Question: Please explain youranswer A systemsadministrator wants to implement a wireless protocol that willallow the organization to authenticate mobile devices prior toproviding the user with a
Please explain youranswer
A systemsadministrator wants to implement a wireless protocol that willallow the organization to authenticate mobile devices prior toproviding the user with a captive portal login. Which of thefollowing should the systems administrator configure?
- L2TP with MAC filtering
- EAP-TTLS
- WPA2-CCMP with PSK
- RADIUS federation
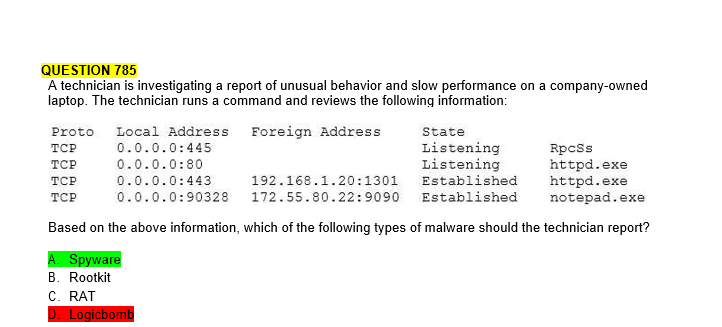
QUESTION 785 A technician is investigating a report of unusual behavior and slow performance on a company-owned laptop. The technician runs a command and reviews the following information: Proto Local Address Foreign Address TCP TCP TCP TCP State Listening Listening Established 192.168.1.20:1301 0.0.0.0:90328 172.55.80.22:9090 Established 0.0.0.0:445 0.0.0.0:80 0.0.0.0:443 RpcSs httpd.exe httpd.exe notepad.exe Based on the above information, which of the following types of malware should the technician report? A. Spyware B. Rootkit C. RAT Logicbomb
Step by Step Solution
3.47 Rating (147 Votes )
There are 3 Steps involved in it
Answer Question 1 As mentioned that the administrator want to implement wireless protocol tha... View full answer

Get step-by-step solutions from verified subject matter experts


