Question: Project 1 - Encryption Methods Overview: The first three schemes to be described fall into the category of key-based schemes The key is a value



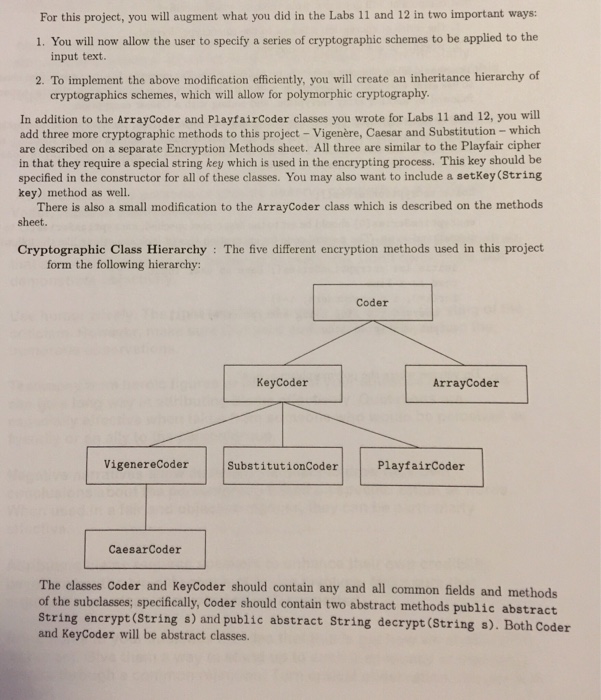

Project 1 - Encryption Methods Overview: The first three schemes to be described fall into the category of key-based schemes The key is a value used by the encryption algorithm in order to encrypt text; vary the key and you vary the type of encryption you get. For the purposes of this project, all keys will be String values All key's should be converted to uppercase and have all non-letter characters removed before being used Vigenre encryption: The key in this scheme is a string of characters of length n. Each character in the key represents a shift value; this value is obtained by subtracting 'A' from the character This shift value is them added to a letter in order to encrypt it. For example, if the first shift letter is ,w,, then the shift value is ,w,-,A, 22. This value would then be added to the letter to be encrypted (recall that char values are really just integers). The table below shows how any letter would be encrypted using this shift value original A BC DE F encrypted WXYZ AB Notice how the encrypted letters wrap around once 'Z' is reached The Vigenre scheme uses multiple shift values. The first character to be encrypted uses the first letter of the key as its shift; the second character uses the second letter of the key as its shift; the third character uses the third letter of the key, and so on. After the n-th character is encrypted the n1-st character uses the first character of the key and the process repeats. For example, if the key was "WAX" and the text to be encrypted was "WESTMINSTER", then the characters 'W' 'T, 'N' and 'E' would use the key letter 'W' when encrypted, the characters 'E', 'M', 'S' and 'R' would use the key letter 'A' when encrypted, and the characters 'S', 'I' and 'T' would use the key letter 'X' when encrypted. The resulting encrypted text would be "SEPPMFJSQAR". Substitution encryption: For this encryption scheme, the key is any string of characters. We first remove any duplicate letters in the key and then append the remaining letters of the alphabet in reverse order. The resulting 26 letter key serves as the encrypted versions of cach letter of the alphabet. For example, if the key was "westminster", it would first be converted to the 26 letter key "WESTMINRZYXVUQPOLKJHGFDCBA" and the encryption pattern would be original encrypted W With this key, the string "WESTMINSTER" would be encrypted as "DMJHUZQJHMK" Caesar encryption: This is the oldest known encryption scheme (and unfortunately one of the easiest to crack). It uses a fixed shift value of 3 to encrypt every character Array encryption: This is the encryption scheme you implemented in Lab 11. In that scheme we fixed the 2-dimensional array to be a 5 5 array. Modify this approach so that the grid is an n n array, where n is the smallest integer such that n2
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


