Question: Leaking or hiding the message length EAV-security for symmetric key secrecy PrivK-EAV An (n) 1 iff b (Gen, Enc, Dec) security parameter 1 M 10,1)
Leaking or hiding the message length
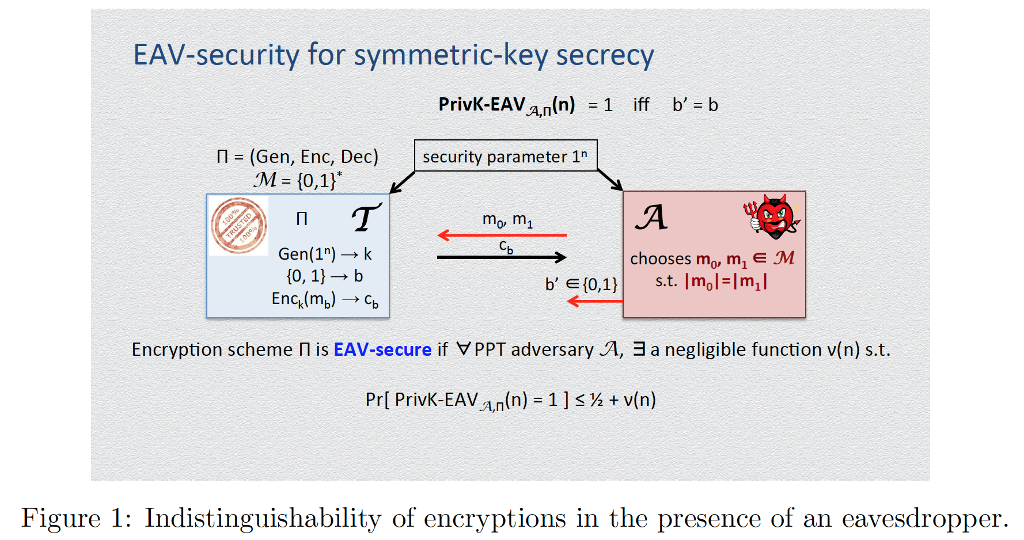
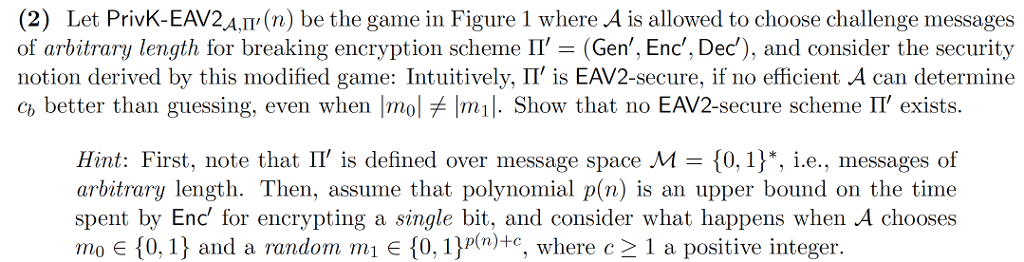
EAV-security for symmetric key secrecy PrivK-EAV An (n) 1 iff b (Gen, Enc, Dec) security parameter 1 M 10,1) mo, m Gen(1 chooses m m, E M (0, 1) b s.t. m Im b' E10,1) Enck(mb) cb Encryption scheme n is EAV-secure if v PPT adversary A, a a negligible function v(n) s.t. Figure 1: Indistinguishability of encryptions in the presence of an eavesdropper. EAV-security for symmetric key secrecy PrivK-EAV An (n) 1 iff b (Gen, Enc, Dec) security parameter 1 M 10,1) mo, m Gen(1 chooses m m, E M (0, 1) b s.t. m Im b' E10,1) Enck(mb) cb Encryption scheme n is EAV-secure if v PPT adversary A, a a negligible function v(n) s.t. Figure 1: Indistinguishability of encryptions in the presence of an eavesdropper
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


