Question: Micro Computers (MC) , is a small computer retail shop that sells computers and computer accessories to its customers in the Balitmore area. You are
Micro Computers (MC), is a small computer retail shop that sells computers and computer accessories to its customers in the Balitmore area. You are employed by MC, and your group is the team selected to create the company's security policy. The primary purpose of the security policy is to create a firewall-based network security solution for MC's network. There are 80 employees working in different roles ranging from sales to senior manager.MC has the following departments: Sales/Marketing, Store, Management where the accounting department is also hosted. The departments communicate internally within MC network and with the outside world via the internet regarding the operations and transactions related to the business processes.
image: Microsoft Active Directory environment( see attachment)
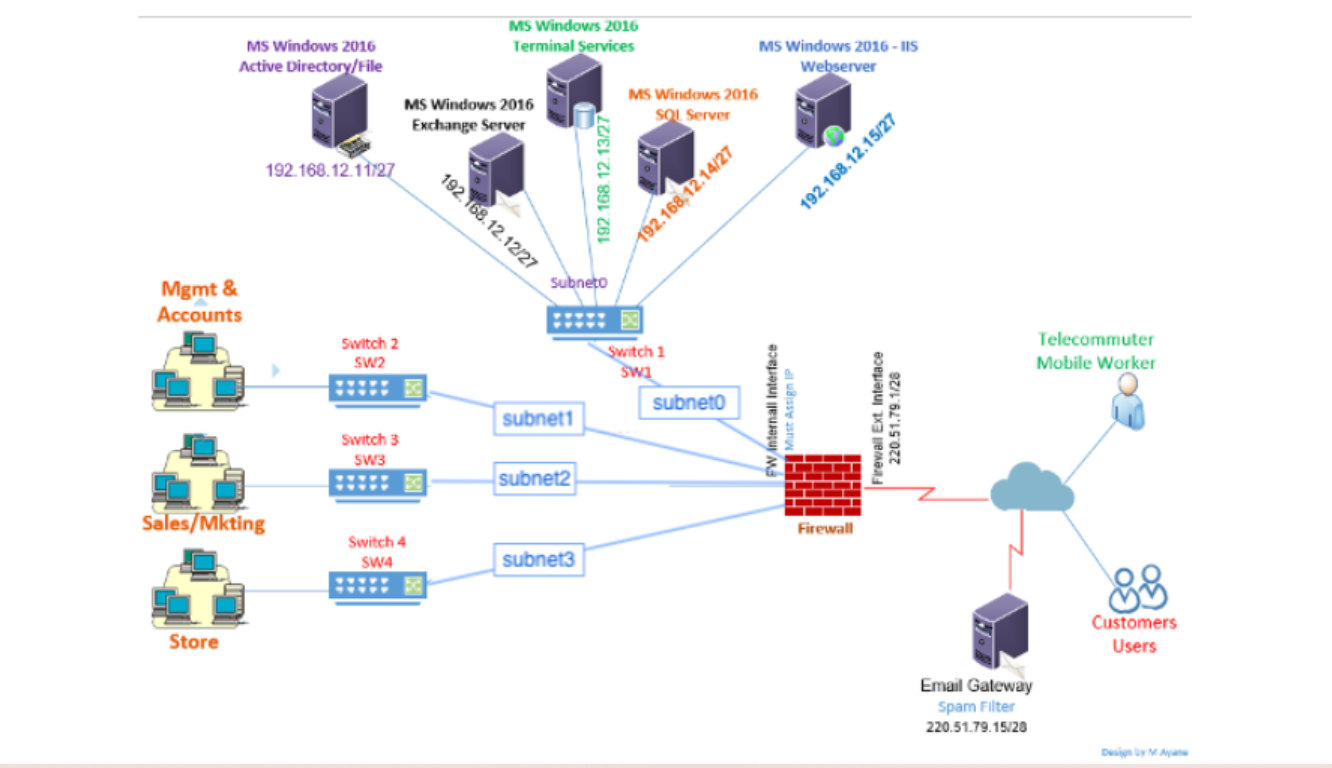
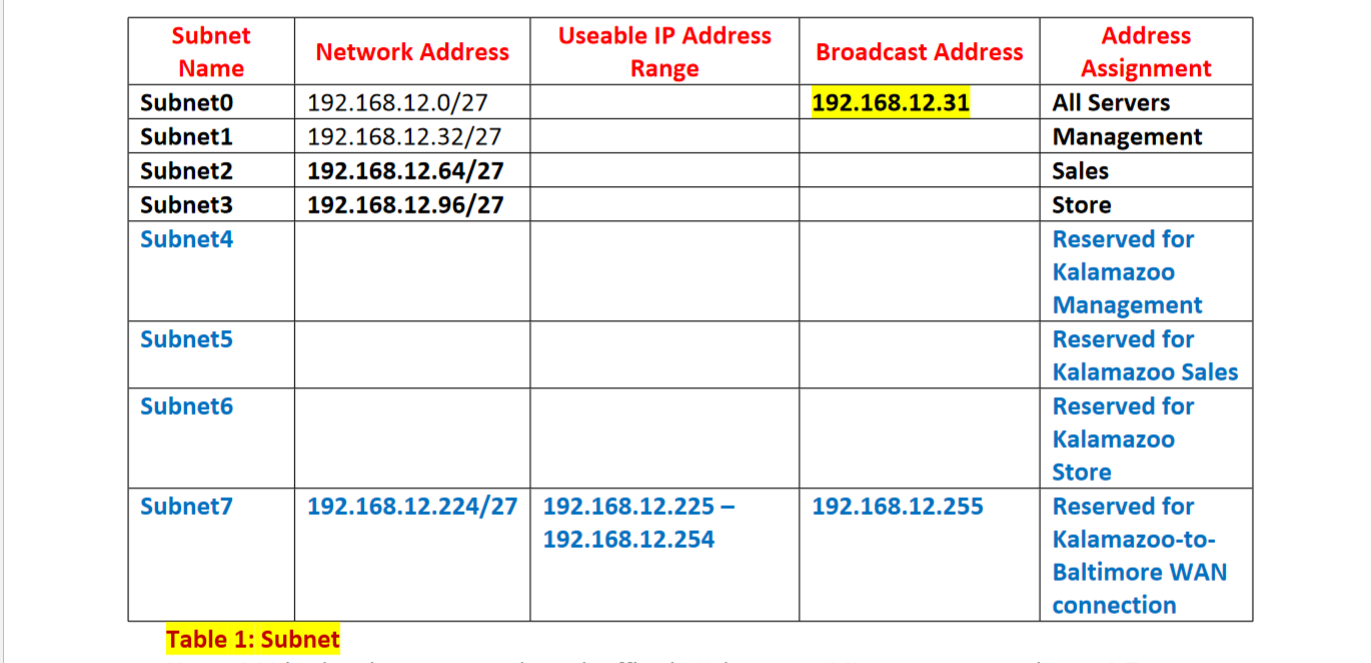
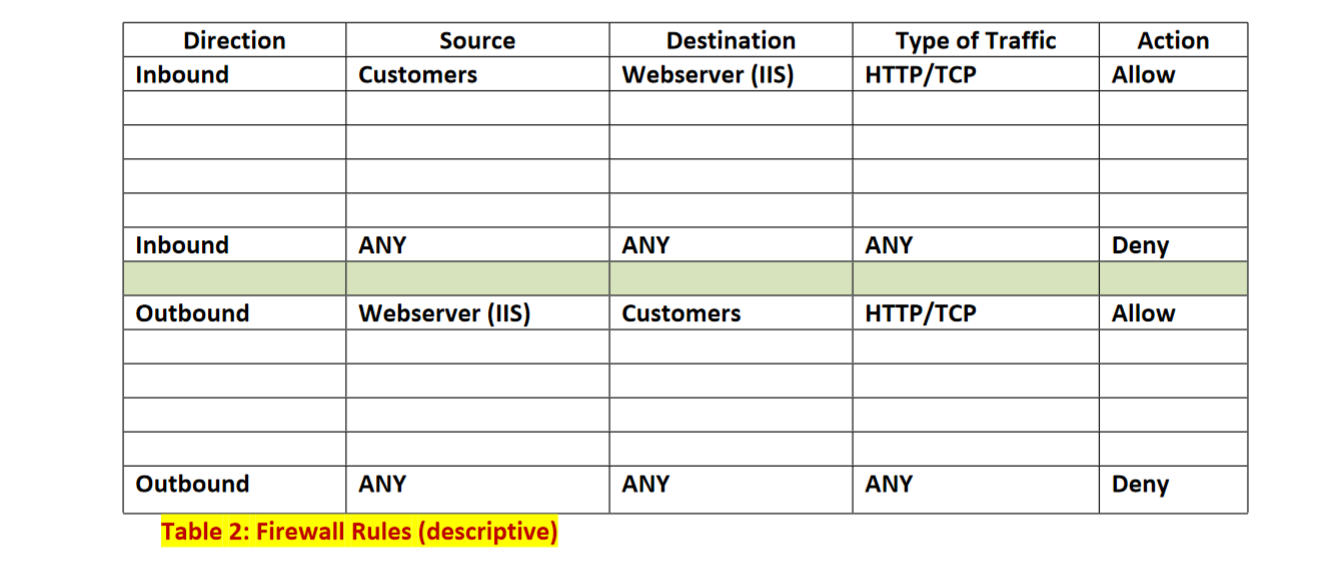
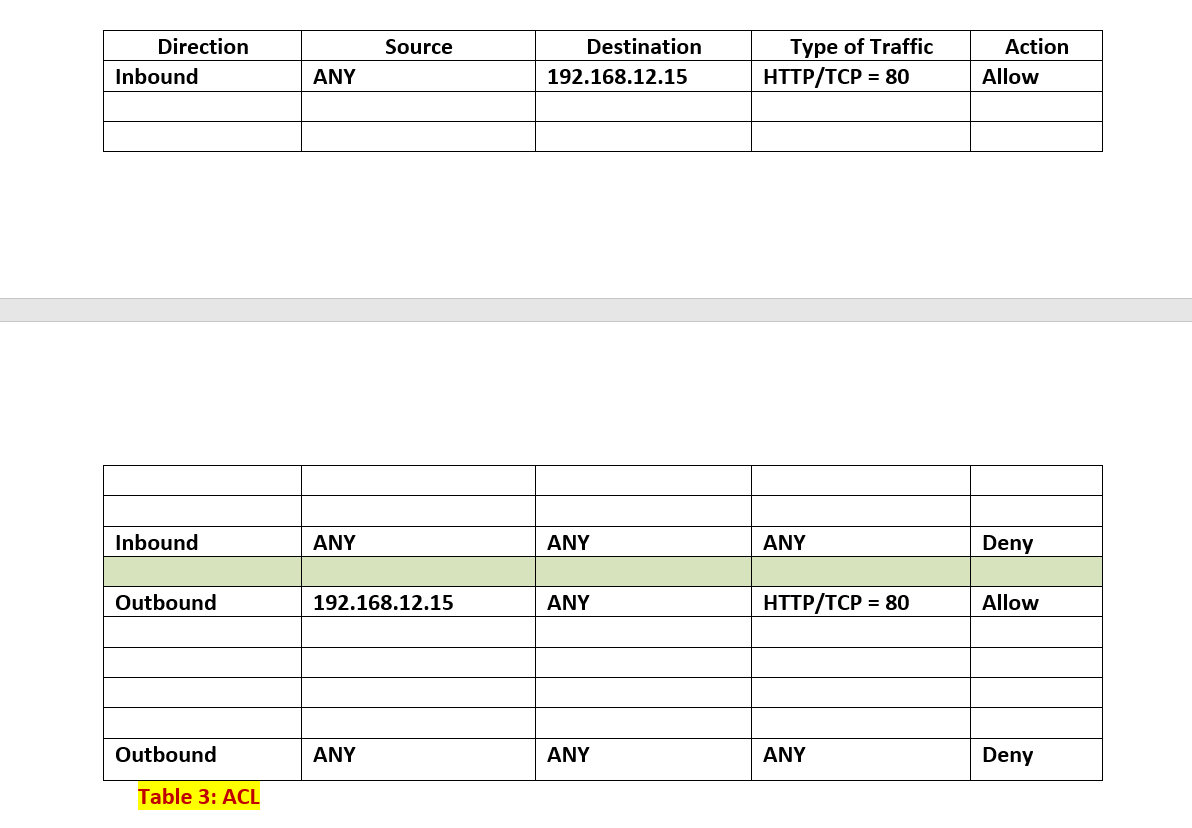
MS Windows 2016 Active Directory/File Mgmt & Accounts Store 192.168.12.11/27 10 Sales/Mkting Switch 2 SW2 Switch 3 SW3 MS Windows 2016 Terminal Services MS Windows 2016 Exchange Server Switch 4 SW4 192.168.12.12/27 Subneto subnet1 subnet2 192.168.12.13/27 subnet3 MS Windows 2016 SQL Server 192.168.12.14/27 Switch 1 SW1 MS Windows 2016-IIS Webserver subneto FW internall Interface HHH Must Assign Firewall 192.168.12.15/27 Interface Firewall Ext. Interfac 220.51.79.1/28 Email Gateway Spam Filter 220.51.79.15/28 Telecommuter Mobile Worker Customers Users Design by Myan
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


