Question: ** Please with an explanation if possible ** *Please answers all or leave it to another expert* Question #:1 Which of the following is MOST
** Please with an explanation if possible **
*Please answers all or leave it to another expert*
Question #:1
Which of the following is MOST likely happening?
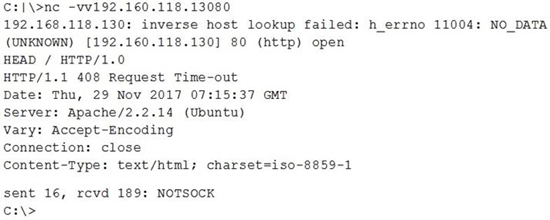 A hacker attempted to pivot using the web server interface.
A hacker attempted to pivot using the web server interface.
A potential hacker could be banner grabbing to determine what architecture is being used
The DNS is misconfigured for the server's IP address.
A server is experiencing DoS, and the request Is timing out.
-------------------------------------------------------------------------------------------------------------
Question #:2
A Chief Executive Officer (CEO) is staying at a hotel during a business trip. The hotel's wireless network does not show a lock symbol. Which of the following precautions should the CEO take? (Select TWO).
Change the connection type to WPA2.
Change TKIP to CCMR
Use a VPN. Tether to a mobile phone.
Create a tunnel connection with EAP-TTLS.
-------------------------------------------------------------------------------------------------------------
Question #:3
A company has migrated to two-factor authentication for accessing the corporate network, VPN, and SSO. Several legacy applications cannot support multifactor authentication and must continue to use usernames and passwords. Which of the following should be implemented to ensure the legacy applications are as secure as possible while ensuring functionality? (Select TWO).
Privileged accounts
Password reuse restrictions
Password complexity requirements
Password recovery
Account disablement
------------------------------------------------------------------------------------------------------------- Question #:4
Which of the following BEST explains likelihood of occurrence'?
The chance that an event will happen regardless of how much damage it may cause
The overall impact to the organization once all factors have been considered
The potential for a system to have a weakness or aw that might be exploited
The probability that a threat actor will target and attempt to exploit an organization's systems
-------------------------------------------------------------------------------------------------------------
Question #:5
A security specialist is notified about a certificate warning that users receive when using a new internal website. After being given the URL from one of the users and seeing the warning, the security specialist inspects the certificate and realizes it has been issued to the IP address, which is how the developers reach the site. Which of the following would BEST resolve the issue?
A. OSCP
B. OID
C. PEM
D. SAN
------------------------------------------------------------------------------------------------------------- Question #:6
A technician has been asked to document which services are running on each of a collection of 200 servers. Which of the following tools BEST meets this need while minimizing the work required?
A. Nmap
B. Nslookup
C. Netcat
D. Netstat
-------------------------------------------------------------------------------------------------------------
Question #:7
Which of the following explains why a vulnerability scan might return a false positive?
A. The scan is performed at a time of day when the vulnerability does not exist.
B. The test Is performed against the wrong host.
C. The signature matches the product but not the version information.
D. The hosts are evaluated based on an OS-specific profile.
------------------------------------------------------------------------------------------------------------- Question #:8
Which of the following may indicate a configuration item has reached end-of-life?
A. The device will no longer turn on and indicates an error
B. The vendor has not published security patches recently.
C. The object has been removed from the Active Directory.
D. Logs show a performance degradation of the component.
------------------------------------------------------------------------------------------------------------- Question #:9
Which of the following Impacts are associated with vulnerabilities in embedded systems? (Select TWO).
A. Repeated exploitation due to unpatchtable firmware
B. Denial of service due to an integrated legacy operating system
C. Loss of inventory accountability due to device deployment
D. Key reuse and collision Issues due to decentralized management
E. Exhaustion of network resources resulting from poor NIC management
------------------------------------------------------------------------------------------------------------- Question #:10
Which of the following algorithms would be used to provide non-repudiation of a file transmission?
A. AES
B. RSA
C. MD5
D. SHA
C:\>nc -vv192.160.118.13080 192.168.118.130: inverse host lookup failed: n_errno 11004: NO_DATA (UNKNOWN) [192.160.118.130] 80 (http) open HEAD / HTTP/1.0 HTTP/1.1 408 Request Time-out Date: Thu, 29 Nov 2017 07:15:37 GMT Server: Apache/2.2.14 (Ubuntu) Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=iso-8859-1 sent 16, rcvd 189: NOTSOCK C:\>
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


