Question: Our text did discuss Security & Information Event Management (SIEM) to a degree, what they did not include is why these types of solutions are
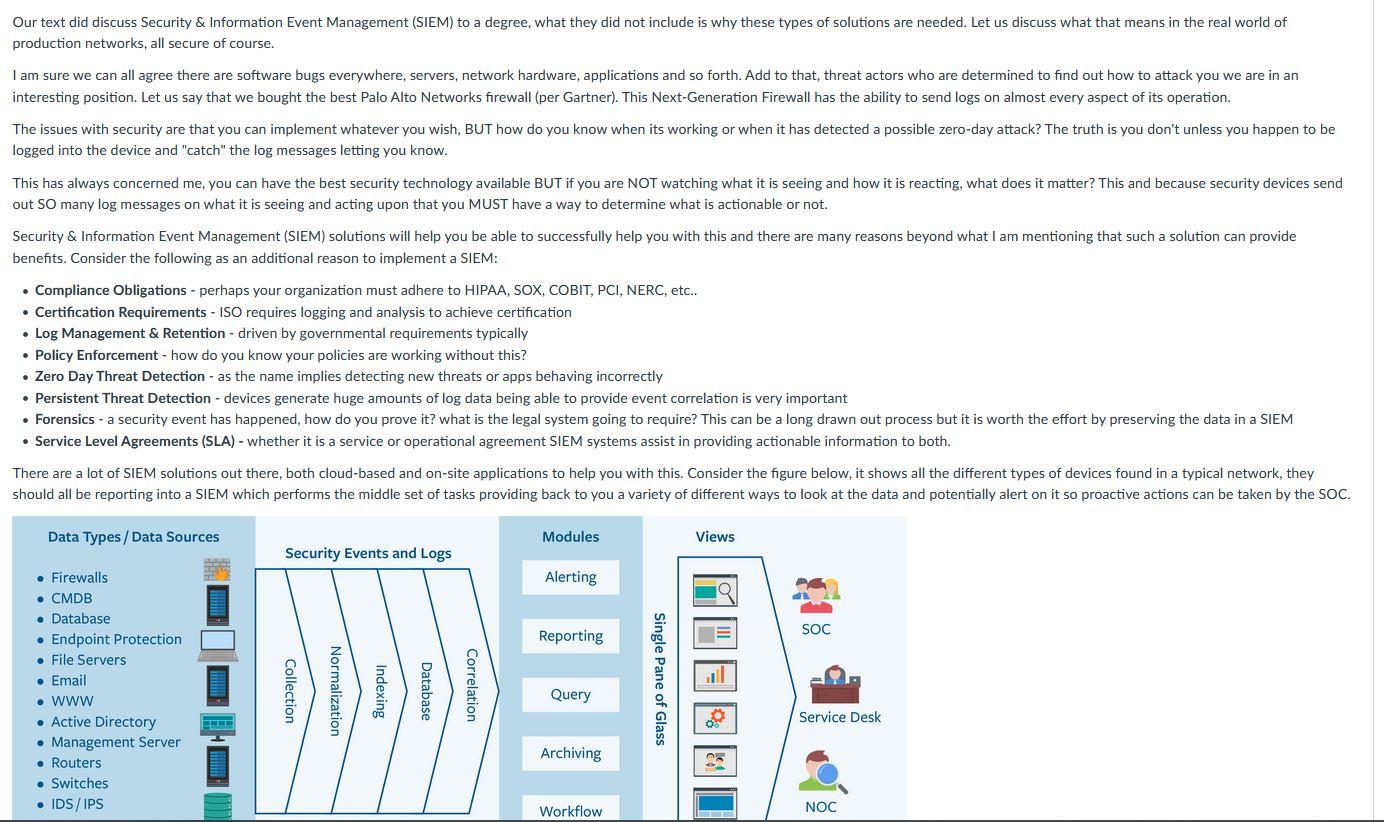
Our text did discuss Security & Information Event Management (SIEM) to a degree, what they did not include is why these types of solutions are needed. Let us discuss what that means in the real world of production networks, all secure of course. I am sure we can all agree there are software bugs everywhere, servers, network hardware, applications and so forth. Add to that, threat actors who are determined to find out how to attack you we are in an interesting position. Let us say that we bought the best Palo Alto Networks firewall (per Gartner). This Next-Generation Firewall has the ability to send logs on almost every aspect of its operation. The issues with security are that you can implement whatever you wish, BUT how do you know when its working or when it has detected a possible zero-day attack? The truth is you don't unless you happen to be logged into the device and "catch" the log messages letting you know. This has always concerned me, you can have the best security technology available BUT if you are NOT watching what it is seeing and how it is reacting, what does it matter? This and because security devices send out SO many log messages on what it is seeing and acting upon that you MUST have a way to determine what is actionable or not. Security & Information Event Management (SIEM) solutions will help you be able to successfully help you with this and there are many reasons beyond what I am mentioning that such a solution can provide benefits. Consider the following as an additional reason to implement a SIEM: Compliance Obligations - perhaps your organization must adhere to HIPAA, SOX, COBIT, PCI, NERC, etc.. Certification Requirements - ISO requires logging and analysis to achieve certification Log Management & Retention - driven by governmental requirements typically Policy Enforcement - how do you know your policies are working without this? Zero Day Threat Detection - as the name implies detecting new threats or apps behaving incorrectly Persistent Threat Detection - devices generate huge amounts of log data being able to provide event correlation is very important Forensics - a security event has happened, how do you prove it? what is the legal system going to require? This can be a long drawn out process but it is worth the effort by preserving the data in a SIEM Service Level Agreements (SLA) - whether it is a service or operational agreement SIEM systems assist in providing actionable information to both. There are a lot of SIEM solutions out there, both cloud-based and on-site applications to help you with this. Consider the figure below, it shows all the different types of devices found in a typical network, they should all be reporting into a SIEM which performs the middle set of tasks providing back to you a variety of different ways to look at the data and potentially alert on it so proactive actions can be taken by the SOC. Data Types/Data Sources Modules Views Security Events and Logs Alerting Reporting SOC Firewalls CMDB Database Endpoint Protection File Servers Email . www Active Directory Management Server Routers Switches IDS/IPS THOME Collection Normalization Indexing Database Correlation Single Pane of Glass Query Service Desk Archiving Workflow NOC A few things to consider with any SIEM, do not let an engineer define the alerts without business input. These logs and the alerts from the SIEM as it does event correlation should be driven on how to protect the business. To many engineers think THEY know best, perhaps they do however they are employed by an organization and they must do their best to protect it. I find a great analogy here in that with SIEMs the more you learn the more you will know. That is really what is most important to a security professional, you have to know what is happening in order to respond it and as Dr. Seuss said: The more that you read, the more things you will know. The more that you learn, the more places youll go. . Dr. Seuss Discussion Scenario & Question Now that we have laid the groundwork and quoted a Doctor for this discussion lets get into the scenario that we will be discussing: You are tasked with analyzing a SIEM products and proposing one as the solution for your organization. The parameters you will be expected to support for SIEM are as follows: 1 firewall, 1 router, 4 switches, 10 servers and 8 different applications. You do not really know the amount of log traffic these devices will be sending to the SIEM. You will want the SIEM to be able to support custom alerts, monthly reports, and other security solutions that you are free to add. Perhaps this exercist relate back to your 9-5 job. At a minimum select 3 different SIEM solutions, compare and contrast them based on what we have learned in this module, To conclude the discussion make a recommendation for an SIEM solution with supporting information that describes why the solution was chosen. Tettone






