Question: PLEASE DO TASK 2 AND READ EVERYTHING CAREFULLY DO STEP BY STEP. THANK YOU --------------------------------------------------------------------------------------------------------------------------- gcc -DBUF_SIZE=100 -m32 -o stack -z execstack -fno-stack-protector stack.c sudo
"PLEASE DO "TASK 2" AND READ EVERYTHING CAREFULLY"
"DO STEP BY STEP. THANK YOU
---------------------------------------------------------------------------------------------------------------------------
gcc -DBUF_SIZE=100 -m32 -o stack -z execstack -fno-stack-protector stack.c sudo chown root stack sudo chmod 4755 stack
----------------------------------------------------------------------------------------------------------------------------------
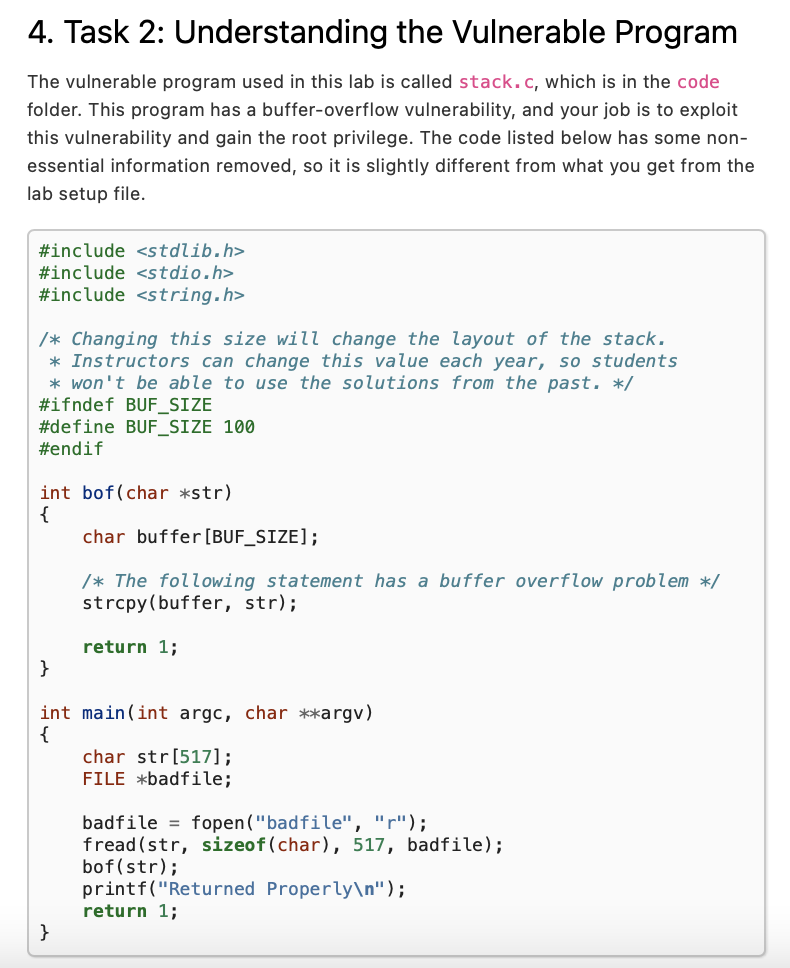
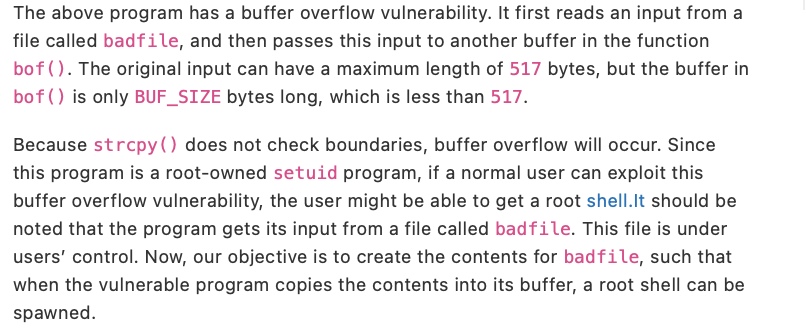
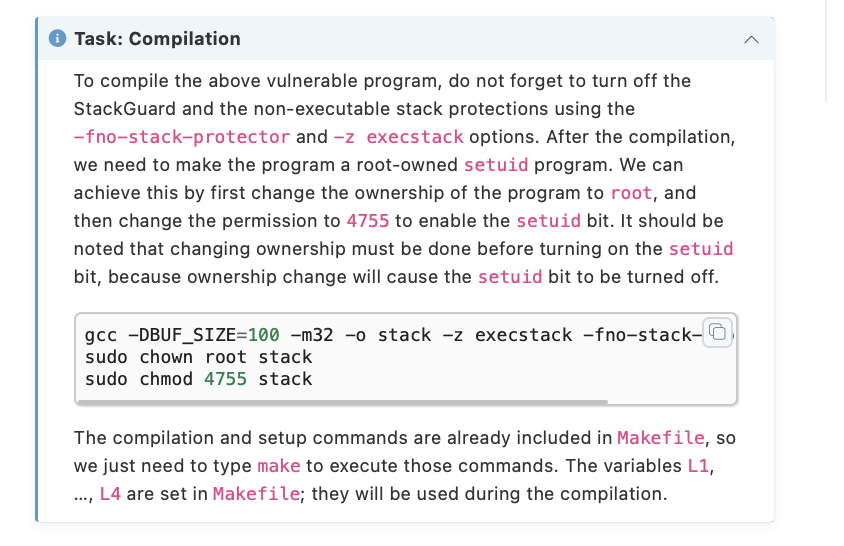
4. Task 2: Understanding the Vulnerable Program The vulnerable program used in this lab is called stack. c, which is in the code folder. This program has a buffer-overflow vulnerability, and your job is to exploit this vulnerability and gain the root privilege. The code listed below has some nonessential information removed, so it is slightly different from what you get from the lab setup file. \#include \#include \#include /* Changing this size will change the layout of the stack; * Instructors can change this value each year, so students * won't be able to use the solutions from the past. */ \#ifndef BUF_SIZE \#define BUF_SIZE 100 \#endif int bof(char str) \{ char buffer[BUF_SIZE]; /* The following statement has a buffer overflow problem / strcpy(buffer, str); return 1; int main(int argc, char argv) \{ preturn 1; The above program has a buffer overflow vulnerability. It first reads an input from a file called badfile, and then passes this input to another buffer in the function bof ( ). The original input can have a maximum length of 517 bytes, but the buffer in bof () is only BUF_SIZE bytes long, which is less than 517. Because strcpy ( ) does not check boundaries, buffer overflow will occur. Since this program is a root-owned setuid program, if a normal user can exploit this buffer overflow vulnerability, the user might be able to get a root shell.It should be noted that the program gets its input from a file called badfile. This file is under users' control. Now, our objective is to create the contents for badfile, such that when the vulnerable program copies the contents into its buffer, a root shell can be spawned. Task: Compilation To compile the above vulnerable program, do not forget to turn off the StackGuard and the non-executable stack protections using the -fno-stack-protector and -z execstack options. After the compilation, we need to make the program a root-owned setuid program. We can achieve this by first change the ownership of the program to root, and then change the permission to 4755 to enable the setuid bit. It should be noted that changing ownership must be done before turning on the setuid bit, because ownership change will cause the setuid bit to be turned off. gcc -DBUF_SIZE=100 m32 - o stack -z execstack -fno-stack- sudo chown root stack sudo chmod 4755 stack The compilation and setup commands are already included in Makefile, so we just need to type make to execute those commands. The variables L1, ..., L4 are set in Makefile; they will be used during the compilation
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


