Question: Now that you can encypt and decypt messages using the easier methods, you are ready to work on code for your third message and make
Now that you can encypt and decypt messages using the easier methods, you are ready to work on code for your third message and make encypition method See the overview section for description, equation and examples.
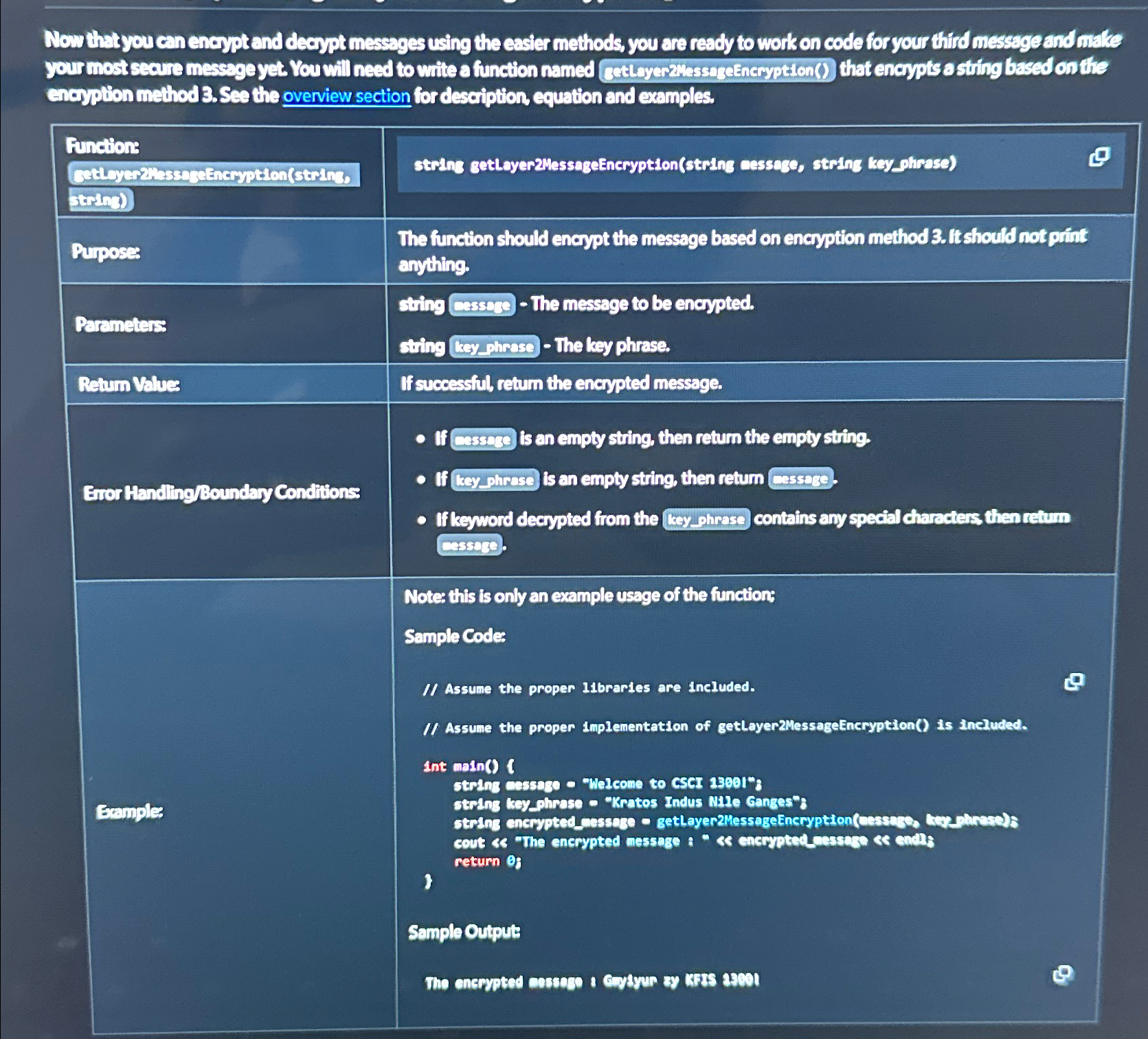
tablestring getloyerMessageEncryptionstring cessaze, string keyphrasePuposestableThe function should encypt the message based on encyption method fit should not priftanythingParemeterstablesting cassebe The message to be encypted.sting lay phrese The ksy phrase.Retum Values,If succeasiol, retum the encrypted message.Euorthanding Bounday Conditions,Exuples
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


