Question: please just choose the answer no explanation need !! Which of the following is harder to be detected by anti virus Viruses that surround a
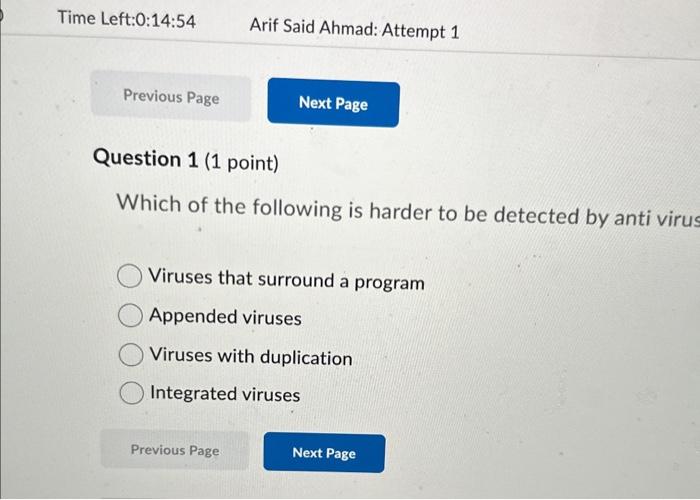
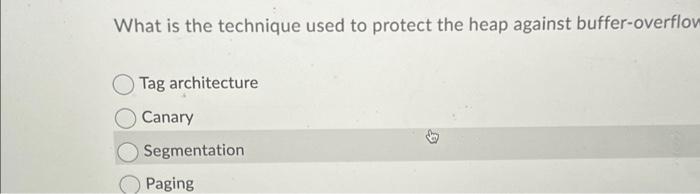

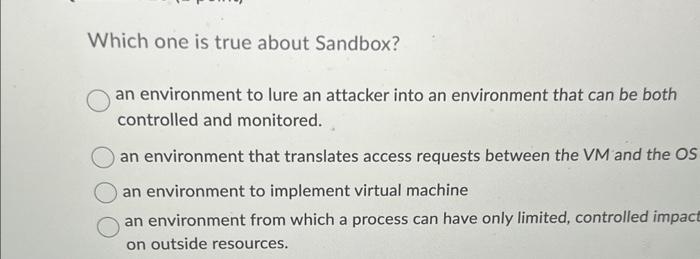

Which of the following is harder to be detected by anti virus Viruses that surround a program Appended viruses Viruses with duplication Integrated viruses What is the technique used to protect the heap against buffer-overflov Tag architecture Canary Segmentation Paging What is a Rabbit? malware that replicate itself with no limit to exhaust resources malware that propagate itself through a network malware that similar to Troje horse to limit the resources malware that drops other malicious codes Which one is true about Sandbox? an environment to lure an attacker into an environment that can be both controlled and monitored. an environment that translates access requests between the VM and the O; an environment to implement virtual machine an environment from which a process can have only limited, controlled impac on outside resources. SilentBanker is an example of: Keystroke logger User-in-the-middle Man in the browser Page-in-the-middle
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


