Question: please answer ASAP ASSESS Comm ons low FRAME WONITOR RESPOND FIGURE 1: RISK MANAGEMENT PROCESS 1. Begin your analysis with an explanation of the three
please answer ASAP 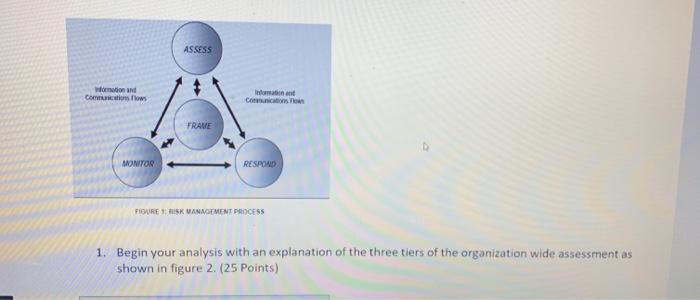
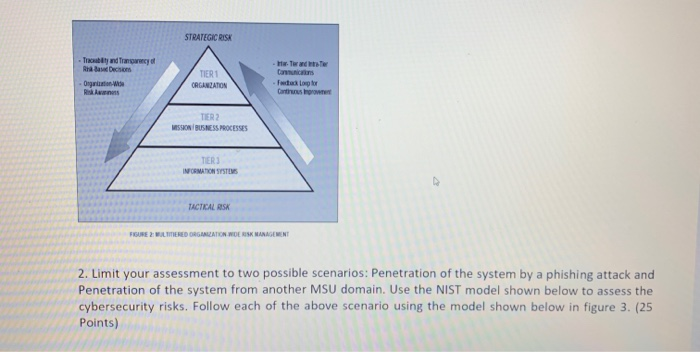
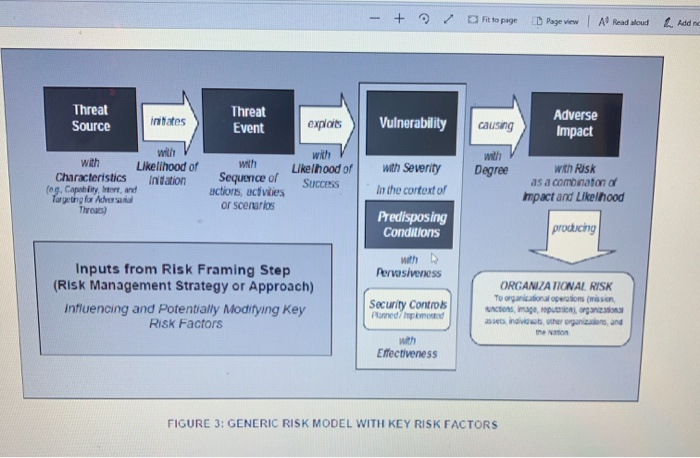
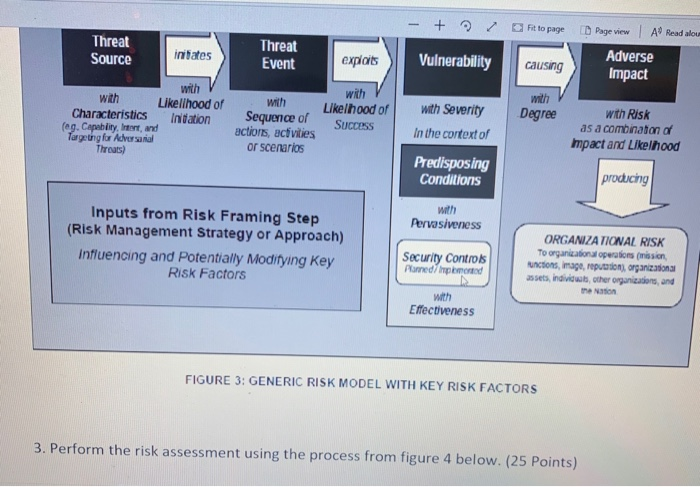
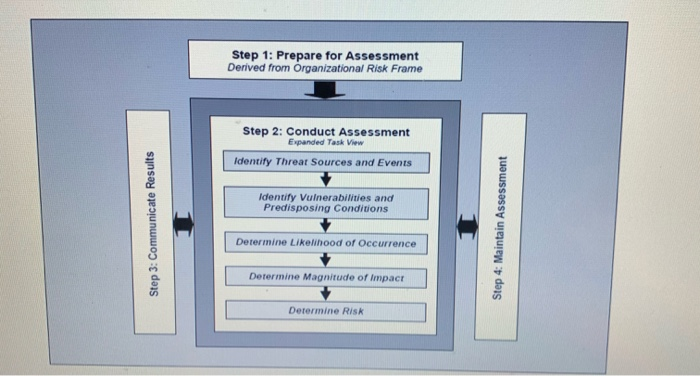
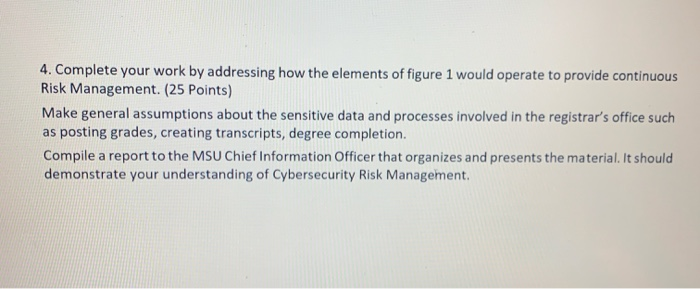
ASSESS Comm ons low FRAME WONITOR RESPOND FIGURE 1: RISK MANAGEMENT PROCESS 1. Begin your analysis with an explanation of the three tiers of the organization wide assessment as shown in figure 2. (25 Points) STRATEGIC RISK Tractand Tracy Race TIERI ORGANZATION Camions For Logo Organise Risks MISSION BUSINESS PROCESSES TER) INFOMATION SYSTEMS TACTICAL BISK FIGURE 2 W ERED ORGANIZATIONWIDE RISK MANAGEMENT 2. Limit your assessment to two possible scenarios: Penetration of the system by a phishing attack and Penetration of the system from another MSU domain. Use the NIST model shown below to assess the cybersecurity risks. Follow each of the above scenario using the model shown below in figure 3. (25 Points) - + fit to page Page view A Read aloud L Addre Threat Source intates Threat Event exploits Vulnerability causing Adverse Impact with with Likelhood of with Degree Sequence of with Likelihood of Characteristics in tation eg. Capability and Targeting for Adversal SUCCESS with Severity In the context of with Risk as a combination of Impact and Likelhood actions, activities or scenarios Thread Predisposing Conditions produchy Pervasiveness Inputs from Risk Framing Step (Risk Management Strategy or Approach) influencing and Potentially Modifying Key Risk Factors Security Controls Pored p od ORGANIZATIONAL RISK To organizational operator (mission con mage porn individwub other organdon, and with Effectiveness FIGURE 3: GENERIC RISK MODEL WITH KEY RISK FACTORS - + Fit to page Threat Event Page view A Read alou Adverse Impact exploits Vulnerability causing with Threat Source initates with with Likelihood of Characteristics Initiation (eg. Capability In , and Targeting for Adversarial Threats) with Sequence of actions, activities or scenarios Likelhood of SUCCESS Degree with Severity In the context of with Risk as a combination of mpact and Likelihood Predisposing Conditions producing with Pervasiveness Inputs from Risk Framing Step (Risk Management Strategy or Approach) Influencing and Potentially Modifying Key Risk Factors Security Controls Panned imported ORGANIZATIONAL RISK To organizational operations (mission actions, image, repom, organizations assets individuals, other organizations, and with Effectiveness FIGURE 3: GENERIC RISK MODEL WITH KEY RISK FACTORS 3. Perform the risk assessment using the process from figure 4 below. (25 Points) Step 1: Prepare for Assessment Derived from Organizational Risk Frame Step 2: Conduct Assessment Expanded Task View Identify Threar Sources and Events Identify Vulnerabilities and Predisposing Conditions Step 3: Communicate Results Step 4: Maintain Assessment Determine Likelihood of Occurrence Determine Magnitude of impact Determine Risk 4. Complete your work by addressing how the elements of figure 1 would operate to provide continuous Risk Management. (25 Points) Make general assumptions about the sensitive data and processes involved in the registrar's office such as posting grades, creating transcripts, degree completion. Compile a report to the MSU Chief Information Officer that organizes and presents the material. It should demonstrate your understanding of Cybersecurity Risk Management. ASSESS Comm ons low FRAME WONITOR RESPOND FIGURE 1: RISK MANAGEMENT PROCESS 1. Begin your analysis with an explanation of the three tiers of the organization wide assessment as shown in figure 2. (25 Points) STRATEGIC RISK Tractand Tracy Race TIERI ORGANZATION Camions For Logo Organise Risks MISSION BUSINESS PROCESSES TER) INFOMATION SYSTEMS TACTICAL BISK FIGURE 2 W ERED ORGANIZATIONWIDE RISK MANAGEMENT 2. Limit your assessment to two possible scenarios: Penetration of the system by a phishing attack and Penetration of the system from another MSU domain. Use the NIST model shown below to assess the cybersecurity risks. Follow each of the above scenario using the model shown below in figure 3. (25 Points) - + fit to page Page view A Read aloud L Addre Threat Source intates Threat Event exploits Vulnerability causing Adverse Impact with with Likelhood of with Degree Sequence of with Likelihood of Characteristics in tation eg. Capability and Targeting for Adversal SUCCESS with Severity In the context of with Risk as a combination of Impact and Likelhood actions, activities or scenarios Thread Predisposing Conditions produchy Pervasiveness Inputs from Risk Framing Step (Risk Management Strategy or Approach) influencing and Potentially Modifying Key Risk Factors Security Controls Pored p od ORGANIZATIONAL RISK To organizational operator (mission con mage porn individwub other organdon, and with Effectiveness FIGURE 3: GENERIC RISK MODEL WITH KEY RISK FACTORS - + Fit to page Threat Event Page view A Read alou Adverse Impact exploits Vulnerability causing with Threat Source initates with with Likelihood of Characteristics Initiation (eg. Capability In , and Targeting for Adversarial Threats) with Sequence of actions, activities or scenarios Likelhood of SUCCESS Degree with Severity In the context of with Risk as a combination of mpact and Likelihood Predisposing Conditions producing with Pervasiveness Inputs from Risk Framing Step (Risk Management Strategy or Approach) Influencing and Potentially Modifying Key Risk Factors Security Controls Panned imported ORGANIZATIONAL RISK To organizational operations (mission actions, image, repom, organizations assets individuals, other organizations, and with Effectiveness FIGURE 3: GENERIC RISK MODEL WITH KEY RISK FACTORS 3. Perform the risk assessment using the process from figure 4 below. (25 Points) Step 1: Prepare for Assessment Derived from Organizational Risk Frame Step 2: Conduct Assessment Expanded Task View Identify Threar Sources and Events Identify Vulnerabilities and Predisposing Conditions Step 3: Communicate Results Step 4: Maintain Assessment Determine Likelihood of Occurrence Determine Magnitude of impact Determine Risk 4. Complete your work by addressing how the elements of figure 1 would operate to provide continuous Risk Management. (25 Points) Make general assumptions about the sensitive data and processes involved in the registrar's office such as posting grades, creating transcripts, degree completion. Compile a report to the MSU Chief Information Officer that organizes and presents the material. It should demonstrate your understanding of Cybersecurity Risk Management 





Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


