Question: IV . There is an active connection between a Telnet client ( 1 0 . 0 . 2 . 5 ) and a Telnet server
IV There is an active connection between a Telnet client and a Telnet server
The server has just acknowledged a sequence number and the client has
just acknowledged a sequence number An attacker wants to launch the TCP session
hijacking attack on the connection, so he can execute a command on the server. He is on
the same local area network as these two computers. You need to construct a TCP packet
for the attacker. Please fill in the following fields:
Source IP and Destination IP
Source port and Destination port
Sequence number
The TCP data field.
Section : PKI Public Key Infrastructure
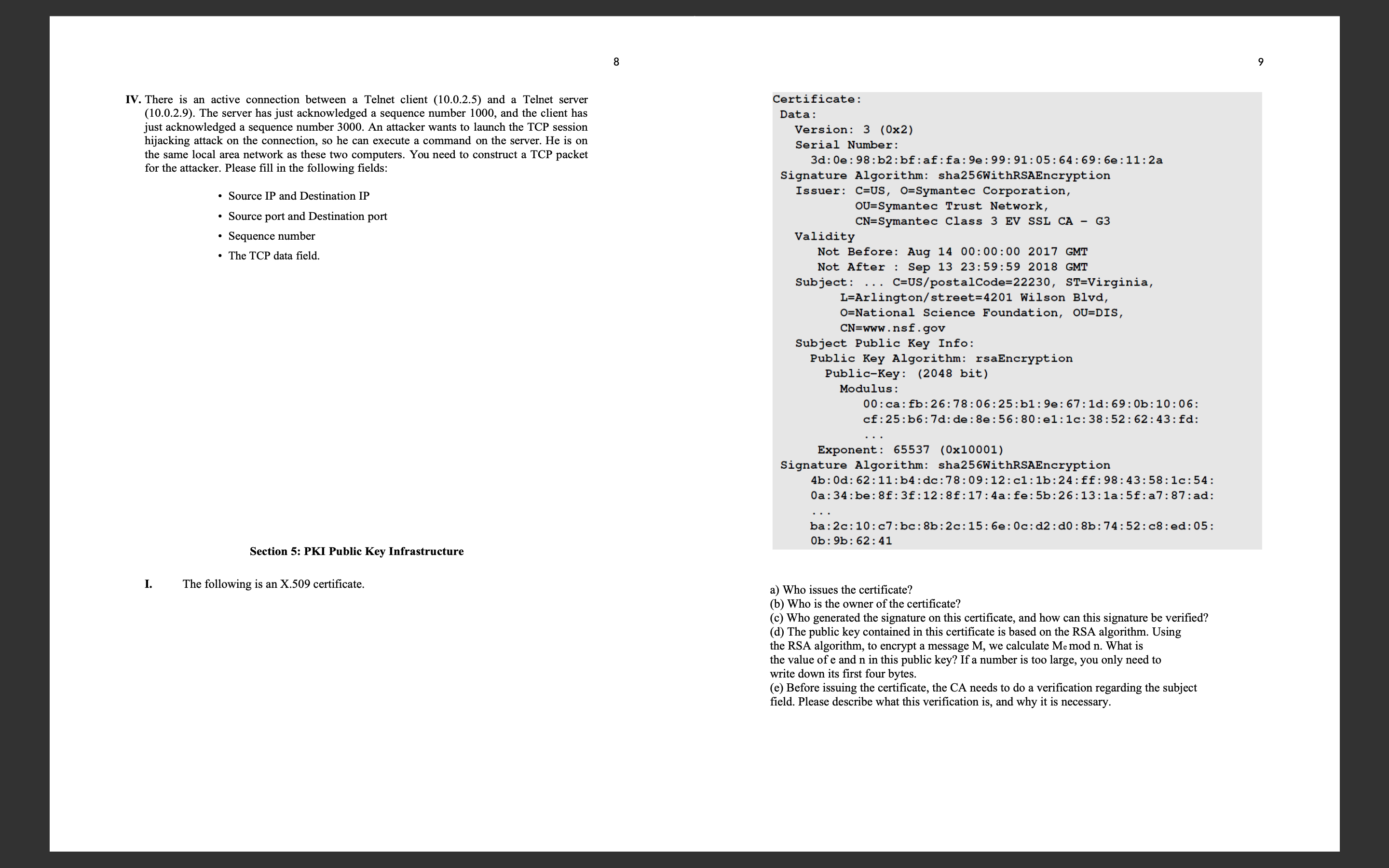
I. The following is an X certificate.
Certificate:
Data:
Version:
Serial Number:
d:e: :b:bf : af : fa: e: : ::::e::a
Signature Algorithm: shaWithRSAEncryption
Issuer: CUS OSymantec Corporation,
OUSymantec Trust Network,
CNSymantec Class SSL CA G
Validity
Not Before: Aug :: GMT
Not After : Sep :: GMT
Subject: C CUSpostalCode STVirginia,
Arlingtonstreet WilsonBlvd,
ONational Science Foundation, OUDIS,
CNwww nsf gov
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
PublicKey: bit
Modulus :
:::::::::::::: :
cf: : b: d: de :::: e :::::: :
Exponent: x
Signature Algorithm: shaWithRSAEncryption
b:d: ::::::::::::::: :
:: be: f: f : :::: fe: b:::a: f:a: :ad:
ba:c: ::::::::::::::::
ob: ::
a Who issues the certificate?
b Who is the owner of the certificate?
c Who generated the signature on this certificate, and how can this signature be verified?
d The public key contained in this certificate is based on the RSA algorithm. Using
the RSA algorithm, to encrypt a message we calculate Memodn. What is
the value of and in this public key? If a number is too large, you only need to
write down its first four bytes.
e Before issuing the certificate, the CA needs to do a verification regarding the subject
field. Please describe what this verification is and why it is necessary.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


