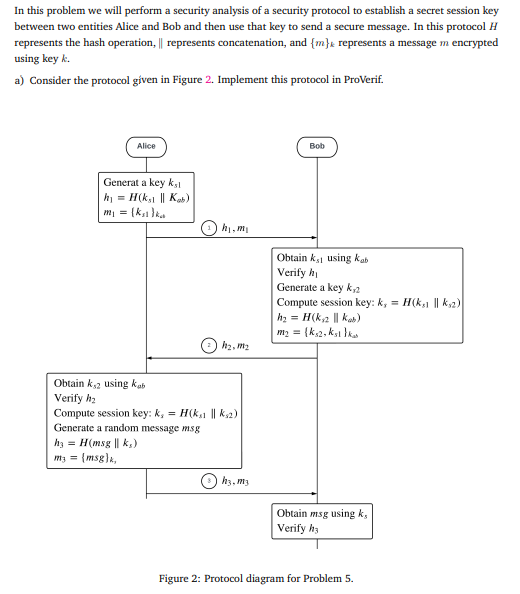
Question: In this problem we will perform a security analysis of a security protocol to establish a secret session key between two entities Alice and Bob
In this problem we will perform a security analysis of a security protocol to establish a secret session key
between two entities Alice and Bob and then use that key to send a secure message. In this protocol H
represents the hash operation, represents concatenation, and mk represents a message m encrypted
using key k
a Consider the protocol given in Figure Implement this protocol in ProVerif
solve also other questions in second picture please :)
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


