Question: Prolog for Artificial Intelligence A basic D-type flip-flop is addressed by the Prolog predicate dff whose definition is as per the following: dff(D, 0, Q,
Prolog for Artificial Intelligence A basic D-type flip-flop is addressed by the Prolog predicate dff whose definition is as per the following: dff(D, 0, Q, Q). dff(D, 1, Q, D). The primary contention is the contribution to the flip-flop, the second is the clock with 0 addressing a falling edge and 1 addressing a rising edge. The third and fourth contentions are the past and next conditions of the flip-flop. As should be visible the state of the flip-flop changes on a rising edge of the clock. A timed circuit comprises of three d-type goes back and forth with information sources and states (D1, Q1), (D2, Q2) and (D3, Q3). They are wired so that D1 = (Q1 ? Q2) ? (Q1 ? Q2) D2 = (Q1 ? Q3) ? (Q2 ? Q3) D3 = (Q1 ? Q3) ? (Q2 ? Q3) (a) Using s(Q1, Q2, Q3) to address the condition of the circuit, characterize a predicate that will register the state after the following rising edge of the clock. You may find it supportive to characterize predicates to address and, or and not entryways. [14 marks] (b) Define a predicate testcc(N, s(Q1,Q2,Q3), List) that will figure the rundown of states (List) through which the circuit passes from the given introductory state s(Q1,Q2,Q3) because of a grouping of N rising edges of the clock. [6 marks] 6 CST.2002.13.7 8 Databases ((profoundly) social polynomial math. [6 marks] (b) The center social polynomial math is frequently reached out with different administrators. For the following administrators give a definition and an illustration of their way of behaving: (I) the full external join administrator; [3 marks] (ii) the total and gathering administrator. [5 marks] (c) X, Y and Z are on the whole relations with a solitary characteristic A. A na?ve client wishes to figure the set-hypothetical articulation X ? (Y ? Z) and composes the accompanying SQL inquiry. SELECT X.A FROM X,Y,Z WHERE X.A=Y.A OR X.A=Z.A (I) Give the social variable based math term that this inquiry would be assembled to. [2 marks]
(a) Write ML work converge of type ('a * 'a - > bool) - > ('a rundown * 'a rundown) - > 'a rundown which takes an examination capacity of type 'a * 'a - > bool and gives a capacity for blending two arrangements of type 'an as per this capacity. [6 marks] (b) Use your capacity converge to compose a curried polymorphic capacity mergesort which takes a correlation work f and yields an arranging capacity of the proper sort. [6 marks] (c) Write a capacity sumcomp which takes two number records and returns the boolean worth valid assuming the amount of numbers in the main rundown is no more prominent than the amount of whole numbers in the subsequent rundown and bogus in any case. [6 marks] (d) What is the kind of the articulation mergesort sumcomp? [2 marks] 9 [TURN OVER CST.2002.13.10 11 Computer Vision (a) Consider the "eigenfaces" way to deal with face acknowledgment in PC vision. (I) What is the r?ole of the data set populace of model appearances whereupon this calculation depends? [4 marks] (ii) What are the highlights that the calculation concentrates, and how can it process them? How is any given face addressed concerning the current populace of countenances? [4 marks] (iii) What are the qualities and the shortcomings of this kind of portrayal for human countenances? What invariances, if any, does this calculation catch over the variables of point of view point (or posture), enlightenment math, and look? [4 marks] (iv) Describe the relative computational intricacy of this calculation, its capacity to learn after some time, and its run of the mill execution in face acknowledgment preliminaries. [4 marks] (b) What is the accompanying square of code doing over the picture cluster image[i][j] as it processes the subsequent new picture exhibit result[i][j] ? Give the suitable numerical name for this activity, and portray what it achieves. What are some PC vision undertakings that could utilize this square of four settled for circles? for (I = 0; I 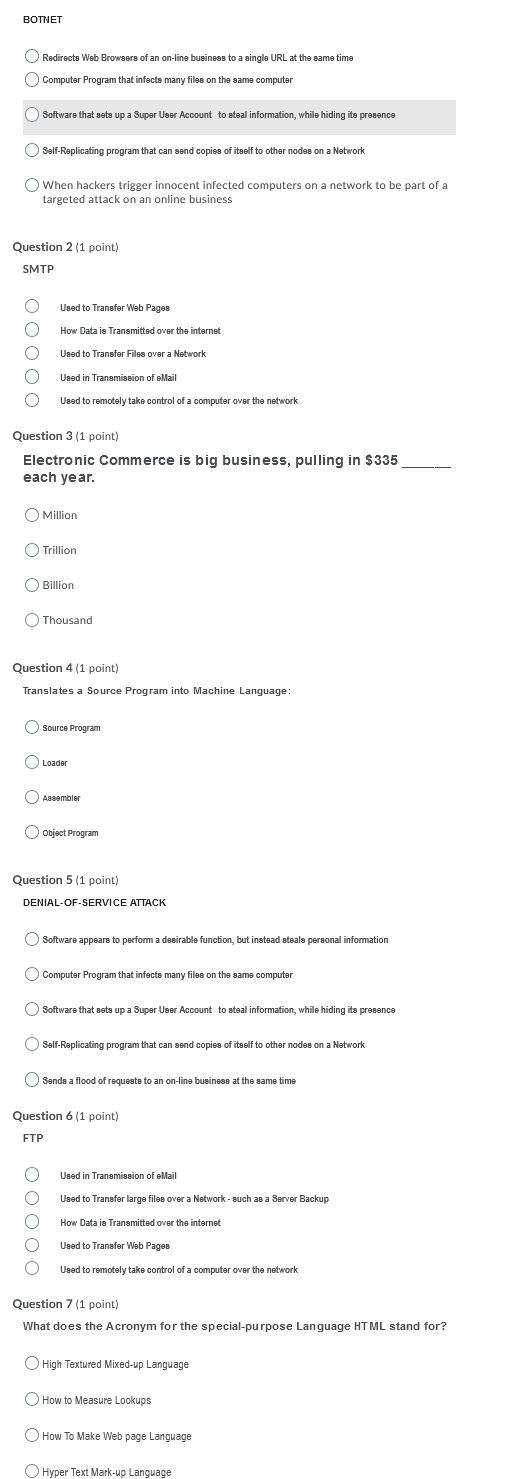
BOTNET Redirects Web Browsers of an on-line business to a single URL at the same time Computer Program that infects many files on the same computer Software that sets up a Super User Account to steal information, while hiding its presence Self-Replicating program that can send copies of itself to other nodes on a Network When hackers trigger innocent infected computers on a network to be part of a targeted attack on an online business Question 2 (1 point) SMTP 00000 Used to Transfer Web Pages How Data is Transmitted over the internet Used to Transfer Files over a Network Used in Transmission of eMail Used to remotely take control of a computer over the network Question 3 (1 point) Electronic Commerce is big business, pulling in $335 each year. Million Trillion Billion Thousand Question 4 (1 point) Translates a Source Program into Machine Language: Source Program Loader Assembler Object Program Question 5 (1 point) DENIAL-OF-SERVICE ATTACK Software appears to perform a desirable function, but instead steals personal information Computer Program that infects many files on the same computer Software that sets up a Super User Account to steal information, while hiding its presence Self-Replicating program that can send copies of itself to other nodes on a Network Sends a flood of requests to an on-line business at the same time Question 6 (1 point) FTP Used in Transmission of eMail Used to Transfer large files over a Network - such as a Server Backup How Data is Transmitted over the internet Used to Transfer Web Pages Used to remotely take control of a computer over the network Question 7 (1 point) What does the Acronym for the special-purpose Language HTML stand for? High Textured Mixed-up Language How to Measure Lookups How To Make Web page Language Hyper Text Mark-up Language
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


