Question: Q4: Suppose H is a well-designed pseudorandom generator, now we want to take a larger input y y1||42, (y1 is the first half of y
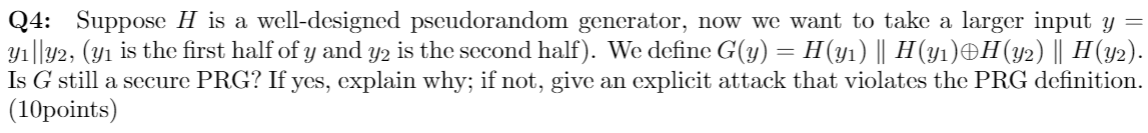
Q4: Suppose H is a well-designed pseudorandom generator, now we want to take a larger input y y1||42, (y1 is the first half of y and y2 is the second half). We define G(y) = H(y) || H(y)H(y2) || H(y2). Is G still a secure PRG? If yes, explain why; if not, give an explicit attack that violates the PRG definition. (10points)
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


