Question: NCA ECC - 1-2018 Domain # 1: Cyber Security Goveranance Total Implementation of CSC #1 1.1.2 A roadmap must be executed to implement the cybersecurity
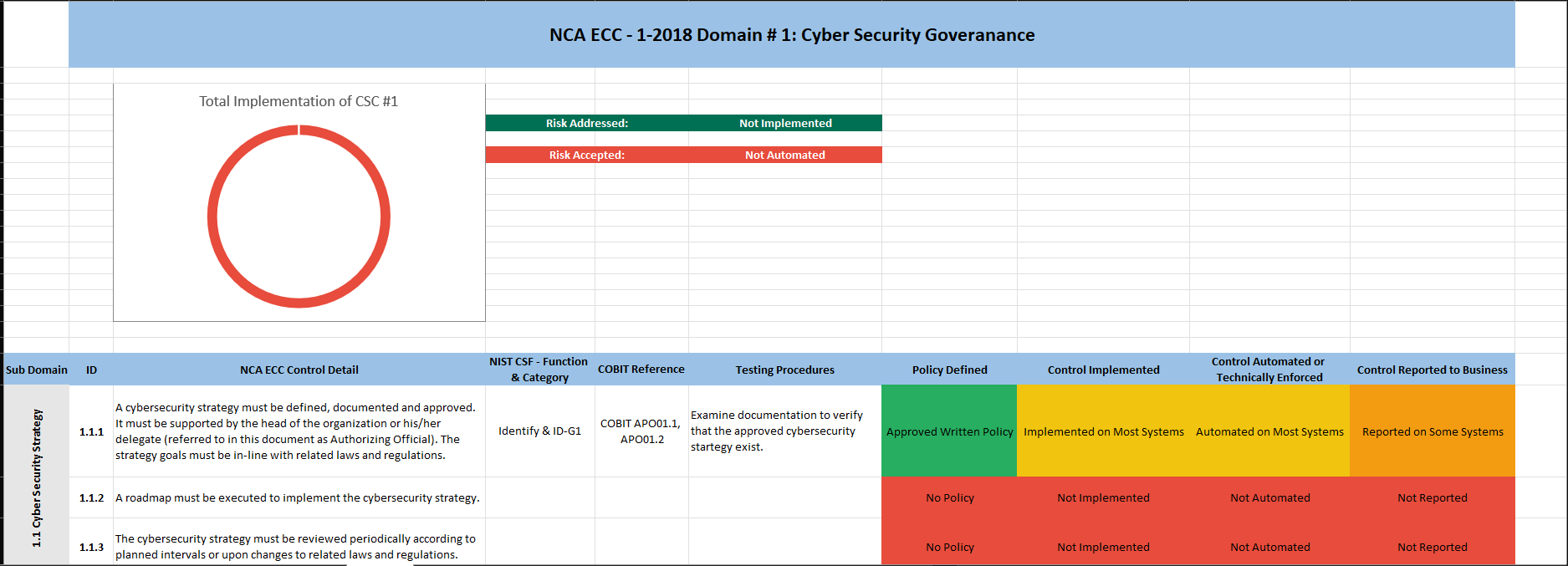
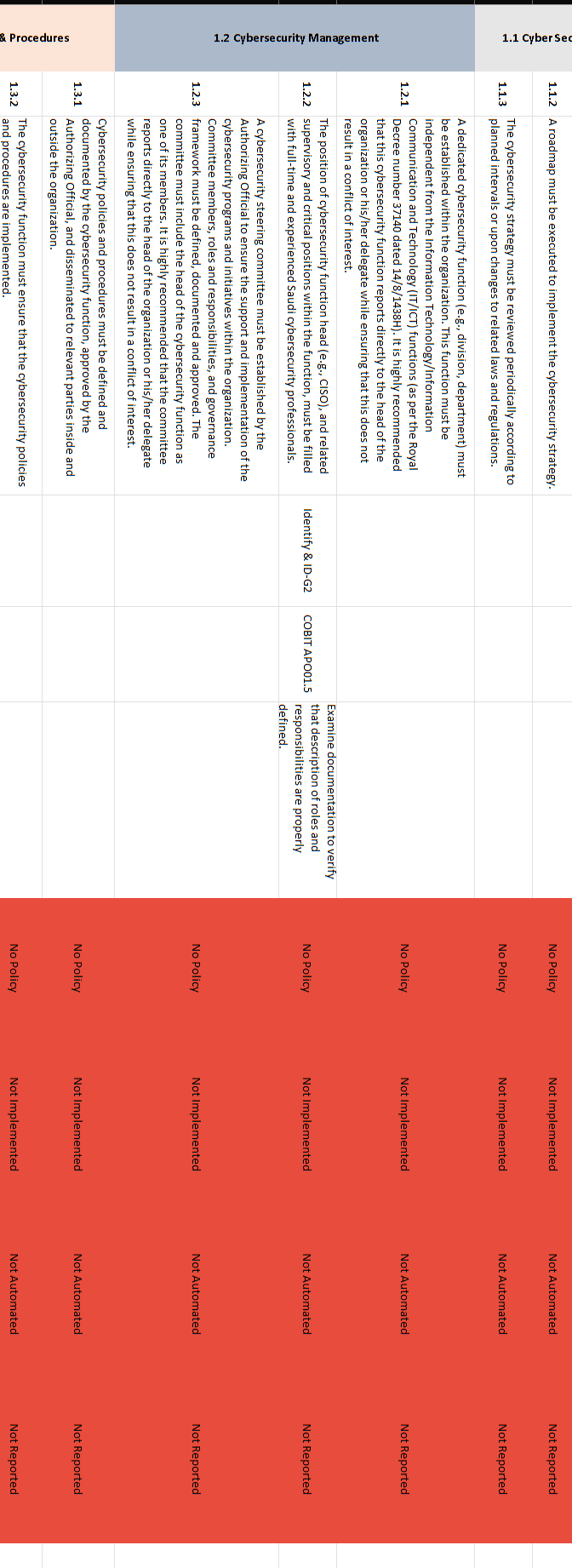
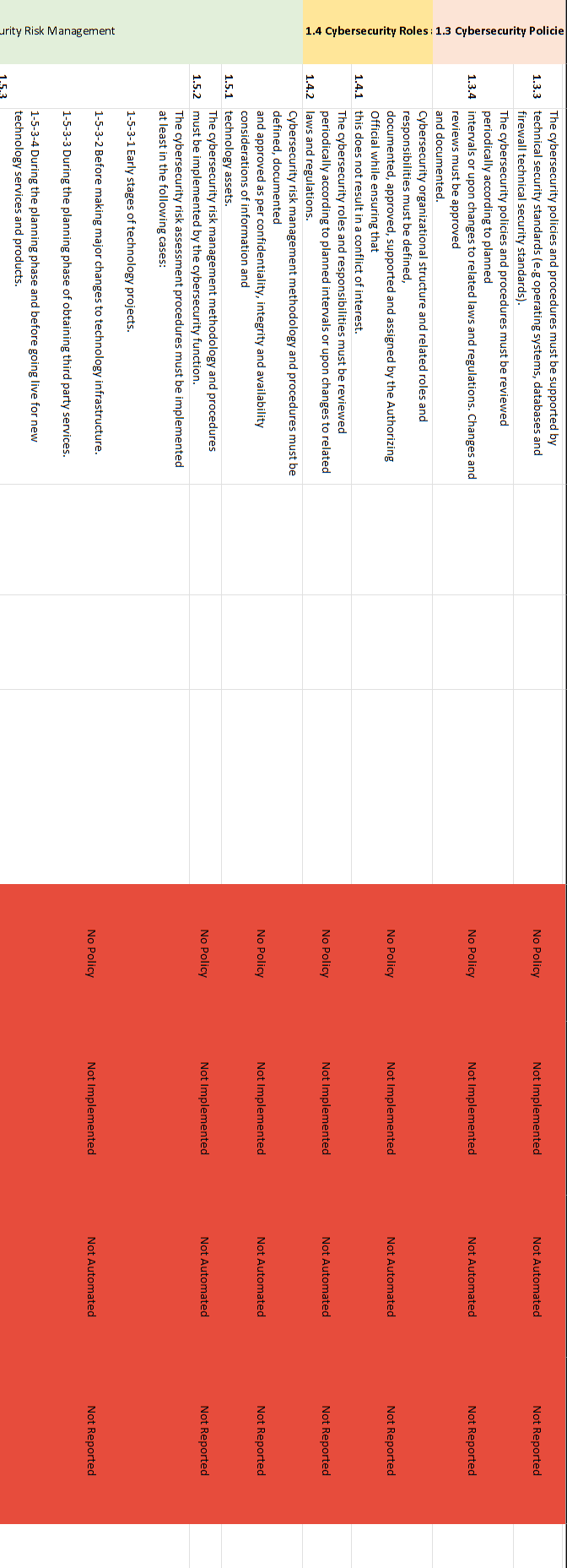
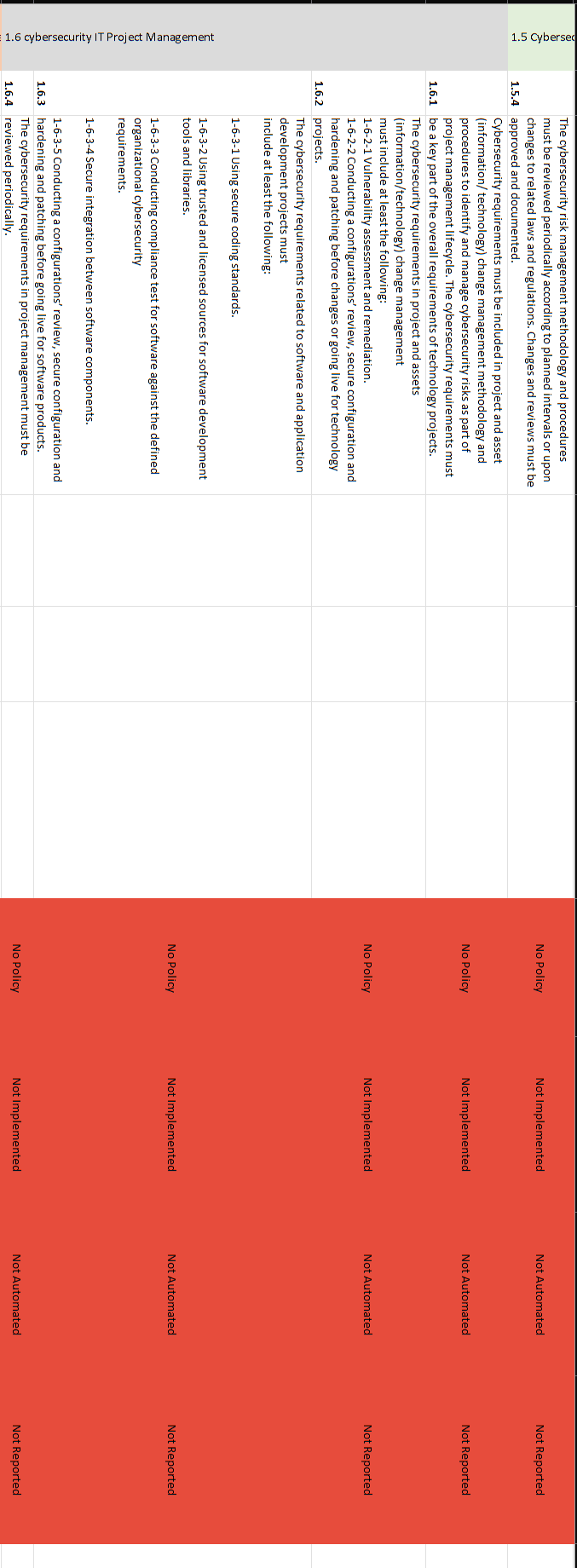
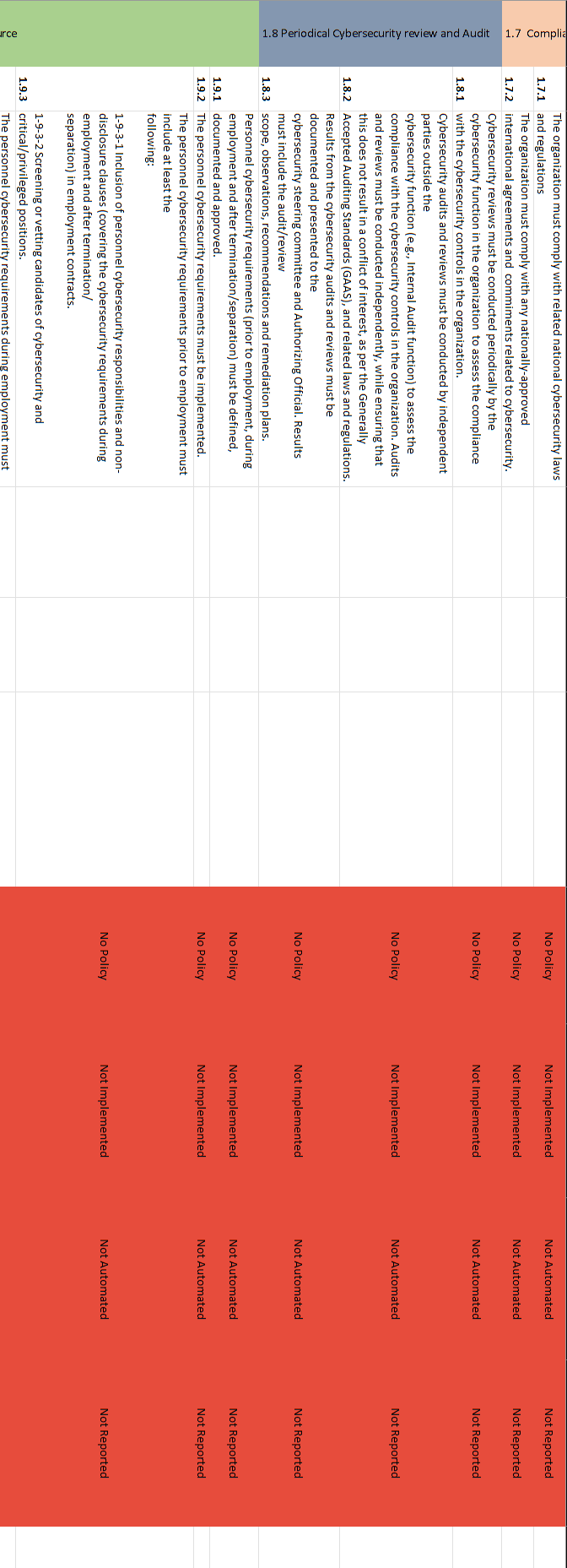
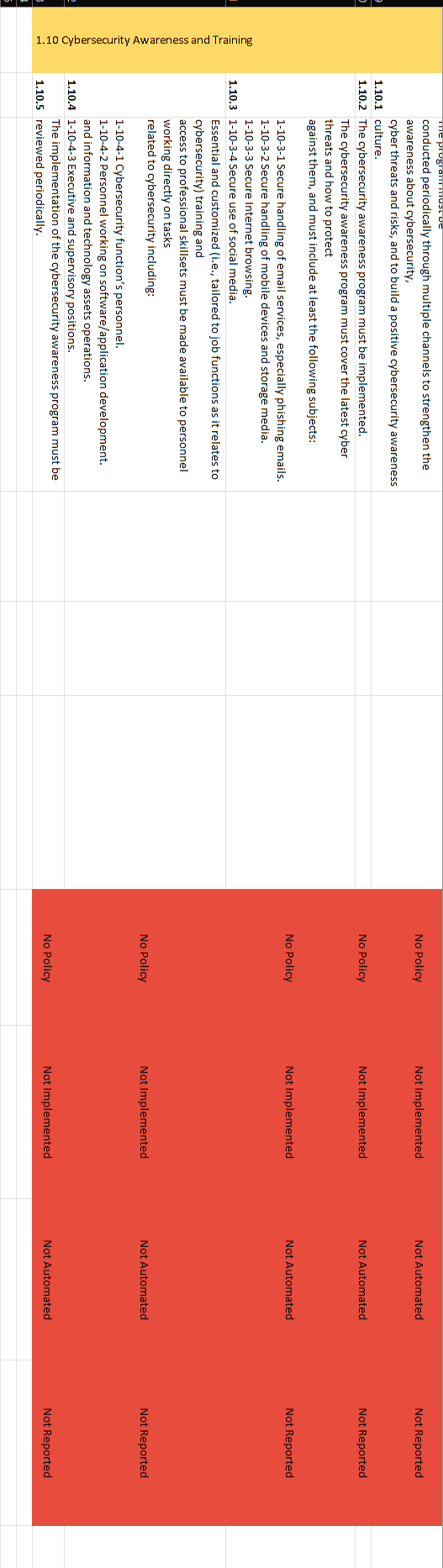
NCA ECC - 1-2018 Domain \# 1: Cyber Security Goveranance Total Implementation of CSC \#1 1.1.2 A roadmap must be executed to implement the cybersecurity strategy. 1.1.3 The cybersecurity strategy must be reviewed periodically according to planned intervals or upon changes to related laws and regulations. A dedicated cybersecurity function (e.g., division, department) must be established within the organization. This function must be independent from the Information Technology/Information 1.2.1 Communication and Technology (IT/ICT) functions (as per the Royal Decree number 37140 dated 14/8/1438H ). It is highly recommended that this cybersecurity function reports directly to the head of the organization or his/her delegate while ensuring that this does not result in a conflict of interest. The position of cybersecurity function head (e.g., CISO), and related Examine documentation to verify 1.2.2 supervisory and critical positions within the function, must be filled that description of roles and with full-time and experienced Saudi cybersecurity professionals. responsibilities are properly defined. A cybersecurity steering committee must be established by the Authorizing Official to ensure the support and implementation of the cybersecurity programs and initiatives within the organization. Committee members, roles and responsibilities, and governance 1.2.3 framework must be defined, documented and approved. The committee must include the head of the cybersecurity function as one of its members. It is highly recommended that the committee reports directly to the head of the organization or his/her delegate while ensuring that this does not result in a conflict of interest. Cybersecurity policies and procedures must be defined and 1.3.1 documented by the cybersecurity function, approved by the Authorizing Official, and disseminated to relevant parties inside and outside the organization. 1.3.2 The cybersecurity function must ensure that the cybersecurity policies and procedures are implemented. The cybersecurity risk management methodology and procedures must be reviewed periodically according to planned intervals or upon changes to related laws and regulations. Changes and reviews must be 1.5.4 approved and documented. Cybersecurity requirements must be included in project and asset (information/ technology) change management methodology and procedures to identify and manage cybersecurity risks as part of project management lifecycle. The cybersecurity requirements must 1.6.1 be a key part of the overall requirements of technology projects. The cybersecurity requirements in project and assets (information/technology) change management must include at least the following: 1-6-2-1 Vulnerability assessment and remediation. 1-6-2-2 Conducting a configurations' review, secure configuration and hardening and patching before changes or going live for technology 1.6.2 projects. The cybersecurity requirements related to software and application development projects must include at least the following: 1-6-3-1 Using secure coding standards. 1-6-3-2 Using trusted and licensed sources for software development tools and libraries. 1-6-3-3 Conducting compliance test for software against the defined organizational cybersecurity requirements. 1-6-3-4 Secure integration between software components. 1-6-3-5 Conducting a configurations' review, secure configuration and 1.6.3 hardening and patching before going live for software products. The cybersecurity requirements in project management must be The organization must comply with related national cybersecurity laws 1.7.1 and regulations The organization must comply with any nationally-approved 1.7.2 international agreements and commiments related to cybersecurity. Cybersecurity reviews must be conducted periodically by the cybersecurity function in the organization to assess the compliance 1.8.1 with the cybersecurity controls in the organization. Cybersecurity audits and reviews must be conducted by independent parties outside the cybersecurity function (e.g., Internal Audit function) to assess the compliance with the cybersecurity controls in the organization. Audits and reviews must be conducted independently, while ensuring that this does not result in a conflict of interest, as per the Generally 1.8.2 Accepted Auditing Standards (GAAS), and related laws and regulations. Results from the cybersecurity audits and reviews must be documented and presented to the cybersecurity steering committee and Authorizing Official. Results must include the audit/review 1.8.3 scope, observations, recommendations and remediation plans. Personnel cybersecurity requirements (prior to employment, during employment and after termination/separation) must be defined, 1.9.1 documented and approved. 1.9.2 The personnel cybersecurity requirements must be implemented. The personnel cybersecurity requirements prior to employment must include at least the following: 1-9-3-1 Inclusion of personnel cybersecurity responsibilities and nondisclosure clauses (covering the cybersecurity requirements during employment and after termination/ separation) in employment contracts. 1-9-3-2 Screening or vetting candidates of cybersecurity and 1.9.3 critical/privileged positions
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


