Question: Q2. List with Hash Pointers (7 points] The linked list below uses hash pointers. Each item in this list has three fields: ID, previous item
![Q2. List with Hash Pointers (7 points] The linked list below](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f03fe6c2c92_03066f03fe63f730.jpg)
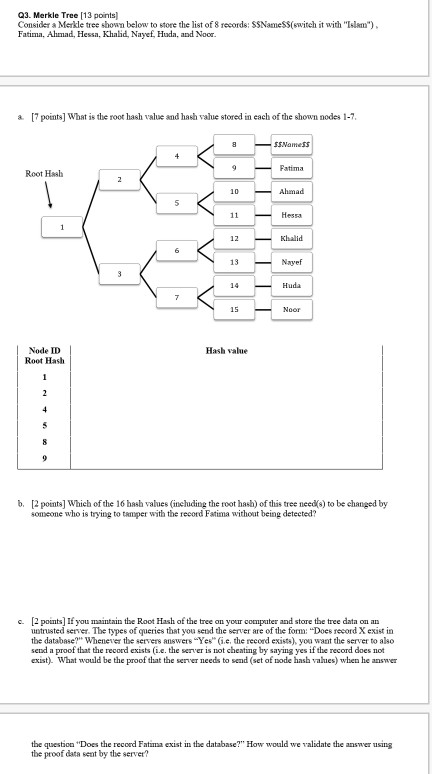
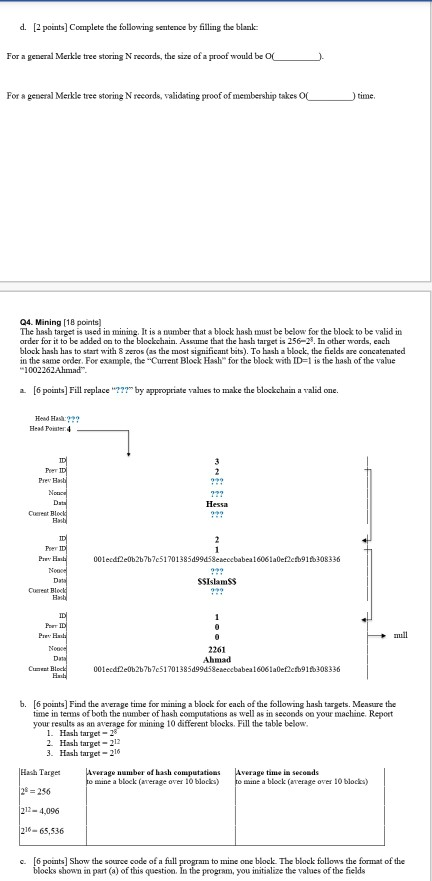
Q2. List with Hash Pointers (7 points] The linked list below uses hash pointers. Each item in this list has three fields: ID, previous item ID previous node hash, and data. To hash a block, the fields are concatenated in the same order. For example, to hash the block with ID=4, the following value is hashed (after replacing ??? with the right Prev Hash value): "43???Hessa" a. [4 points] Fill the missing hash values for this list (replace ??? by the appropriate value) Head Pointer 4 Head Hash??? Prer ID Prev Hasli ??? Det Hessa Prer ID Prev Hasli ??? Ahmad Date PrevD Prev Hasil Date Fatima Prev Prev Hall Dard SSIslams - null b. [1 point) Suppose that you store this list on an untrusted computer. How much data you need to store to be able to detect any malicious tampering with the data? c. [1 point) Explain how you will be able to detect if someone changes "Fatima" to "Fatma". d. 1 point) Explain how will you be able to detect if someone changes "Fatima" to "Fatma" and also re-computes the Prev Hash values of blocks with IDs 3 and 4 Q3. Merkle Tree (13 points) Consider a Merkle tree shown below to store the list of records: SSName(switch it with "Islam") Fatima, Ahmad, Hessa, Khalid, Nayef, Huda, and Noor a 17 points) What is the root hash value and hash value stored in each of the shown nodes 1-7 - Names - Fatima Root Hash Ahmad Hessa Khalid Nayef Huda Noor Hash value Node ID Root Hast: b. 12 points) Which of the 16 hash values (including the root hash) of this tree need(s) to be changed by someone who is trying to tamper with the record Fatima without being detected? 12 points. If you maintain the Root Hash of the tree on your computer and store the tree data oman trusted server. The types of queries that you send the server are of the form "Does record X exist in the database. Whenever the serv e rs "Yes" (ie the record exit you want the server to also send a proof that the record exists (ie there is not cheating by saying yes if the record does not exist). What would be the proof that the ever needs to wed (set of node hash values) when he an the question "Does the record Fatima exist in the database?" How would we validate the answer using the proof data sent by the server? d. (2 points) Complete the following sentence by filling the blank For a general Merkle tree storing N records, the size of a proof would be o For a general Merkle tree storing N records, validating proof of membership takes time. 04. Mining (18 points The hub target is medin mining. It is a mamber that a block hashist be below for the block to be valid in order for it to be added to the blockchain. Assume that the hash tartis 256-21. In other words, cach block hash has to start with zeros(as the most significant buts). To bash a black, the fields are concatenated in the same order. For example, the Current Block Hal for the block with ID-1 is the hash of the value "1002262 Alunad" a. [6 points) Fill replace by appropriate values to make the blockchain a valid one. Head4 PID Need Hessa C lock PID PH Nood colecd0b2b7b751701395499d5ebeecbabeat 6061ef91208316 SSIslams Cro Ne D Ahmad OledD02717517013850995ean babea160610 2 09216 b. [6 points) Find the average time for mining a block for each of the following hash targets. Measure the tune in terms of both the umber of hash compute s well as in seconds on your machine. Report your role as average for mining 10 different blocks. Fill the table below 1. Hash target 2 Hash target-212 3. Hashart-216 Average number of hash computations homine a block average 10 ocks) Average time in seconds mine a block (average over 10 Mocks) Hash Target 28 = 256 212 - 4,096 216-65,536 c. (6 points Show the source code of a full program to mine one block. The block follows the format of the blocks shown in part (a) of this question. In the program, you initialize the values of the fields c. [6 points) Show the source code of a full program to mine one block. The block follows the format of the blocks shown in part (a) of this question. In the program, you initialize the values of the fields I ID O Prev ID | Prev Hash O Data It computes and prints the Nonce and the Current Block Hash values. You can use a programming language of your choice
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


