Question: Please ANSWER all question for thumbs up. Please ANSWER all question for thumbs up. Which of the following should be used to stop a determined
Please ANSWER all question for thumbs up.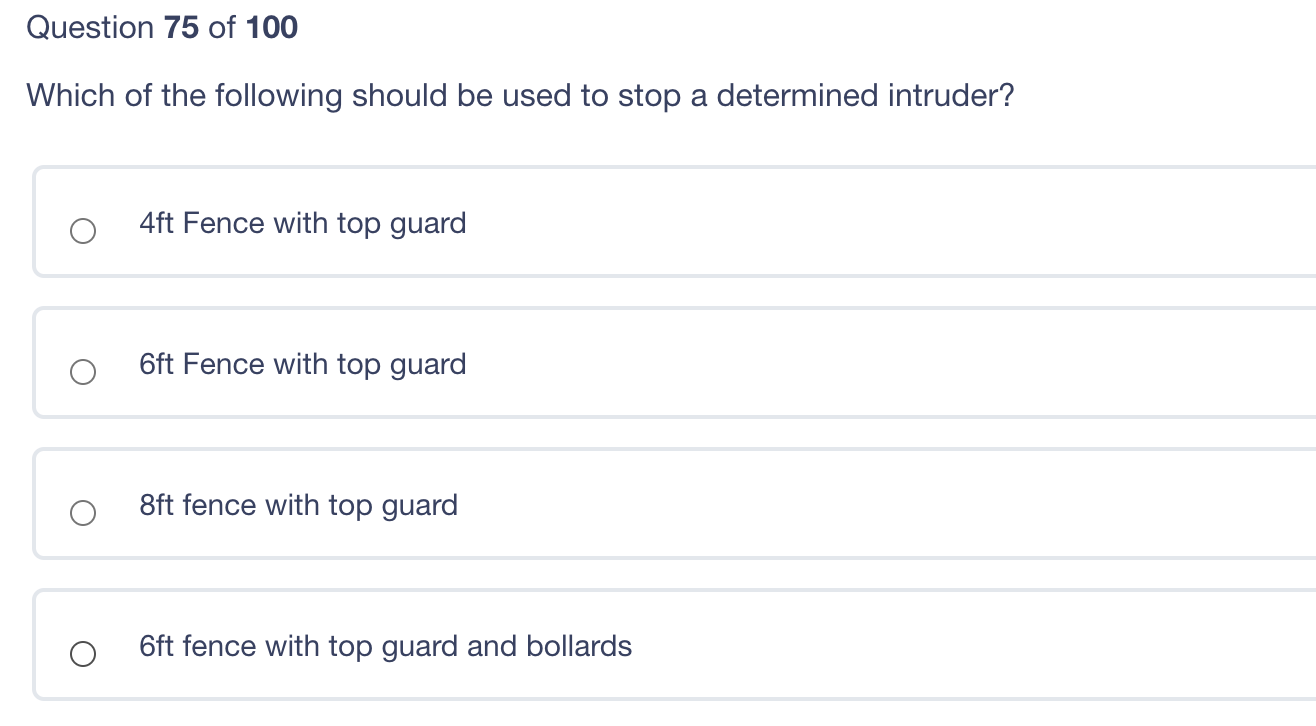

 Please ANSWER all question for thumbs up.
Please ANSWER all question for thumbs up.
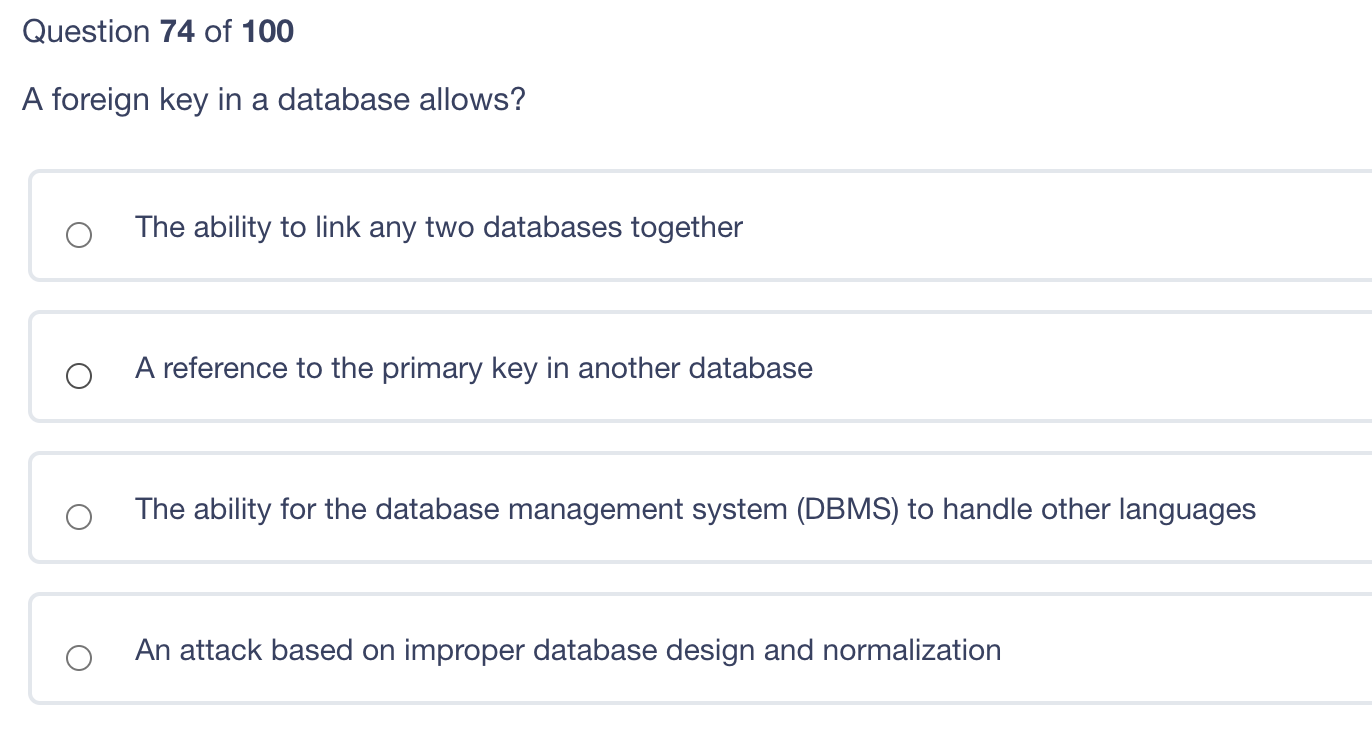
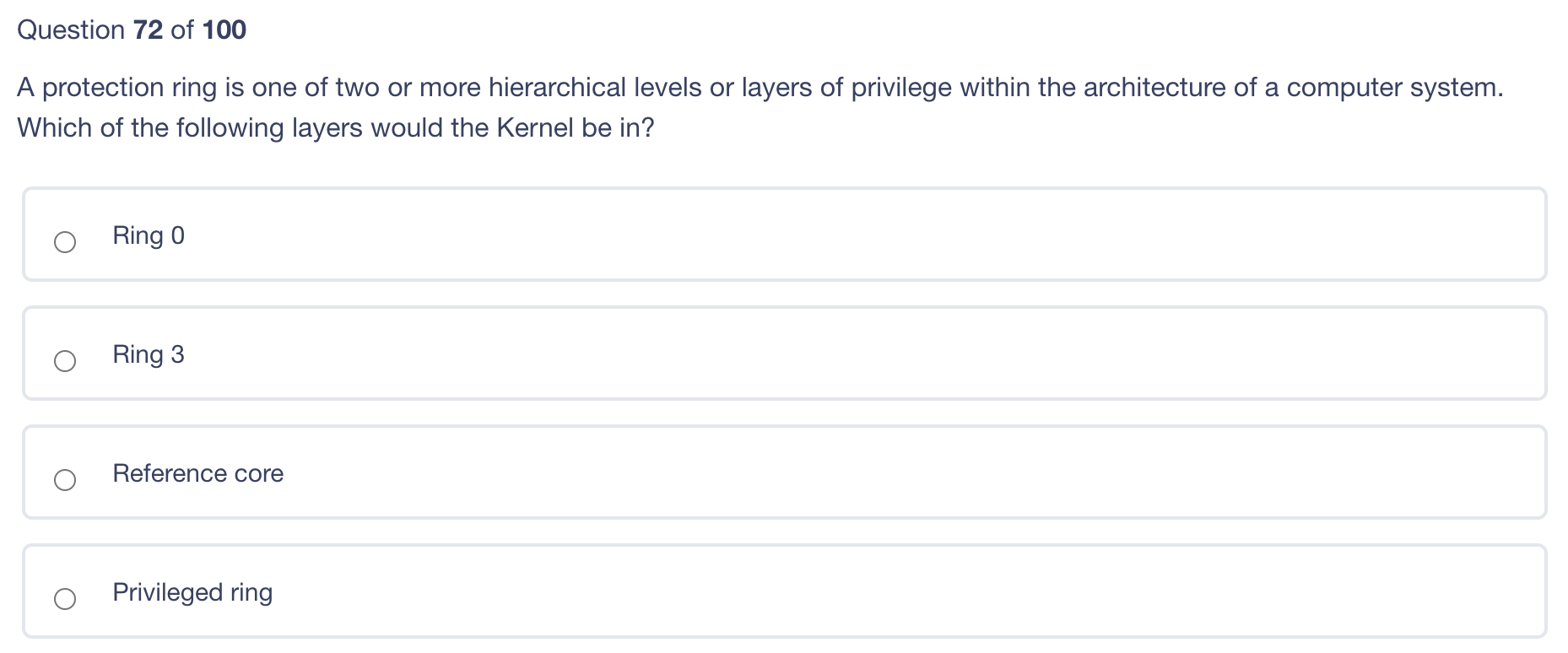
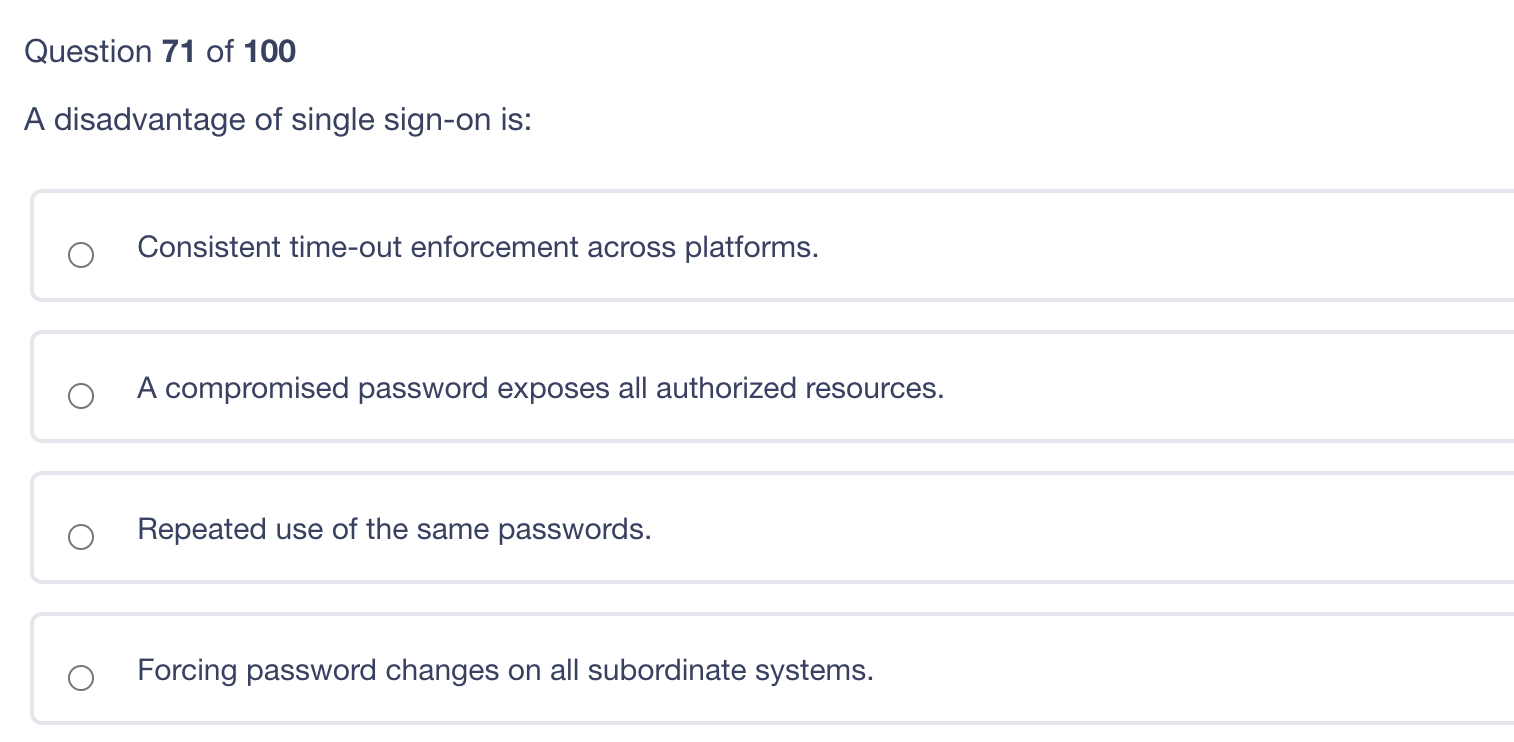
Which of the following should be used to stop a determined intruder? 4ft Fence with top guard 6ft Fence with top guard 8ft fence with top guard 6ft fence with top guard and bollards Question 74 of 100 A foreign key in a database allows? The ability to link any two databases together A reference to the primary key in another database The ability for the database management system (DBMS) to handle other languages An attack based on improper database design and normalization Question 73 of 100 Which one of the following is correct? RTO (Recovery Time Objective) is the time it will take to travel to an alternate location RPO (Recovery Point Objective) is the time that all critical systems must be operating The business continuity plan must be modular in design An incident response plan is closely tied to the disaster recovery plan in both execution and planning A protection ring is one of two or more hierarchical levels or layers of privilege within the architecture of a computer system. Which of the following layers would the Kernel be in? Ring 0 Ring 3 Reference core Privileged ring Question 71 of 100 A disadvantage of single sign-on is: Consistent time-out enforcement across platforms. A compromised password exposes all authorized resources. Repeated use of the same passwords. Forcing password changes on all subordinate systems
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


