Question: ** Please with an explanation if possible ** *Please answers all or leave it to another expert* Question #:1 Question #:7 - (Exam Topic 1)
** Please with an explanation if possible **
*Please answers all or leave it to another expert*
Question #:1
Question #:7 - (Exam Topic 1)
A user is unable to obtain an IP address from the corporate DHCP server. Which of the following is MOST likely the cause?
Default configuration
Resource exhaustion
Memory overflow
Improper input handling
-------------------------------------------------------------------------------------------------------------
Question #:2
A security engineer wants to implement a site-to-site VPN that will require SSL certificates for mutual authentication. Which of the following should the engineer implement if the design requires client MAC address to be visible across the tunnel?
A. Tunnel mode IPSec B. Transport mode VPN IPSec C. L2TP D. SSL VPN
-------------------------------------------------------------------------------------------------------------
Question #:3
Which of the following should a company require prior to performing a penetration test? A . NDA B . CVE score C . Data classification D . List of threats
------------------------------------------------------------------------------------------------------------- Question #:4
During certain vulnerability scanning scenarios, It is possible for the target system to react in unexpected ways.
This type of scenario is MOST commonly known as: A . intrusive testing. B . a butter overflow. C . a race condition D . active reconnaissance
-------------------------------------------------------------------------------------------------------------
Question #:5
A security analyst has recently deployed an MDM solution that requires biometric authentication for company-issued smartphones. As the solution was implemented the help desk has seen a dramatic increase in calls by employees frustrated that company-issued phones take several attempts to unlock using the fingerprint scanner.
Which of the following should be reviewed to mitigate this problem? A . Crossover error rate B . False acceptance rate C . False rejection rate D . True rejection rate
------------------------------------------------------------------------------------------------------------- Question #:6
A technician suspects that a desktop was compromised with a rootkit.
After removing the hard drive from the desktop and running an offline le integrity check, the technician reviews the following output: 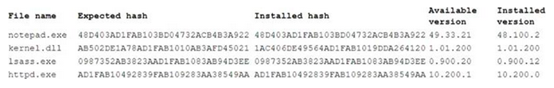 Based on the above output, which of the following is the malicious file? A . notepad.exe B . lsass.exe C . kernel.dll D . httpd.axe
Based on the above output, which of the following is the malicious file? A . notepad.exe B . lsass.exe C . kernel.dll D . httpd.axe
-------------------------------------------------------------------------------------------------------------
Question #:7
A security analyst needs to generate a server certificate to be used for 802.1X and secure RDP connections. The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task? A. Create an OCSP B. Generate a CSR C. Create a CRL D. Generate a .pfx file ------------------------------------------------------------------------------------------------------------- Question #:8
A company is performing an analysis of the corporate enterprise network with the intent of identifying what will cause losses in revenue, referrals, and/or reputation when out of commission. Which of the following is an element of a BIA that is being addressed? A. Mission-essential function B. Single point of failure C. backup and restoration plans D. Identification of critical systems
------------------------------------------------------------------------------------------------------------- Question #:9
A technician is installing a new SIEM and is configuring the system to count the number of times an event occurs at a specific logical location before the system takes action.
Which of the following BEST describes the feature being configured by the technician? A . Correlation B . Aggregation C . Event deduplication D . Flood guard
------------------------------------------------------------------------------------------------------------- Question #:10
A security analyst receives the following output  Which of the following MOST likely occurred to produce this output? A . The host-based firewall prevented an attack from a Trojan horse B . USB-OTG prevented a file from being uploaded to a mobile device C . The host DLP prevented a file from being moved off a computer D . The firewall prevented an incoming malware-infected file
Which of the following MOST likely occurred to produce this output? A . The host-based firewall prevented an attack from a Trojan horse B . USB-OTG prevented a file from being uploaded to a mobile device C . The host DLP prevented a file from being moved off a computer D . The firewall prevented an incoming malware-infected file
File name notepad.exe kernel.dll lsass.exe httpd.exe Available Expected hash Installed hash version 480403ADLFAB103BD04732ACB4B3A922 480403ADIFAB203BD04732ACB4B3A922 49.33.21 AB502DE1A78ADZFAB1010AB3AFD45021 TAC406249564AD FAB1019DDA2641201.01.200 0987352AB3823AADIFAB1083AB94D3EE 0987352AB 382 3AADIFAB1083AB94D3EE 0.900.20 AD1FAB10492839FAB109283AA 38549AA ADIFAB10492839FAB109283AA38549AA 10.200.1 Installed version 48.200.2 1.01.200 0.900.12 10.200.0 Host Time Action 12/15/2017 Policy: Endpoint USB Transfer Blocked File Name User 03- User1 Financials.PDF Hosti
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


