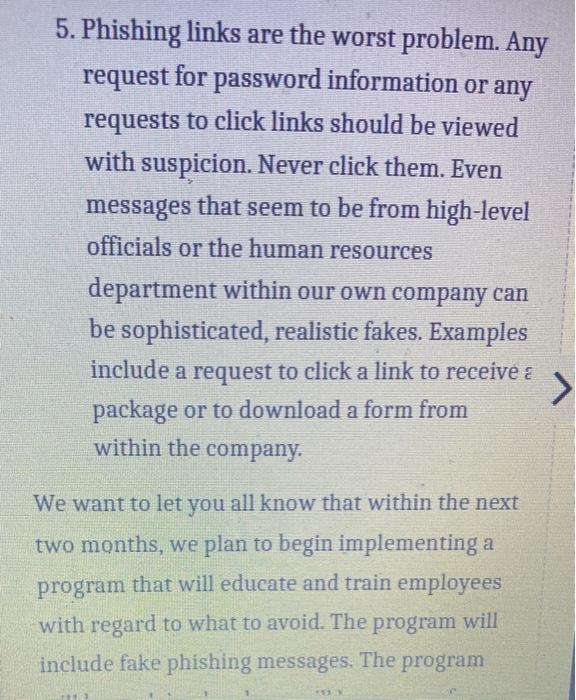
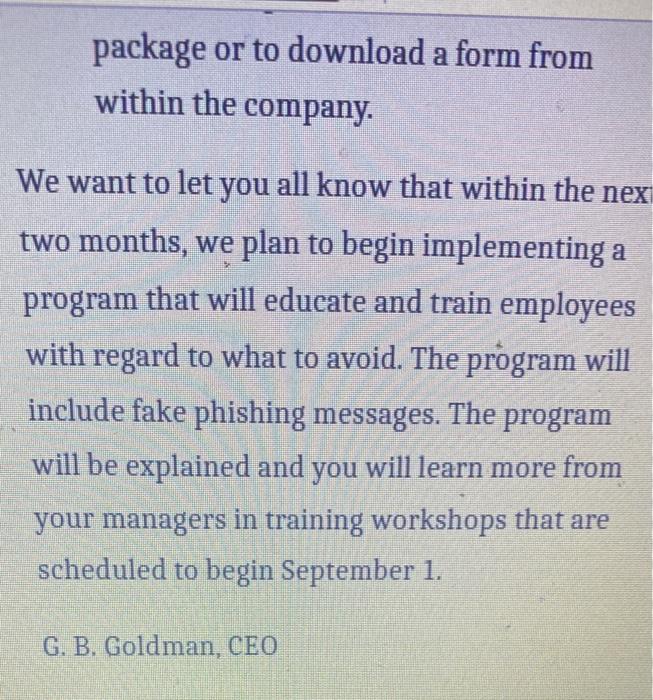
Question: Instructions: Please rewrite this e-mail. You will find this e-mail suffers from a vague and imprecise subject line. It includes a long lead-in and wordy
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


