Question: please show your work and explain Though the RSA cryptosystem is a widely popular public key encryption scheme, another well known public-key scheme is the

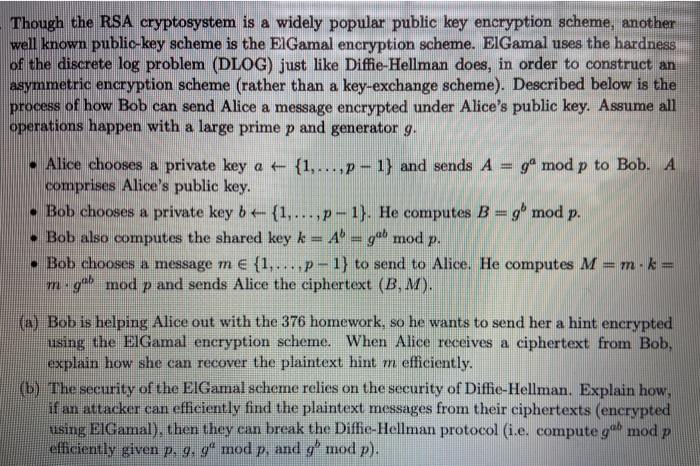
Though the RSA cryptosystem is a widely popular public key encryption scheme, another well known public-key scheme is the EIGamal encryption scheme. EIGamal uses the hardness of the discrete log problem (DLOG) just like Diffie-Hellman does, in order to construct an asymmetric encryption scheme (rather than a key-exchange scheme). Described below is the process of how Bob can send Alice a message encrypted under Alice's public key. Assume all operations happen with a large prime p and generator g. Alice chooses a private key a + {1,...,p - 1} and sends A = g mod p to Bob. A comprises Alice's public key. Bob chooses a private key b + {1,...,p-1). He computes B = g mod p. Bob also computes the shared key k = Abgab mod p. Bob chooses a message m {1,...,p-1} to send to Alice. He computes M = m.k= - got mod p and sends Alice the ciphertext (B,M). m (a) Bob is helping Alice out with the 376 homework, so he wants to send her a hint encrypted using the ElGamal encryption scheme. When Alice receives a ciphertext from Bob, explain how she can recover the plaintext hint m efficiently. (b) The security of the ElGamal scheme relies on the security of Diffie-Hellman. Explain how, if an attacker can efficiently find the plaintext messages from their ciphertexts (encrypted using ElGamal), then they can break the Diffie-Hellman protocol (i.e. compute gab mod p efficiently given p, g, gmod p, and g' mod p). Though the RSA cryptosystem is a widely popular public key encryption scheme, another well known public-key scheme is the EIGamal encryption scheme. ElGamal uses the hardness of the discrete log problem (DLOG) just like Diffie-Hellman does, in order to construct an asymmetric encryption scheme (rather than a key-exchange scheme). Described below is the process of how Bob can send Alice a message encrypted under Alice's public key. Assume all operations happen with a large prime p and generator g. - Alice chooses a private key a + {1,...,p-1) and sends A g mod p to Bob. A comprises Alice's public key. Bob chooses a private key b= {1,...,p-1). He computes B=g mod p. Bob also computes the shared key k = A= get mod p. Bob chooses a message m {1,...,p-1} to send to Alice. He computes M=m.k= mg mod p and sends Alice the ciphertext (B,M). (a) Bob is helping Alice out with the 376 homework, so he wants to send her a hint encrypted using the ElGamal encryption scheme. When Alice receives a ciphertext from Bob, explain how she can recover the plaintext hint m efficiently. (b) The security of the ElGamal scheme relies on the security of Diffie-Hellman. Explain how, if an attacker can efficiently find the plaintext messages from their ciphertexts (encrypted using ElGamal), then they can break the Diffic-Hellman protocol (i.e. compute gel mod p efficiently given p. 9. g4 mod p, and g mod p). Though the RSA cryptosystem is a widely popular public key encryption scheme, another well known public-key scheme is the EIGamal encryption scheme. EIGamal uses the hardness of the discrete log problem (DLOG) just like Diffie-Hellman does, in order to construct an asymmetric encryption scheme (rather than a key-exchange scheme). Described below is the process of how Bob can send Alice a message encrypted under Alice's public key. Assume all operations happen with a large prime p and generator g. Alice chooses a private key a + {1,...,p - 1} and sends A = g mod p to Bob. A comprises Alice's public key. Bob chooses a private key b + {1,...,p-1). He computes B = g mod p. Bob also computes the shared key k = Abgab mod p. Bob chooses a message m {1,...,p-1} to send to Alice. He computes M = m.k= - got mod p and sends Alice the ciphertext (B,M). m (a) Bob is helping Alice out with the 376 homework, so he wants to send her a hint encrypted using the ElGamal encryption scheme. When Alice receives a ciphertext from Bob, explain how she can recover the plaintext hint m efficiently. (b) The security of the ElGamal scheme relies on the security of Diffie-Hellman. Explain how, if an attacker can efficiently find the plaintext messages from their ciphertexts (encrypted using ElGamal), then they can break the Diffie-Hellman protocol (i.e. compute gab mod p efficiently given p, g, gmod p, and g' mod p). Though the RSA cryptosystem is a widely popular public key encryption scheme, another well known public-key scheme is the EIGamal encryption scheme. ElGamal uses the hardness of the discrete log problem (DLOG) just like Diffie-Hellman does, in order to construct an asymmetric encryption scheme (rather than a key-exchange scheme). Described below is the process of how Bob can send Alice a message encrypted under Alice's public key. Assume all operations happen with a large prime p and generator g. - Alice chooses a private key a + {1,...,p-1) and sends A g mod p to Bob. A comprises Alice's public key. Bob chooses a private key b= {1,...,p-1). He computes B=g mod p. Bob also computes the shared key k = A= get mod p. Bob chooses a message m {1,...,p-1} to send to Alice. He computes M=m.k= mg mod p and sends Alice the ciphertext (B,M). (a) Bob is helping Alice out with the 376 homework, so he wants to send her a hint encrypted using the ElGamal encryption scheme. When Alice receives a ciphertext from Bob, explain how she can recover the plaintext hint m efficiently. (b) The security of the ElGamal scheme relies on the security of Diffie-Hellman. Explain how, if an attacker can efficiently find the plaintext messages from their ciphertexts (encrypted using ElGamal), then they can break the Diffic-Hellman protocol (i.e. compute gel mod p efficiently given p. 9. g4 mod p, and g mod p)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


