Question: Please ANSWER all question for thumbs up. Please ANSWER all question for thumbs up. Question 80 of 100 Which of the following provides for secure
Please ANSWER all question for thumbs up.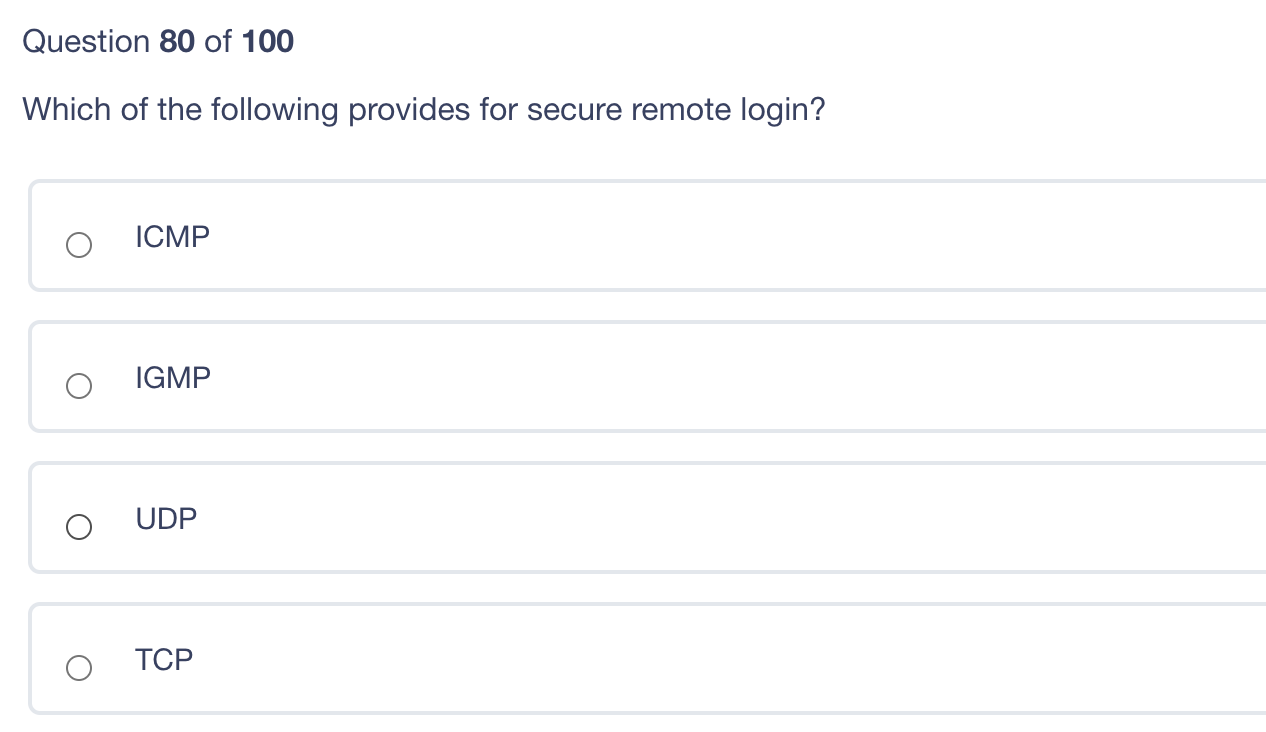
 Please ANSWER all question for thumbs up.
Please ANSWER all question for thumbs up.
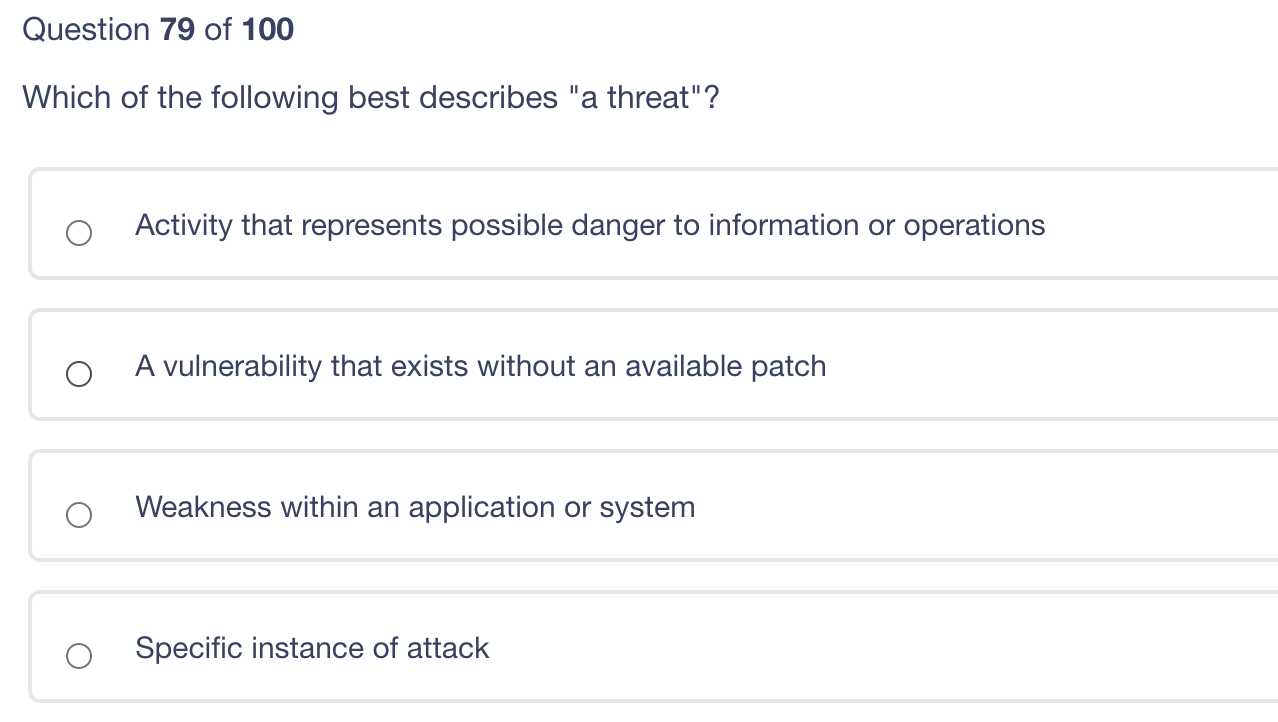
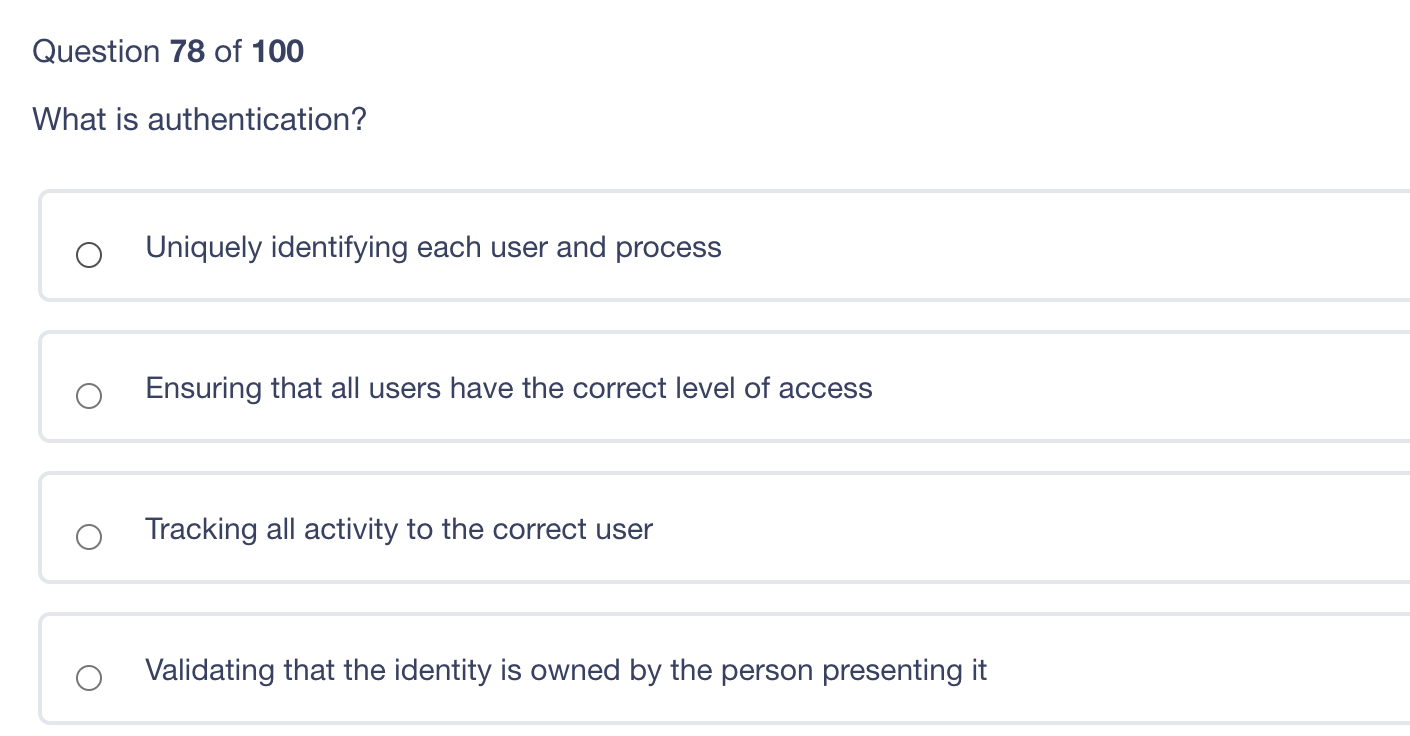
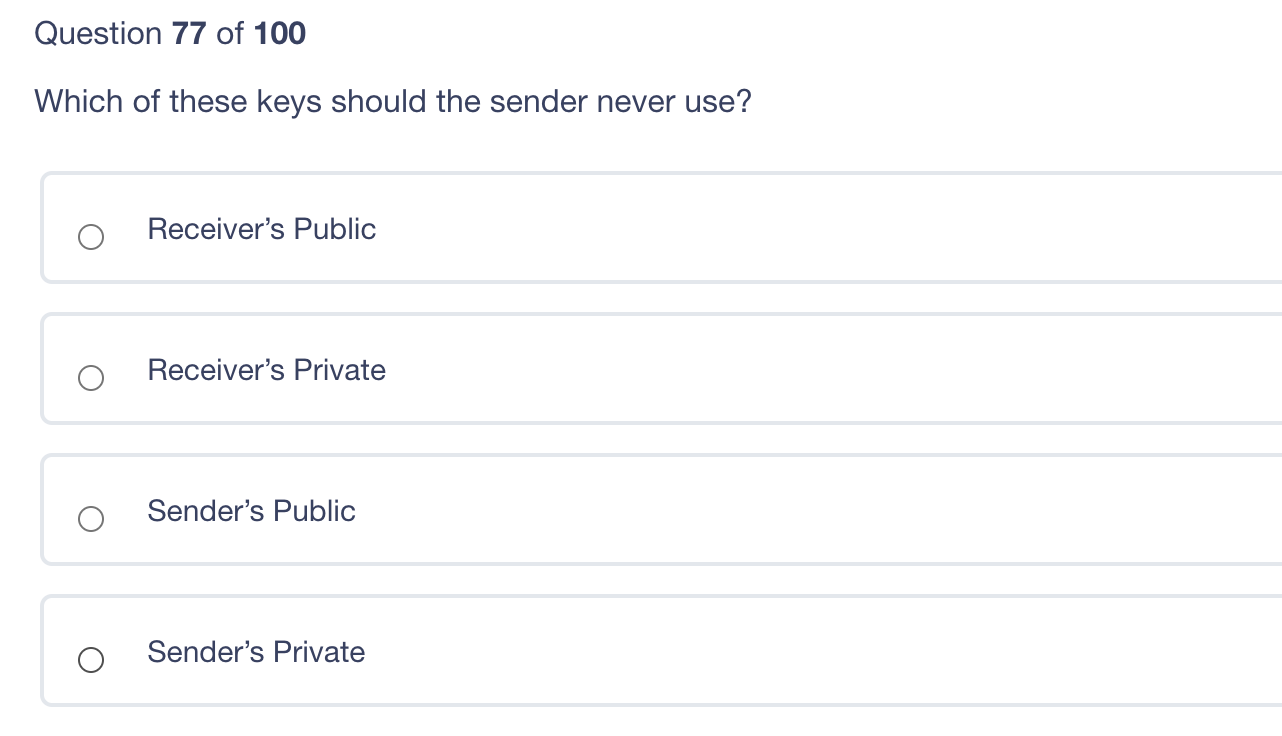
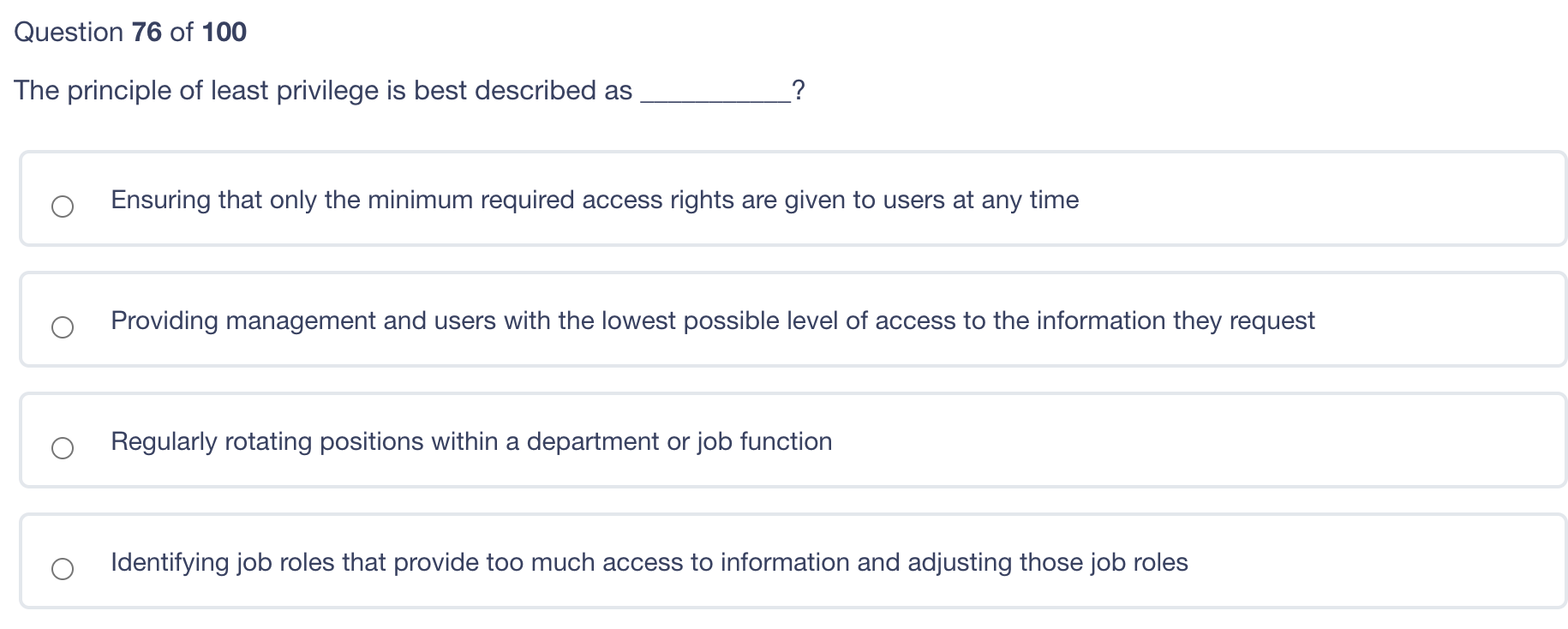
Question 80 of 100 Which of the following provides for secure remote login? ICMP IGMP UDP TCP Question 79 of 100 Which of the following best describes "a threat"? Activity that represents possible danger to information or operations A vulnerability that exists without an available patch Weakness within an application or system Specific instance of attack Question 78 of 100 What is authentication? Uniquely identifying each user and process Ensuring that all users have the correct level of access Tracking all activity to the correct user Validating that the identity is owned by the person presenting it Question 77 of 100 Which of these keys should the sender never use? Receiver's Public Receiver's Private Sender's Public Sender's Private Question 76 of 100 The principle of least privilege is best described as ? Ensuring that only the minimum required access rights are given to users at any time Providing management and users with the lowest possible level of access to the information they request Regularly rotating positions within a department or job function Identifying job roles that provide too much access to information and adjusting those job roles
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


