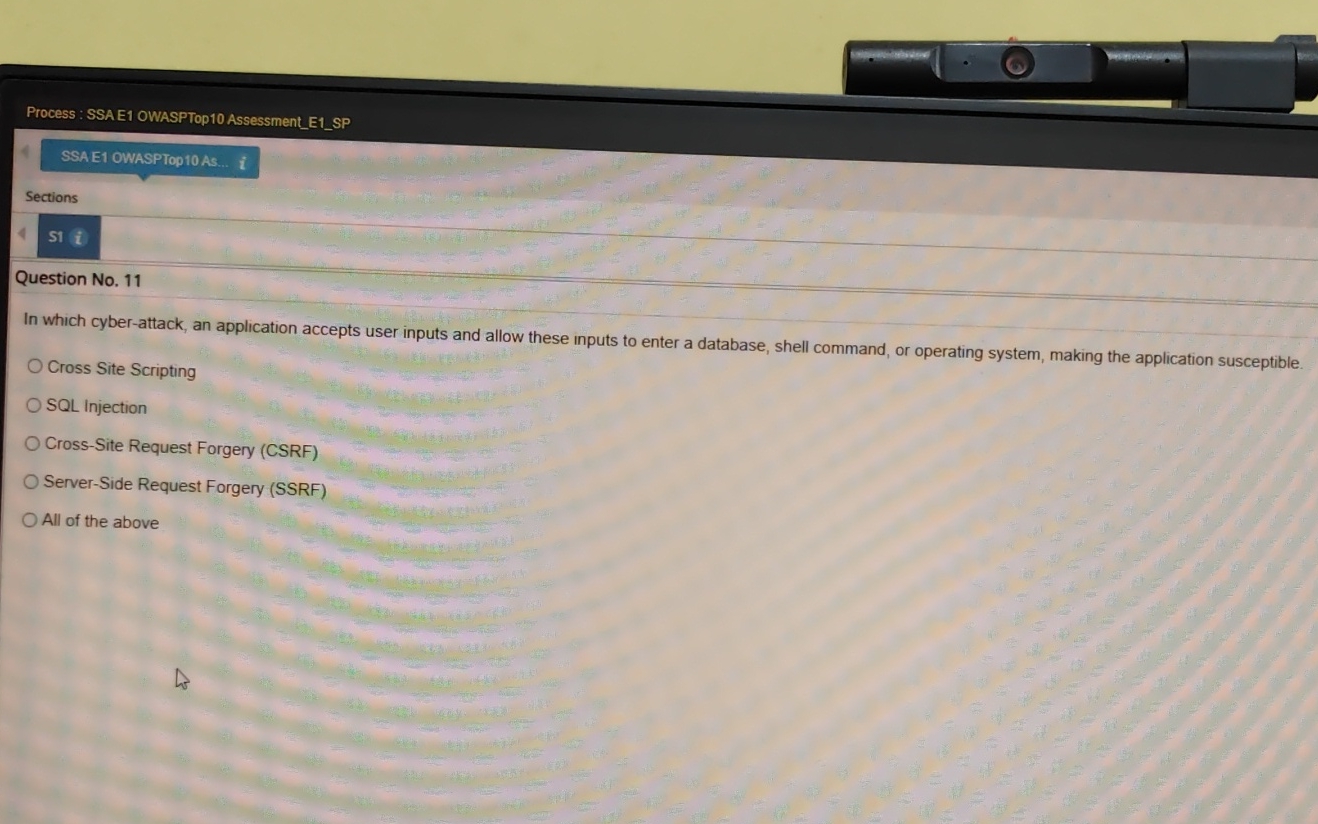
Question: Process : SSAE 1 OWASPTop 1 0 Assessment _ E 1 _ SP Sections Question No . 1 1 In which cyber - attack, an
Process : SSAE OWASPTop AssessmentESP
Sections
Question No
In which cyberattack, an application accepts user inputs and allow these inputs to enter a database, shell command, or operating system, making the application susceptible.
Cross Site Scripting
SQL Injection
CrossSite Request Forgery CSRF
ServerSide Request Forgery SSRF
All of the above
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


