Question: Please draw the answer like the example image included. I need to see how the message exchanges look. (35) 4. Use asymmetric encryption to establish
Please draw the answer like the example image included. I need to see how the message exchanges look.
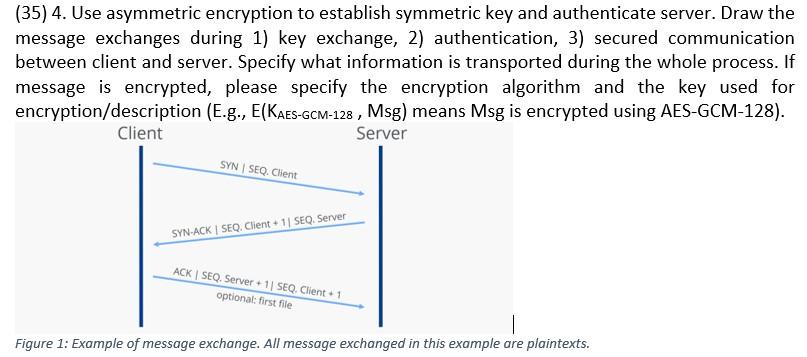
(35) 4. Use asymmetric encryption to establish symmetric key and authenticate server. Draw the message exchanges during 1) key exchange, 2) authentication, 3) secured communication between client and server. Specify what information is transported during the whole process. If message is encrypted, please specify the encryption algorithm and the key used for
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


