of the assignment we will extend the client and server written for Project 1. Now the server process will send its public key to a cient process. The dlient process will hen use the public key to send a short session key to the server. The server will decrypt that key, which will eventually be used in a symmetric encryption implementation. The second part of the assignment involves you generating public and private key pairs to send messages to each other with confidentiality. Part A: Simplified RSA Encryption As we discussed in class, RSA encryption is computationally expensive and so it is typically used to distribute session keys for a symmetric encryption algorithm. In this assignment we will simulate the existence of two parties, a client and a server, that use public key encryption to exchange a session key that will be used to encrypt data using the simplified AES algorithm. As part of the implementation the server will send a pseudorandom string encrypted with the server's private key. The client will decrypt that pseudorandom string, and then encrypt it using the simplified AES algorithm and the session key. f the server is able to retrieve the correct pseudorandom string, the server will send the client a message with a status code of 250, otherwise it will send a message with a status code of 400. Figure I: Messages exhanged for cryptography project Server Implementation Write a function that receives as its parameters primes p and q, calculates public and private RSA keys using these parameters, and outputs, (nd, and e as printouts to the standard output. You must use the Extended Euclide an Algorithm to compute d. Write another function that decrypts data. That
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


