Question: Quantitative Threat Analysis Springfield I.T . Consulting develops and maintains business software for IT clients. Springfield is doing a threat analysis as part of a
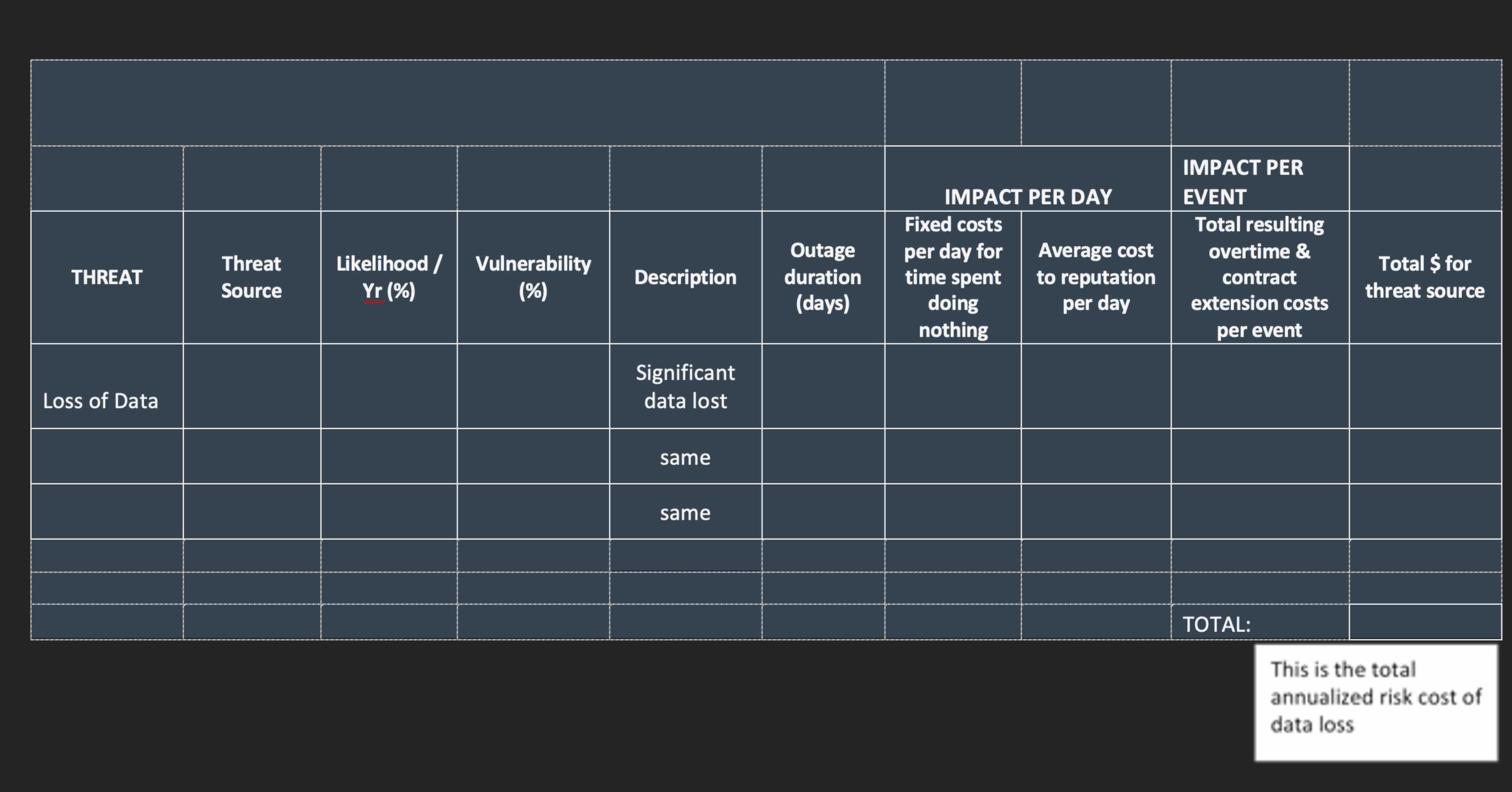
Quantitative Threat Analysis Springfield I.T Consulting develops and maintains business software for IT clients. Springfield is doing a threat analysis as part of a BCP creation project and so far they have identified several threats, In this exercise, we will focus on Data Loss. When Springfield IT Consulting loses data it could be any of the following: Work in progress, Completed work Financial data Three thrent sources have been identified for data loss: Hacking, Worker Error Hardware Failure Please calculate the total annualized risk cost of the data loss threat. Costs: During a data loss, fixed costs must be paid even if work is not being done are $ per day Reputation loss is calculated at $ per day since this is a consulting firm this value is high When a data loss happens there are overtime costs and contract extension costs each project has a deadline it must meet depending on the contract, Springfield could be charged a penalty if it does not meet the deadline. These overtime and contract extension costs vary depending on the source of the threat. These will be given as total cost per event, not per day and have been calculated based on historical data and currentfuture changes. Note: This means that when you are calculating your annualized risk cost your formula will be different from our other example. You need to add fixed costs for each day of doing nothing to reputation loss costs for one day and then multiply this sum by number of days. To this result you need to add the cost of overtime and contract extension. Then you need to multiply this total by likelihood vulnerability. You don't include the overtime and contract extension coses in che first calculation because it is not a per day cost but rather a per event cost. Every organization will have its own method of specifying impoce.tableIMPACT PER DAY,tableIMPACT PEREVENTTHREATtableThreatSourcetableLikelihood
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


