Question: Long Answer Oestions: Answer all the following questions: C1. Answer the following questions: C1.1: Classify the following scenario to their type of social engineering attack
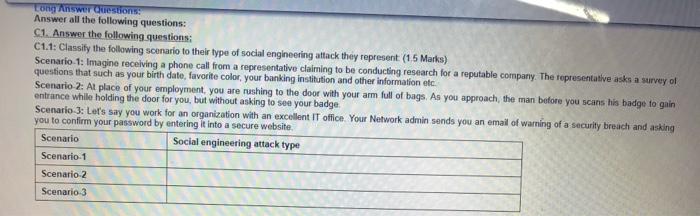
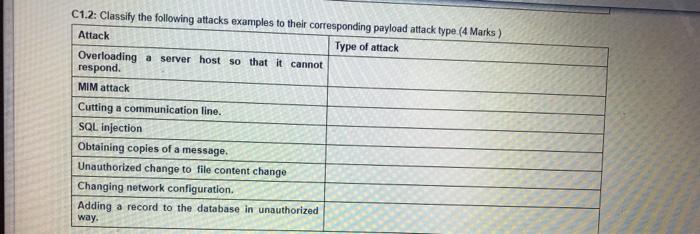
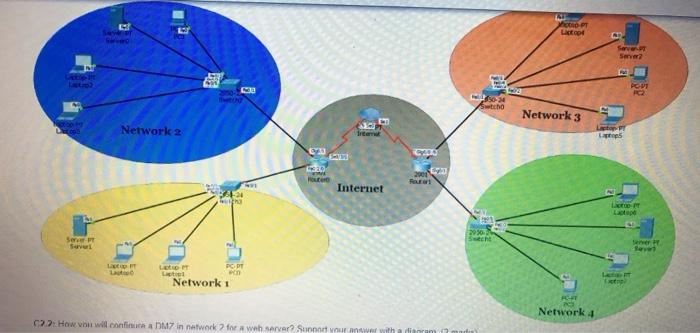
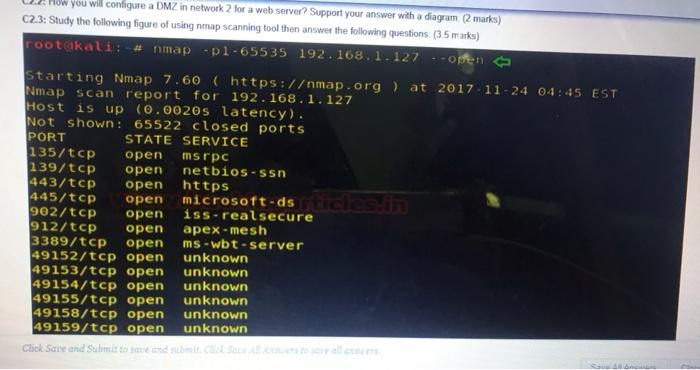
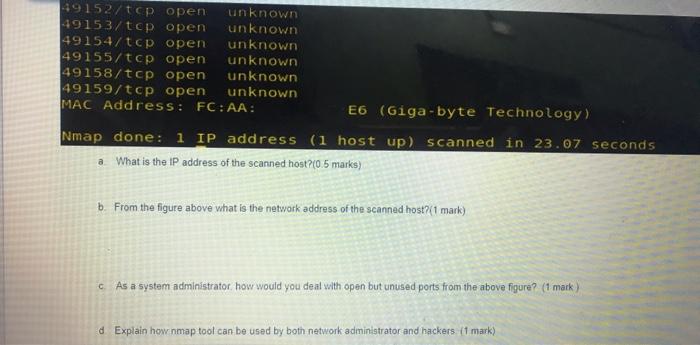
Long Answer Oestions: Answer all the following questions: C1. Answer the following questions: C1.1: Classify the following scenario to their type of social engineering attack they represent(15 Marks) Scenario 1: Imagine receiving a phone call from a representative claiming to be conducting research for a reputable company. The representative asks a survey ol questions that such as your birth date, favorite color, your banking institution and other information etc. Scenario 2: At place of your employment, you are rushing to the door with your arm full of bags. As you approach, the man before you scans his badge to gain entrance while holding the door for you, but without asking to see your badge Scenario 3: Let's say you work for an organization with an excellent IT office. Your Network admin sends you an email of warning of a security breach and asking you to confirm your password by entering it into a secure website. Scenario Social engineering attack type Scenario 1 Scenario 2 Scenario 3 C1.2: Classify the following attacks examples to their corresponding payload attack type (4 Marks) Attack Type of attack Overloading a server host so that it cannot respond MIM attack Cutting a communication line. SQL injection Obtaining copies of a message. Unauthorized change to file content change Changing network configuration. Adding a record to the database in unauthorized way. C1.3. Explain how the principle of least privilege principle is implemented differently in UNIX Linux and Windows operating system. (2 marks) C2. Answer the following questions: C2.1 From the diagram below consider yourself the administrator of below networks How to reduce the attack surface from Internet network to t systems of hosts on the network 1 2 3 and 4 (2 Marks) hot PT Lot ST PPT 34 Scho Network 3 Network 2 Ircow TO 2001 HO Internet PT 29 30 Sent Sere Suvi LOFT La Lot PT Lastest Network 1 HT 20 Network C22 How it will con DM7 in network for a web server Sunnur answer with you will configure a DMZ in network for a web server? Support your answer with a diagram 2 marks) C2.3: Study the following figure of using nmap scanning tool then answer the following questions (3.5 marks) root@kali: # nmap-01-65535 192.168.1.127 open Starting Nmap 7.60 (https:/map.org ) at 2017-11-24 04:45 EST Nmap scan report for 192.168.1.127 Host is up (0.00205 latency). Not shown: 65522 closed ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 443/tcp open https 445/tcp open microsoft.dstielin 902/tcp open iss-realsecure 912/tcp open apex-mesh 3389/tcp open ms - wbt-server 49152/tcp open unknown 49153/tcp open unknown 49154/tcp open unknown 49155/tcp open unknown 49158/tcp open unknown 49159/tcp open unknown Chek Sare and Submit to and the Sultan 49152/tcp open unknown 49153/tcp open unknown 49154/tcp open unknown 49155/tcp open unknown 49158/tcp open unknown 49159/tcp open unknown MAC Address: FC:AA: E6 (Gigabyte Technology) Nmap done: i IP address (1 host up) scanned in 23.07 seconds a What is the IP address of the scanned host?(0.5 marks) b. From the figure above what is the network address of the scanned host?(1 mark) As a system administrator how would you deal with open but unused ports from the above figure? (1 mark) d Explain how nmap tool can be used by both network administrator and hackers (1 mark)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


