Question: infromation security principles , please answer these questions in details Bob offered Alice an X amount of money to complete a job. A hash value
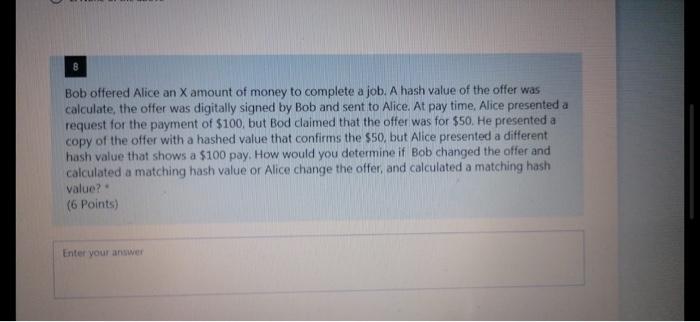
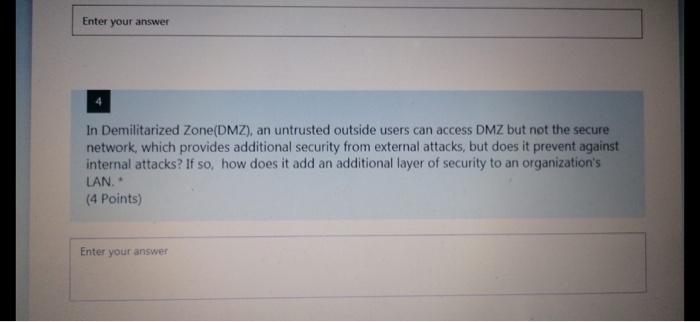
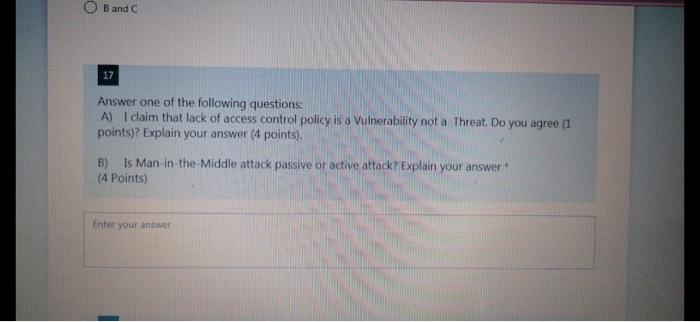
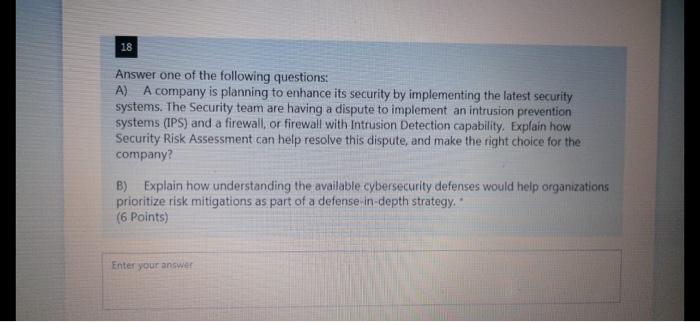
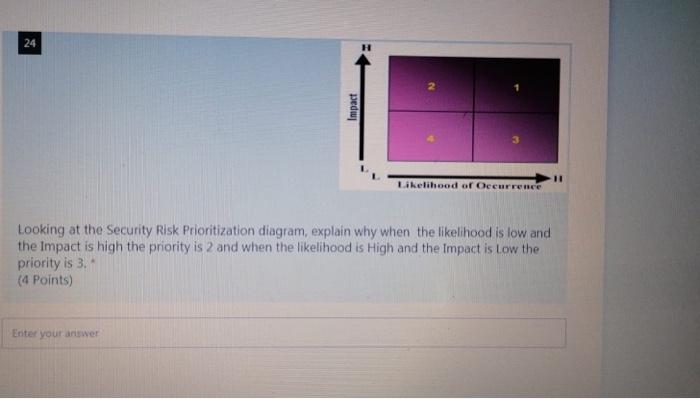
Bob offered Alice an X amount of money to complete a job. A hash value of the offer was calculate, the offer was digitally signed by Bob and sent to Alice. At pay time. Alice presented a request for the payment of $100, but Bod claimed that the offer was for $50. He presented a copy of the offer with a hashed value that confirms the $50, but Alice presented a different hash value that shows a $100 pay. How would you determine if Bob changed the offer and calculated a matching hash value or Alice change the offer, and calculated a matching hash value? (6 Points) Enter your answer Enter your answer In Demilitarized Zone(DMZ), an untrusted outside users can access DMZ but not the secure network, which provides additional security from external attacks, but does it prevent against internal attacks? If so, how does it add an additional layer of security to an organization's LAN. (4 Points) Enter your answer O Band C 17 Answer one of the following questions: A) I claim that lack of access control policy is a Vulnerability not a Threat. Do you agree (1 points)? Explain your answer (4 points) B) is Man in the Middle attack passive or active attack? Explain your answer (4 Points) Enter your answer 18 Answer one of the following questions: A) A company is planning to enhance its security by implementing the latest security systems. The Security team are having a dispute to implement an intrusion prevention systems (IPS) and a firewall, or firewall with Intrusion Detection capability. Explain how Security Risk Assessment can help resolve this dispute, and make the right choice for the company? B) Explain how understanding the available cybersecurity defenses would help organizations prioritize risk mitigations as part of a defense in-depth strategy. (6 Points) Enter your answer gbZoiCGAYL-569HP UNTUKNEZEWFAMVIRGMANIRRI 23 An insurance company asks for your opinion about the best way to grant access to their systems. Explain why/why not they need both authentication and access control? What is the best authentication method they may implement? (4 Points) Enter your answer 24 Impact Likelihood or Occurrence Looking at the Security Risk Prioritization diagram, explain why when the likelihood is low and the Impact is high the priority is 2 and when the likelihood is High and the impact is Low the priority is 3. (4 Points) Enter your answer 25 Answer one of the following questions: A) Explain how a VPN can hide a user's browsing activity and how it can prevent user's personal browsing data leakage? B) No organization with sensitive data or critical operations should be without anomaly- based detection to protect against existing security attacks. Do you agree? Explain your answer (4 Points) Enter your answer Bob offered Alice an X amount of money to complete a job. A hash value of the offer was calculate, the offer was digitally signed by Bob and sent to Alice. At pay time. Alice presented a request for the payment of $100, but Bod claimed that the offer was for $50. He presented a copy of the offer with a hashed value that confirms the $50, but Alice presented a different hash value that shows a $100 pay. How would you determine if Bob changed the offer and calculated a matching hash value or Alice change the offer, and calculated a matching hash value? (6 Points) Enter your answer Enter your answer In Demilitarized Zone(DMZ), an untrusted outside users can access DMZ but not the secure network, which provides additional security from external attacks, but does it prevent against internal attacks? If so, how does it add an additional layer of security to an organization's LAN. (4 Points) Enter your answer O Band C 17 Answer one of the following questions: A) I claim that lack of access control policy is a Vulnerability not a Threat. Do you agree (1 points)? Explain your answer (4 points) B) is Man in the Middle attack passive or active attack? Explain your answer (4 Points) Enter your answer 18 Answer one of the following questions: A) A company is planning to enhance its security by implementing the latest security systems. The Security team are having a dispute to implement an intrusion prevention systems (IPS) and a firewall, or firewall with Intrusion Detection capability. Explain how Security Risk Assessment can help resolve this dispute, and make the right choice for the company? B) Explain how understanding the available cybersecurity defenses would help organizations prioritize risk mitigations as part of a defense in-depth strategy. (6 Points) Enter your answer gbZoiCGAYL-569HP UNTUKNEZEWFAMVIRGMANIRRI 23 An insurance company asks for your opinion about the best way to grant access to their systems. Explain why/why not they need both authentication and access control? What is the best authentication method they may implement? (4 Points) Enter your answer 24 Impact Likelihood or Occurrence Looking at the Security Risk Prioritization diagram, explain why when the likelihood is low and the Impact is high the priority is 2 and when the likelihood is High and the impact is Low the priority is 3. (4 Points) Enter your answer 25 Answer one of the following questions: A) Explain how a VPN can hide a user's browsing activity and how it can prevent user's personal browsing data leakage? B) No organization with sensitive data or critical operations should be without anomaly- based detection to protect against existing security attacks. Do you agree? Explain your answer (4 Points) Enter your
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


