Question: Problem 2: Why do organizations include honeypots in their network security strategies? Problem 3: What are the main components of a distributed intrusion detection system?
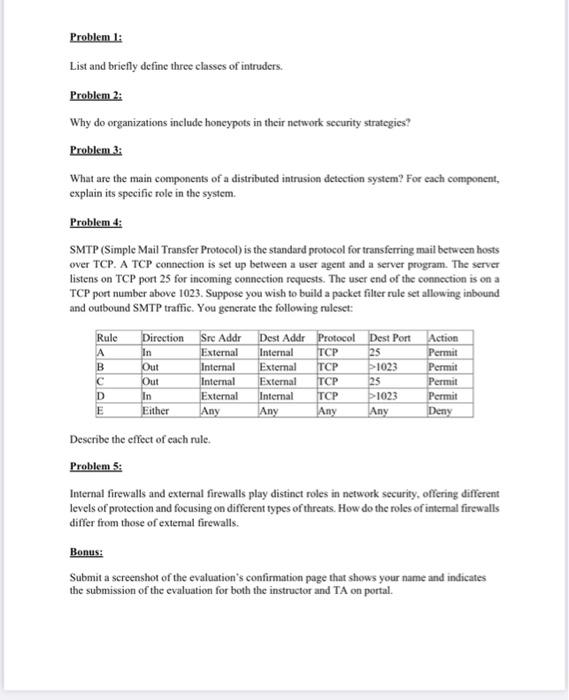
Problem 2: Why do organizations include honeypots in their network security strategies? Problem 3: What are the main components of a distributed intrusion detection system? For each component, explain its specific role in the system. Problem 4: SMTP (Simple Mail Transfer Protocol) is the standard protocol for transferring mail between hosts over TCP. A TCP connection is set up between a user agent and a server program. The server listens on TCP port 25 for incoming connection requests. The user end of the connection is on a TCP port number above 1023. Suppose you wish to build a packet filter rule set allowing inbound and outbound SMTP traffic. You generate the following ruleset: Describe the effect of each rule. Problem 5: Internal firewalls and external firewalls play distinct roles in network security, offering different levels of protection and focusing on different types of threats. How do the roles of intemal firewalls differ from those of extemal firewalls. Bonus: Submit a screenshot of the evaluation's confirmation page that shows your name and indicates the submission of the evaluation for both the instructor and TA on portal
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


