Question: Please ans all question for thumbs up. What is a disadvantage of using a leased line instead of a packet switched network to connect two
 Please ans all question for thumbs up.
Please ans all question for thumbs up.
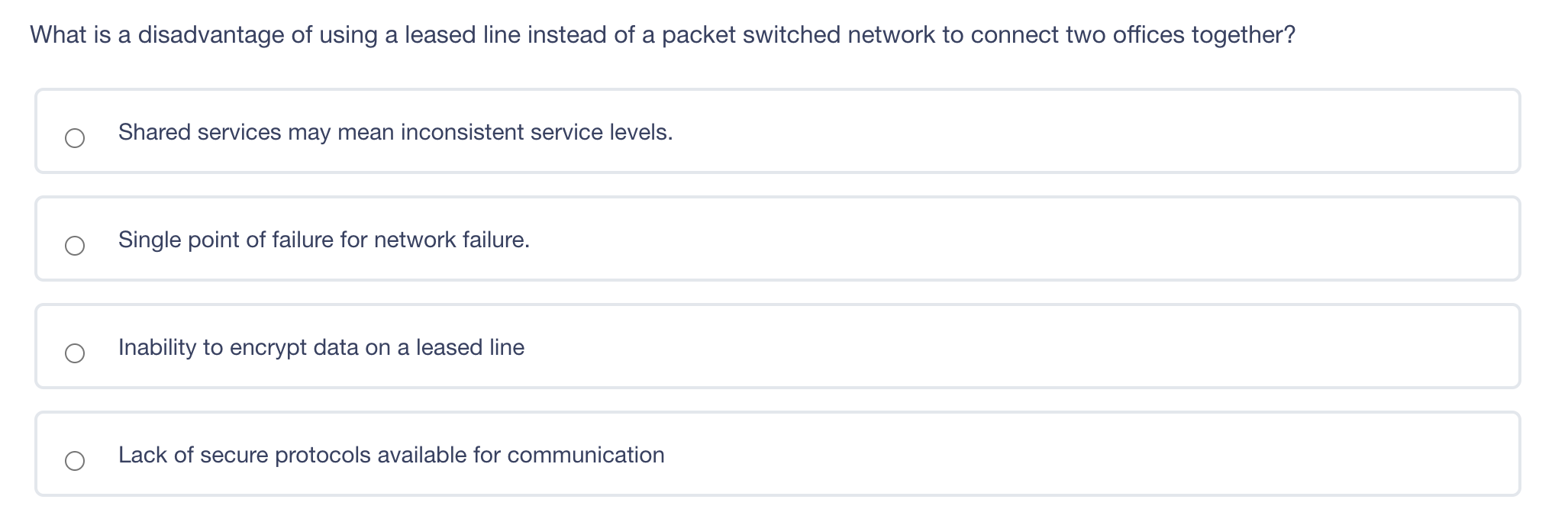
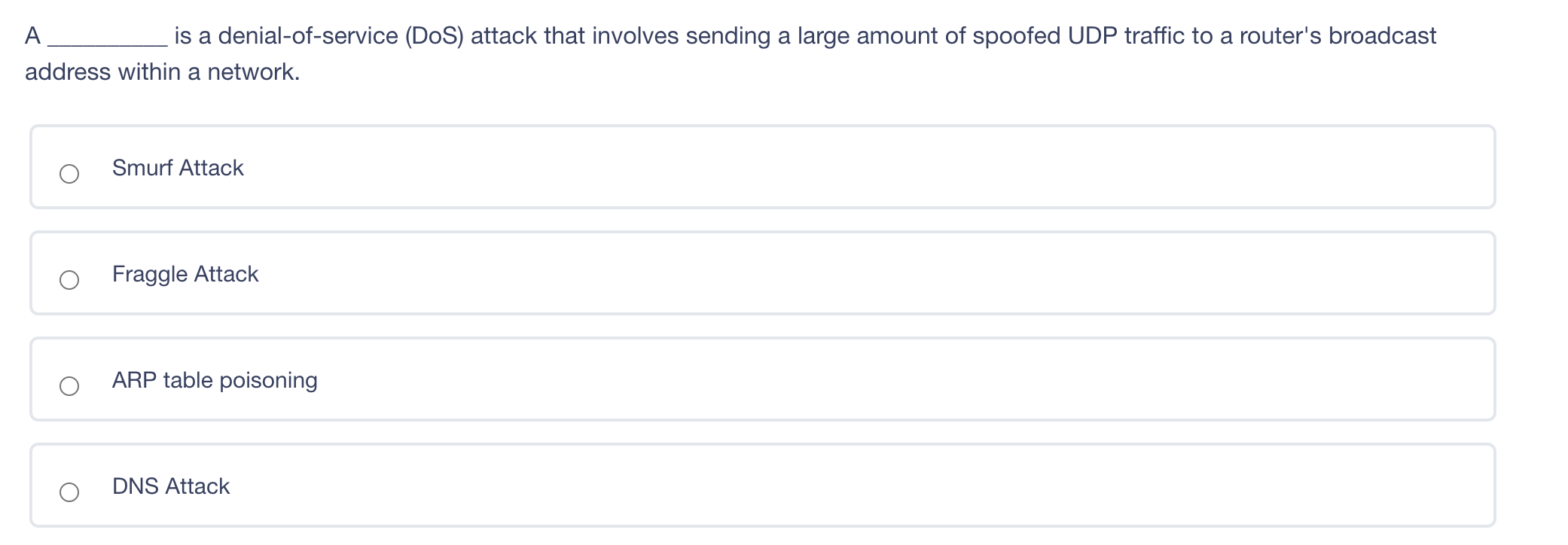
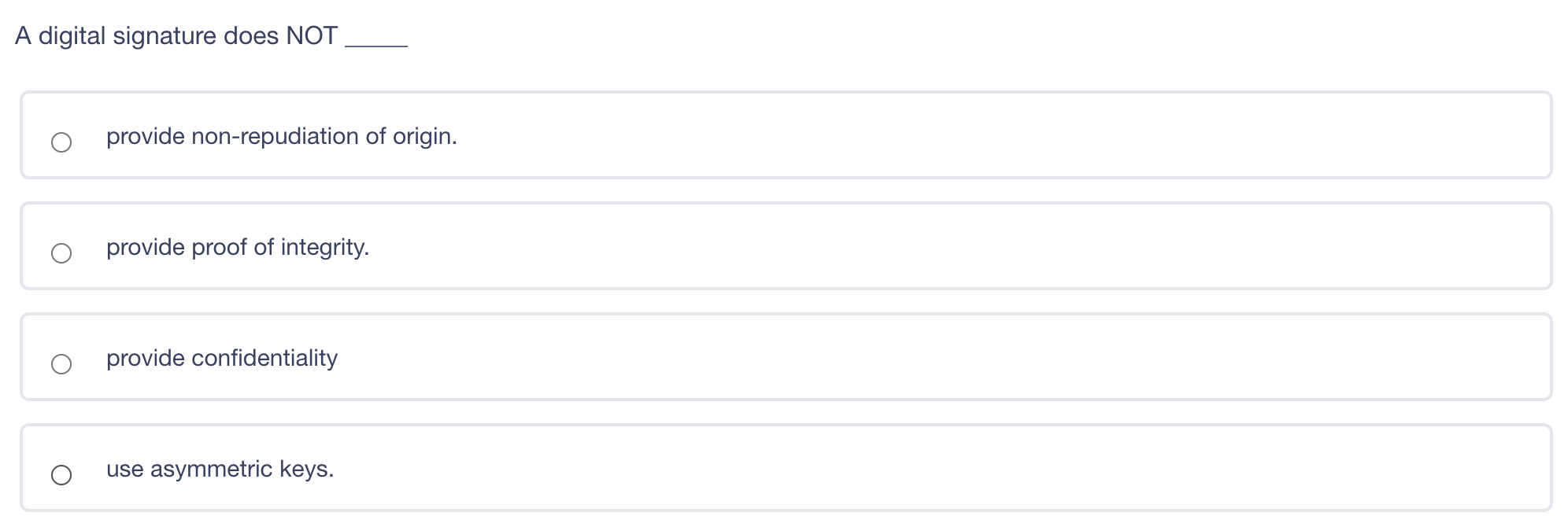
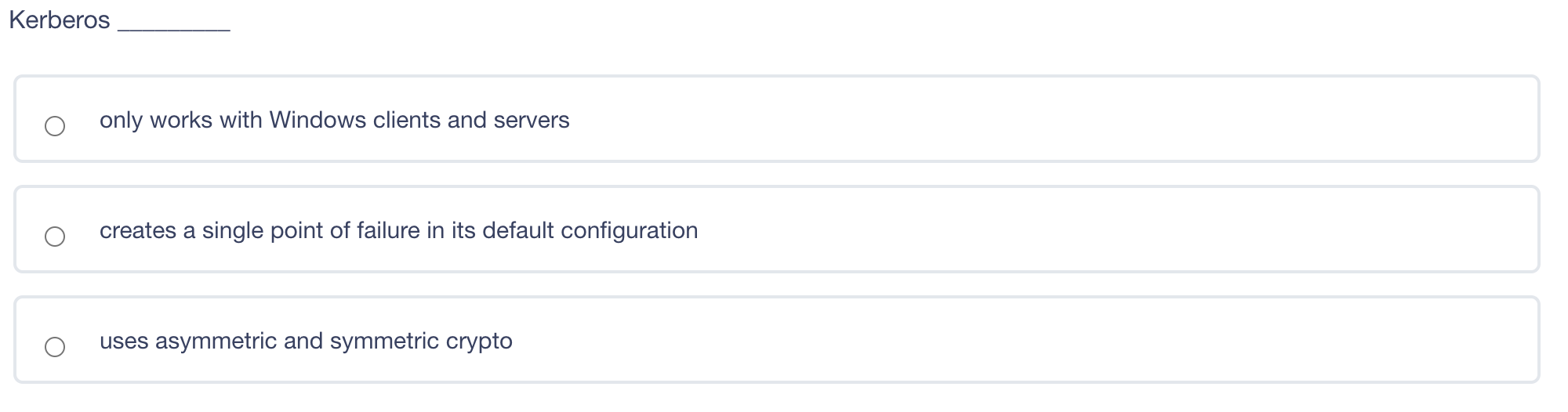
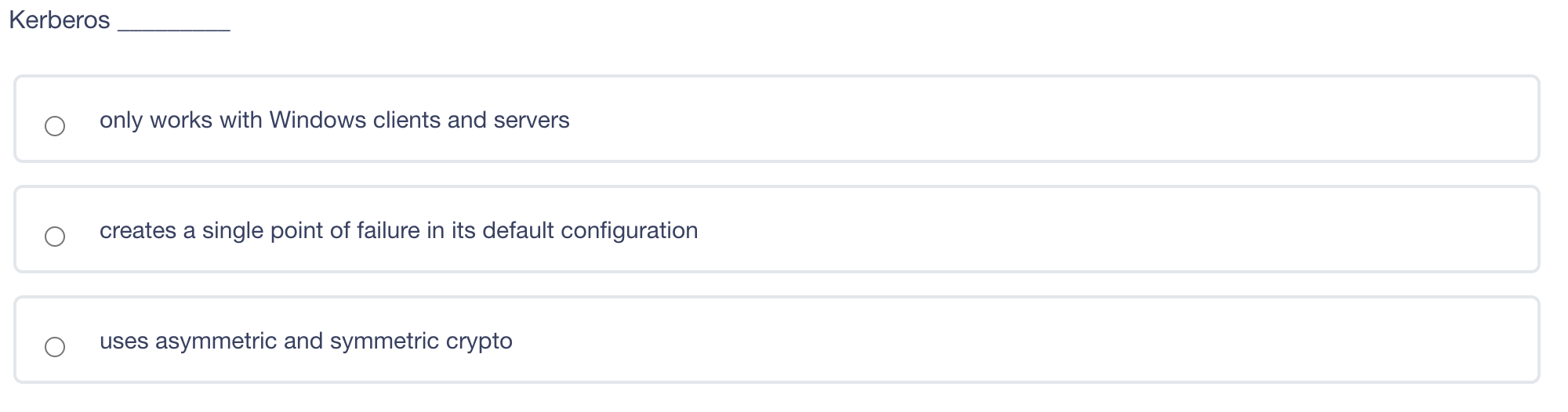
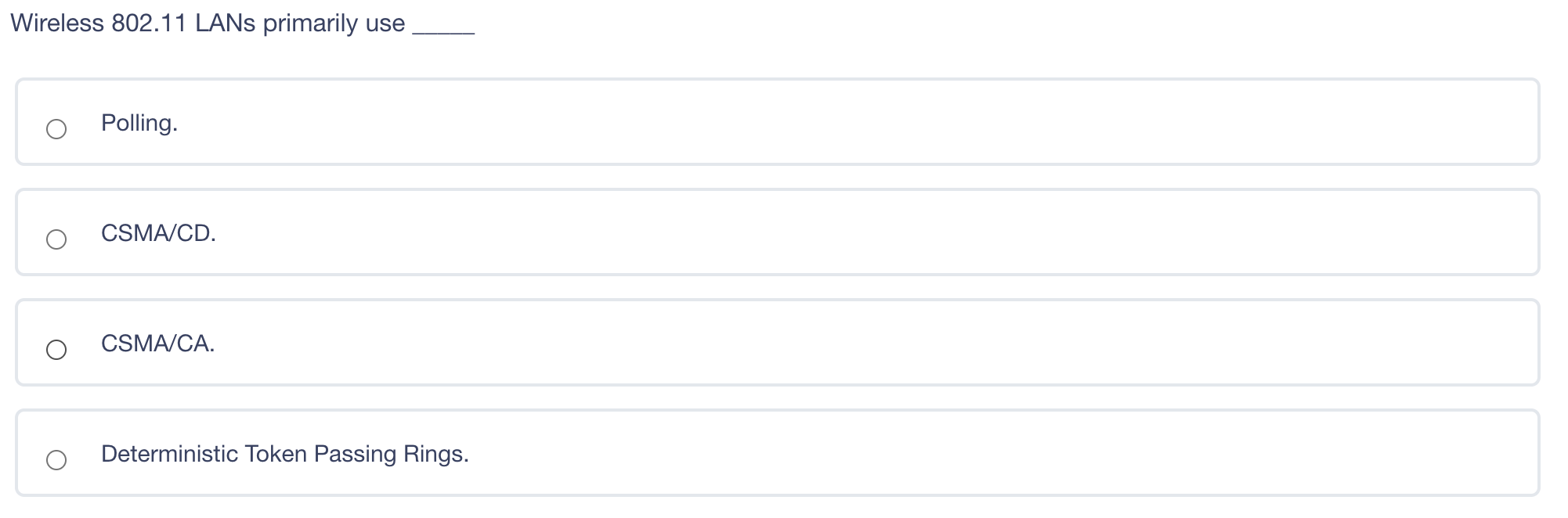
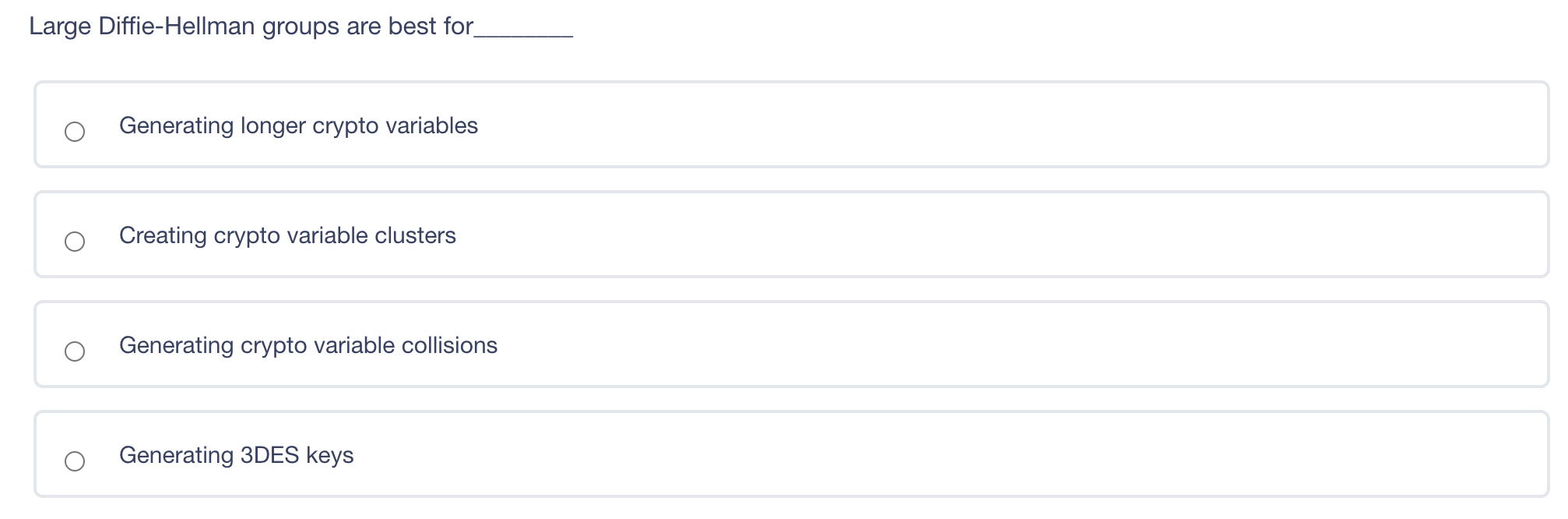
What is a disadvantage of using a leased line instead of a packet switched network to connect two offices together? Shared services may mean inconsistent service levels. Single point of failure for network failure. Inability to encrypt data on a leased line Lack of secure protocols available for communication A is a denial-of-service (DoS) attack that involves sending a large amount of spoofed UDP traffic to a router's broadcast address within a network. Smurf Attack Fraggle Attack ARP table poisoning DNS Attack A digital signature does NOT provide non-repudiation of origin. provide proof of integrity. provide confidentiality use asymmetric keys. Kerberos only works with Windows clients and servers creates a single point of failure in its default configuration uses asymmetric and symmetric crypto Kerberos only works with Windows clients and servers creates a single point of failure in its default configuration uses asymmetric and symmetric crypto Wireless 802.11 LANs primarily use Polling. CSMA/CD. CSMA/CA. Deterministic Token Passing Rings. Large Diffie-Hellman groups are best for Generating longer crypto variables Creating crypto variable clusters Generating crypto variable collisions Generating 3DES keys
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


