Question: Machine A receives the following ARP packet. Here we put the values and their meanings in the table. Field (size of the field MAC address
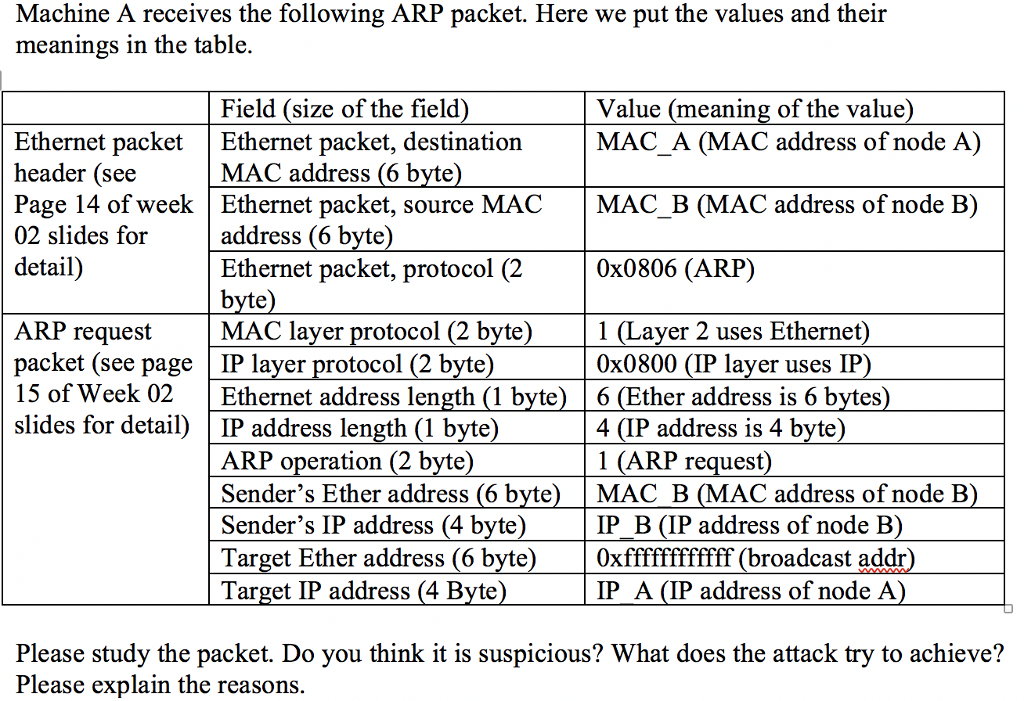
Machine A receives the following ARP packet. Here we put the values and their meanings in the table. Field (size of the field MAC address (6 byte address (6 byte) Value (meaning of the value Ethernet packet Ethernet packet, destinationMAC A (MAC address of node A) header (see Page 14 of week Ethernet packet, source MAC MAC B (MAC address of node B) 02 slides for detail) Ethernet packet, protocol (20x0806 (ARP) ARP request packet (see page |IP layer protocol (2 byte 15 of Week 02 Ethernet address length (1 byte) 6 (Ether address is 6 bytes slides for detail) IP address length (1 byte) MAC layer protocol (2 byte 1 (Layer 2 uses Ethernet 0x0800 (IP layer uses IIP 4 (IP address is 4 byte ARP operation (2 byte Sender's Ether address (6 byte) MAC B (MAC address of node B Sender's IP address (4 byte Target Ether address (6 byte Target IP address (4 Byte 1 (ARP request) IP B (IP address of node B Oxffffffffffff (broadcast addr IP A (IP address of node A Please study the packet. Do you think it is suspicious? What does the attack try to achieve? Please explain the reasons. Machine A receives the following ARP packet. Here we put the values and their meanings in the table. Field (size of the field MAC address (6 byte address (6 byte) Value (meaning of the value Ethernet packet Ethernet packet, destinationMAC A (MAC address of node A) header (see Page 14 of week Ethernet packet, source MAC MAC B (MAC address of node B) 02 slides for detail) Ethernet packet, protocol (20x0806 (ARP) ARP request packet (see page |IP layer protocol (2 byte 15 of Week 02 Ethernet address length (1 byte) 6 (Ether address is 6 bytes slides for detail) IP address length (1 byte) MAC layer protocol (2 byte 1 (Layer 2 uses Ethernet 0x0800 (IP layer uses IIP 4 (IP address is 4 byte ARP operation (2 byte Sender's Ether address (6 byte) MAC B (MAC address of node B Sender's IP address (4 byte Target Ether address (6 byte Target IP address (4 Byte 1 (ARP request) IP B (IP address of node B Oxffffffffffff (broadcast addr IP A (IP address of node A Please study the packet. Do you think it is suspicious? What does the attack try to achieve? Please explain the reasons
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


