Question: Modify the authentication protocol in Figure 9.12 so that it uses a hash function instead of symmetric key encryption. The resulting protocol must be secure.
Modify the authentication protocol in Figure 9.12 so that it uses a hash function instead of symmetric key encryption. The resulting protocol must be secure.
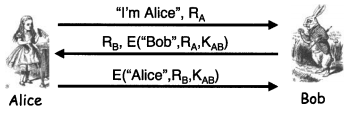
.IS this right?: RB, E(h(msgs,CLNT,KAB))
please answer with the syntax above. Not a picture explaining the process, I get the process. Thanks!
I'm Alice", RA RB, E("Bob",RA,KAB E("Alice",RB,KAB) Alice Bob I'm Alice", RA RB, E("Bob",RA,KAB E("Alice",RB,KAB) Alice Bob
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


