Question: #Network Security You are given a case study of a software development company to explore the security mechanisms and the security measures used in the
#Network Security
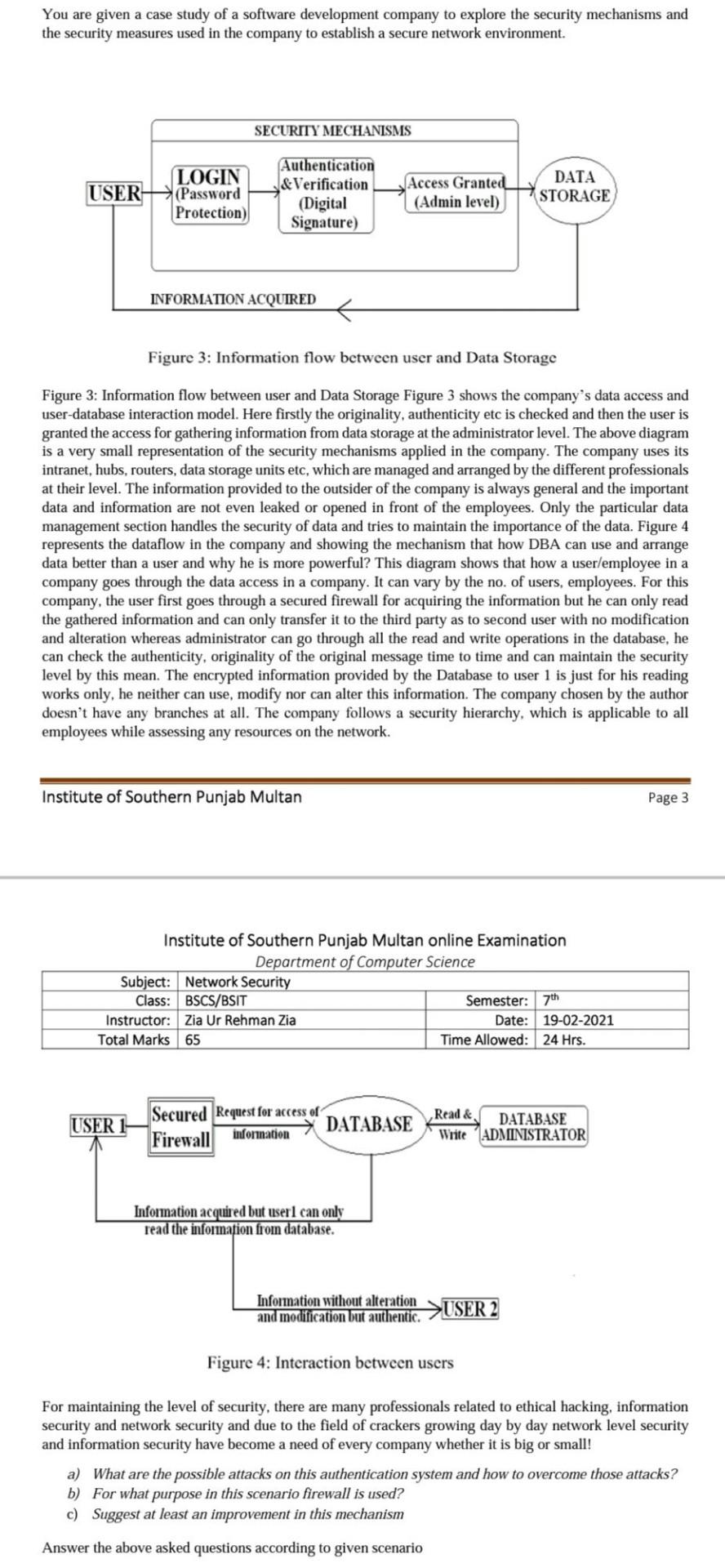
You are given a case study of a software development company to explore the security mechanisms and the security measures used in the company to establish a secure network environment. SECURITY MECHANISMS USER LOGIN (Password Protection) Authentication &Verification (Digital Signature) Access Granted (Admin level) DATA STORAGE INFORMATION ACQUIRED Figure 3: Information flow between user and Data Storage Figure 3: Information flow between user and Data Storage Figure 3 shows the company's data access and user-database interaction model. Here firstly the originality, authenticity etc is checked and then the user is granted the access for gathering information from data storage at the administrator level. The above diagram is a very small representation of the security mechanisms applied in the company. The company uses its intranet, hubs, routers, data storage units etc, which are managed and arranged by the different professionals at their level. The information provided to the outsider of the company is always general and the important data and information are not even leaked or opened in front of the employees. Only the particular data management section handles the security of data and tries to maintain the importance of the data. Figure 4 represents the dataflow in the company and showing the mechanism that how DBA can use and arrange data better than a user and why he is more powerful? This diagram shows that how a user/employee in a company goes through the data access in a company. It can vary by the no. of users, employees. For this company, the user first goes through a secured firewall for acquiring the information but he can only read the gathered information and can only transfer it to the third party as to second user with no modification and alteration whereas administrator can go through all the read and write operations in the database, he can check the authenticity, originality of the original message time to time and can maintain the security level by this mean. The encrypted information provided by the Database to user 1 is just for his reading works only, he neither can use, modify nor can alter this information. The company chosen by the author doesn't have branches at all. The company follows a security hier which is applicable to all employees while assessing any resources on the network. Institute of Southern Punjab Multan Page 3 Institute of Southern Punjab Multan online Examination Department of Computer Science Subject: Network Security Class: BSCS/BSIT Semester: 7th Instructor: Zia Ur Rehman Zia Date: 19-02-2021 Total Marks 65 Time Allowed: 24 Hrs. USER Secured Request for access of DATABASE Firewall information Read & DATABASE Write ADMINISTRATOR Information acquired but user can only read the information from database. Information without alteration and modification but authentic USER Figure 4: Interaction between users For maintaining the level of security, there are many professionals related to ethical hacking, information security and network security and due to the field of crackers growing day by day network level security and information security have become a need of every company whether it is big or small! a) What are the possible attacks on this authentication system and how to overcome those attacks? b) For what purpose in this scenario firewall is used? c) Suggest at least an improvement in this mechanism Answer the above asked questions according to given scenario
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


