Question: Peter works as a cyber security analyst at a private equity firm. His colleagues at the firm have been inundated by a large number of
Peter works as a cyber security analyst at a private equity firm. His colleagues at the firm have been inundated by a large number of spam-emails. Peter has been asked to implement a spam detection system on the companys email server. He reviewed a sample of 500 spam and legitimate emails with relevant variables: spam (1 if it is spam message, 0 otherwise), the number of recipients of the message, the number of hyperlinks, and the number of characters in the message. The dataset is stored in the file Spam_Data.xlsx.
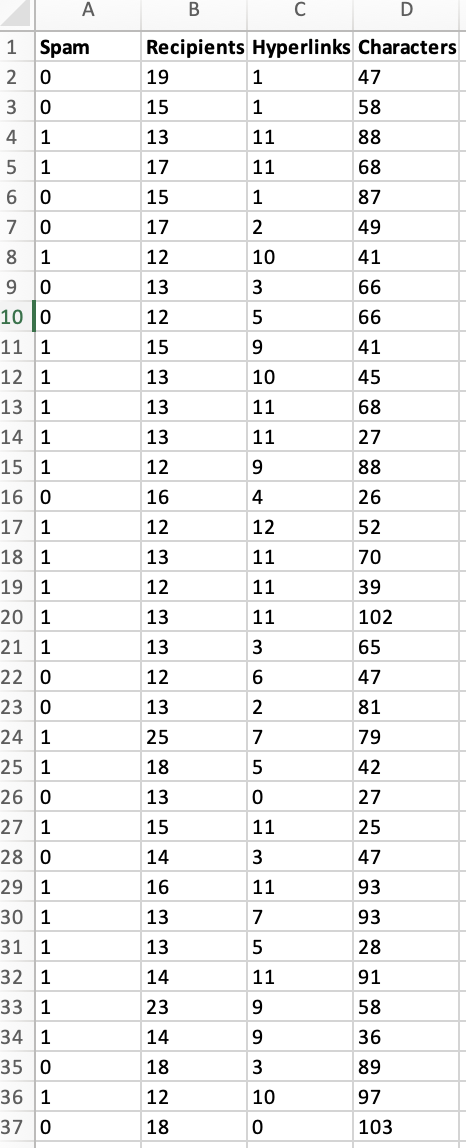
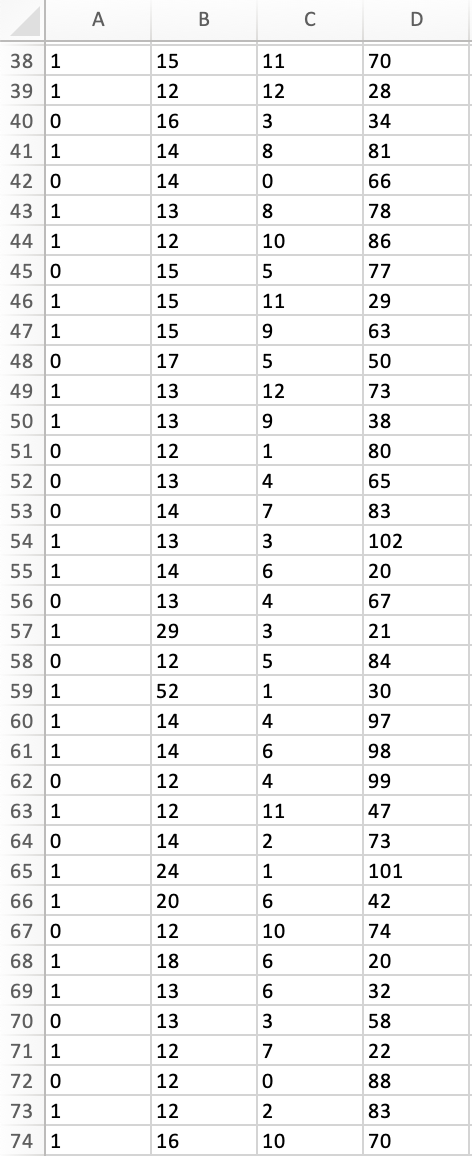
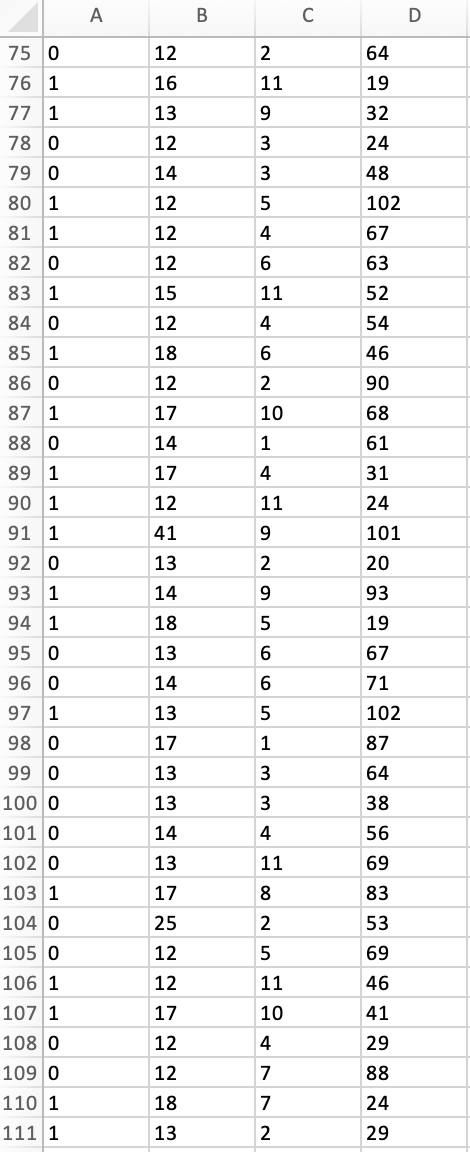
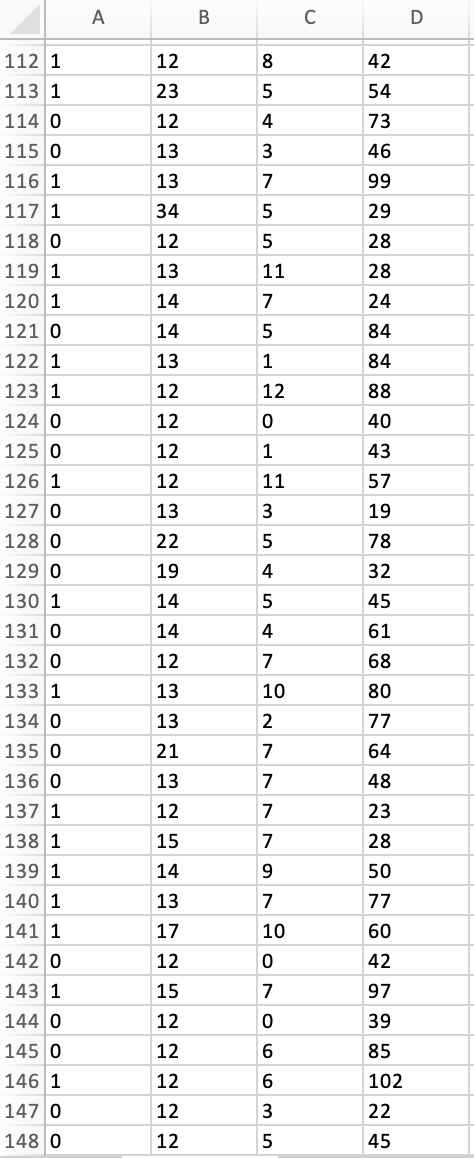
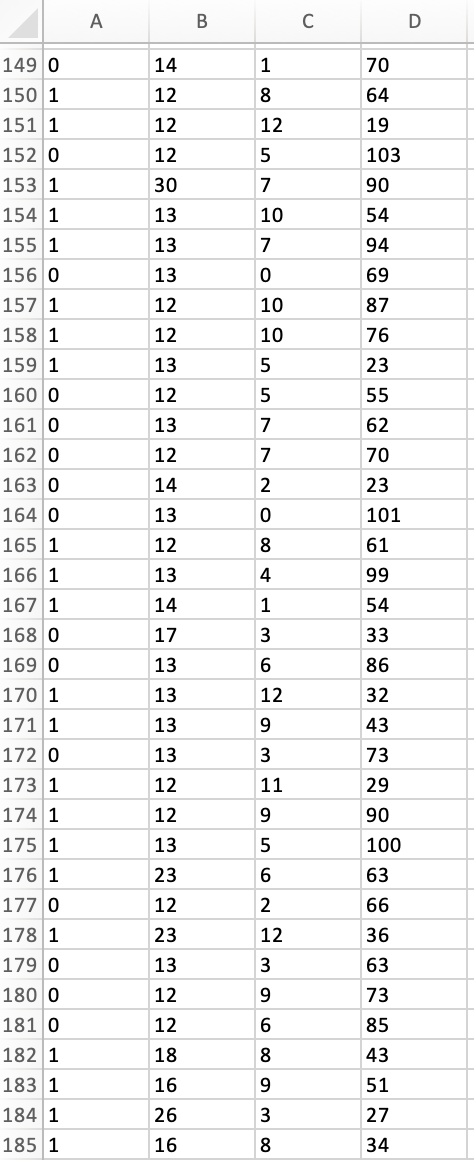
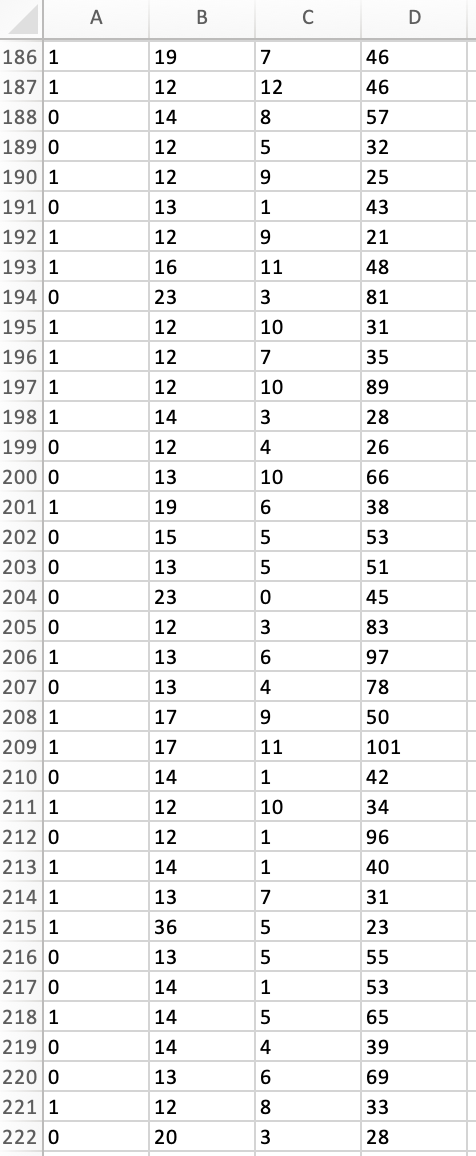
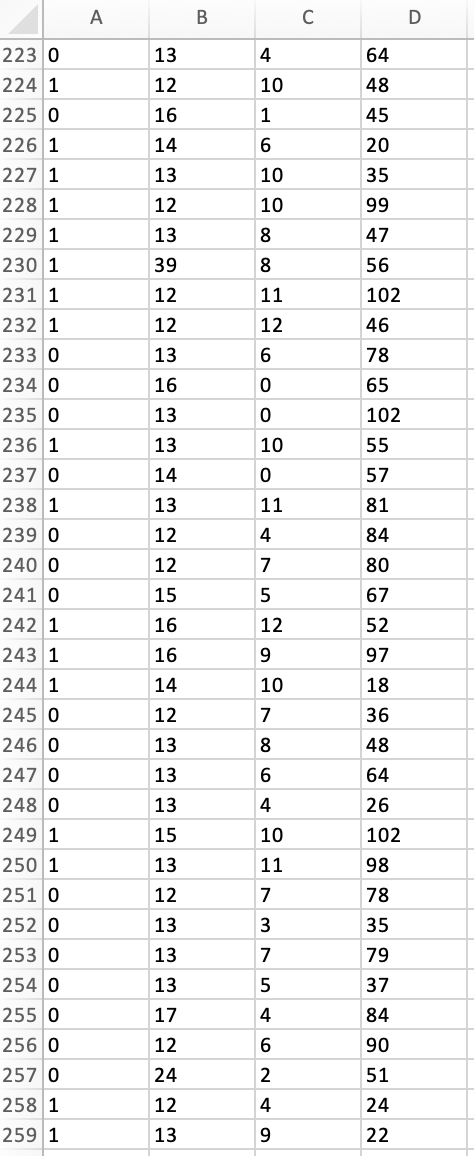
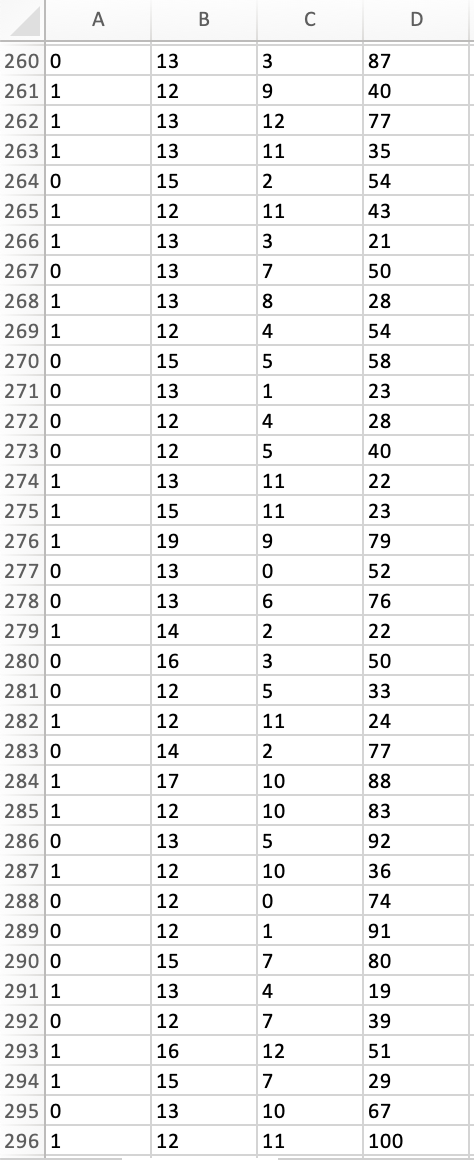
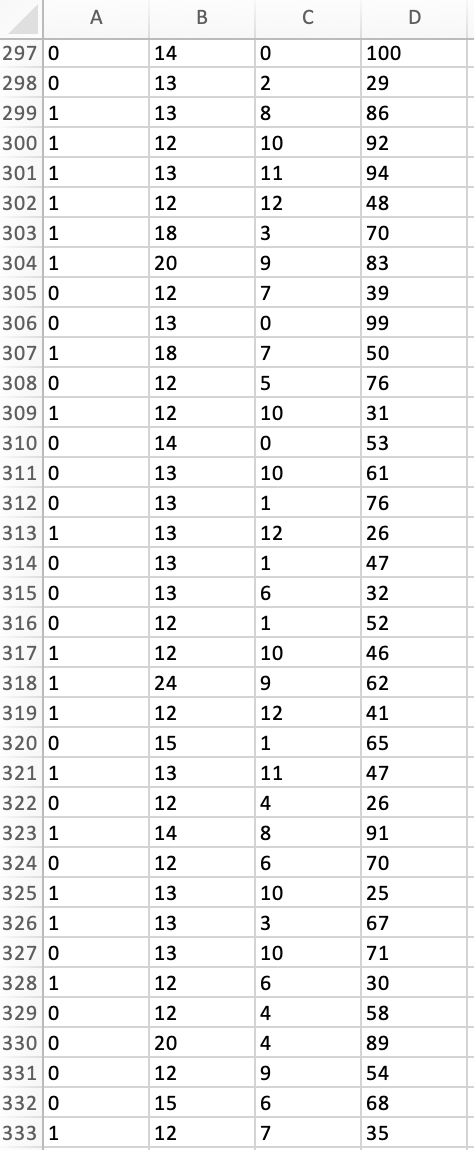
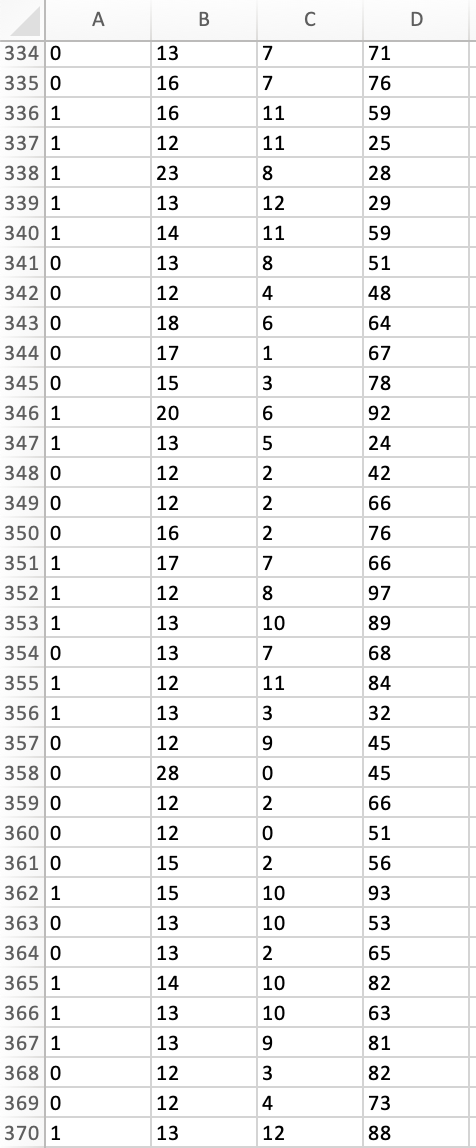
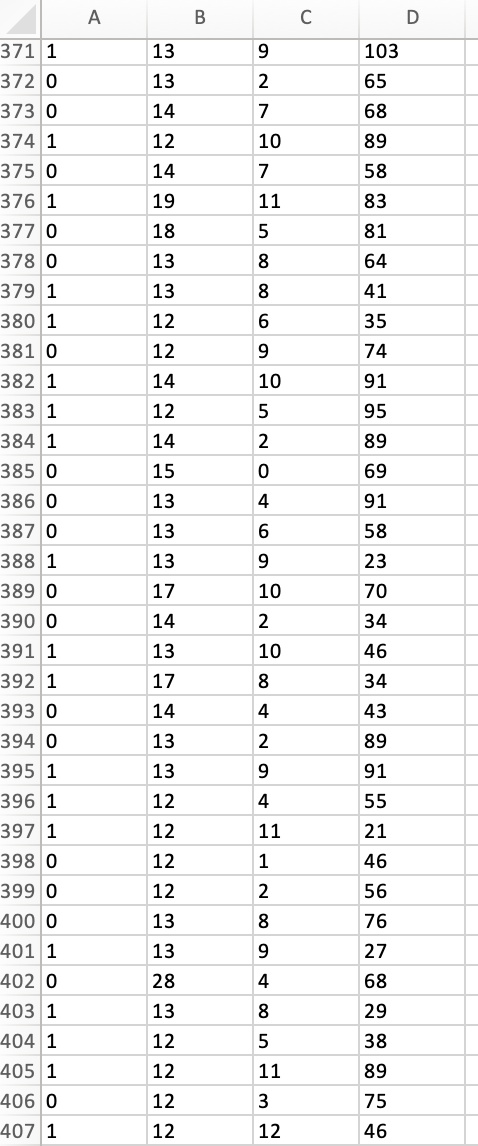
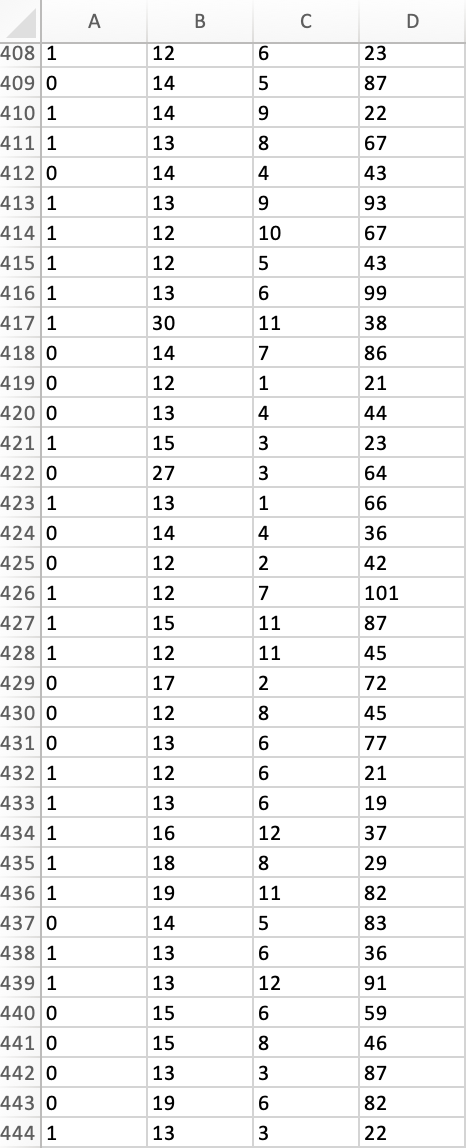
1. Perform a KNN analysis to estimate a classification model for spam detection using the steps we had seen in class. Based on the fitted (trained) data output, what is the optimal value of k?
2. Report the accuracy, specificity, sensitivity, and precision for the validation data set.
THIS HAS TO BE DONE IN R & RSTUDIO PROGRAMMING LANGUAGE!
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


