Question: L A Moving to another question will save this response. Question 19 Consider the below screenshot of the results of port scanning in Victime 1
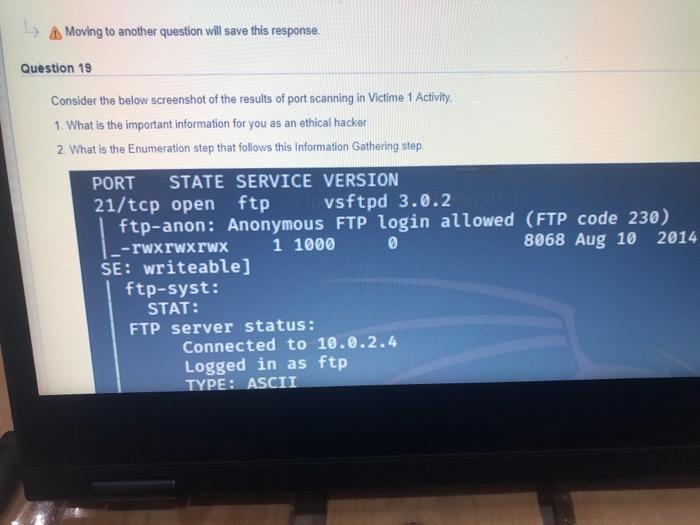
L A Moving to another question will save this response. Question 19 Consider the below screenshot of the results of port scanning in Victime 1 Activity 1. What is the important information for you as an ethical hacker 2 What is the Enumeration step that follows this Information Gathering step PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 ftp-anon: Anonymous FTP login allowed (FTP code 230) -rwxrwxrwx 1 1000 0 8068 Aug 10 2014 SE: writeable] ftp-syst: STAT: FTP server status: Connected to 10.0.2.4 Logged in as ftp TYPE: ASCIT plete estion 22 Craft a LAND and SMURF DoS attack packets against victim machine 10.0.2.4. For the toolbar, press ALT+F10 (PC) or ALT+FN+F10 (Mac). B I y s Paragraph V Arial 14px 3 x X2 * sf fle 36 L A Moving to another question will save this response. Question 19 Consider the below screenshot of the results of port scanning in Victime 1 Activity 1. What is the important information for you as an ethical hacker 2 What is the Enumeration step that follows this Information Gathering step PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 ftp-anon: Anonymous FTP login allowed (FTP code 230) -rwxrwxrwx 1 1000 0 8068 Aug 10 2014 SE: writeable] ftp-syst: STAT: FTP server status: Connected to 10.0.2.4 Logged in as ftp TYPE: ASCIT plete estion 22 Craft a LAND and SMURF DoS attack packets against victim machine 10.0.2.4. For the toolbar, press ALT+F10 (PC) or ALT+FN+F10 (Mac). B I y s Paragraph V Arial 14px 3 x X2 * sf fle 36
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


