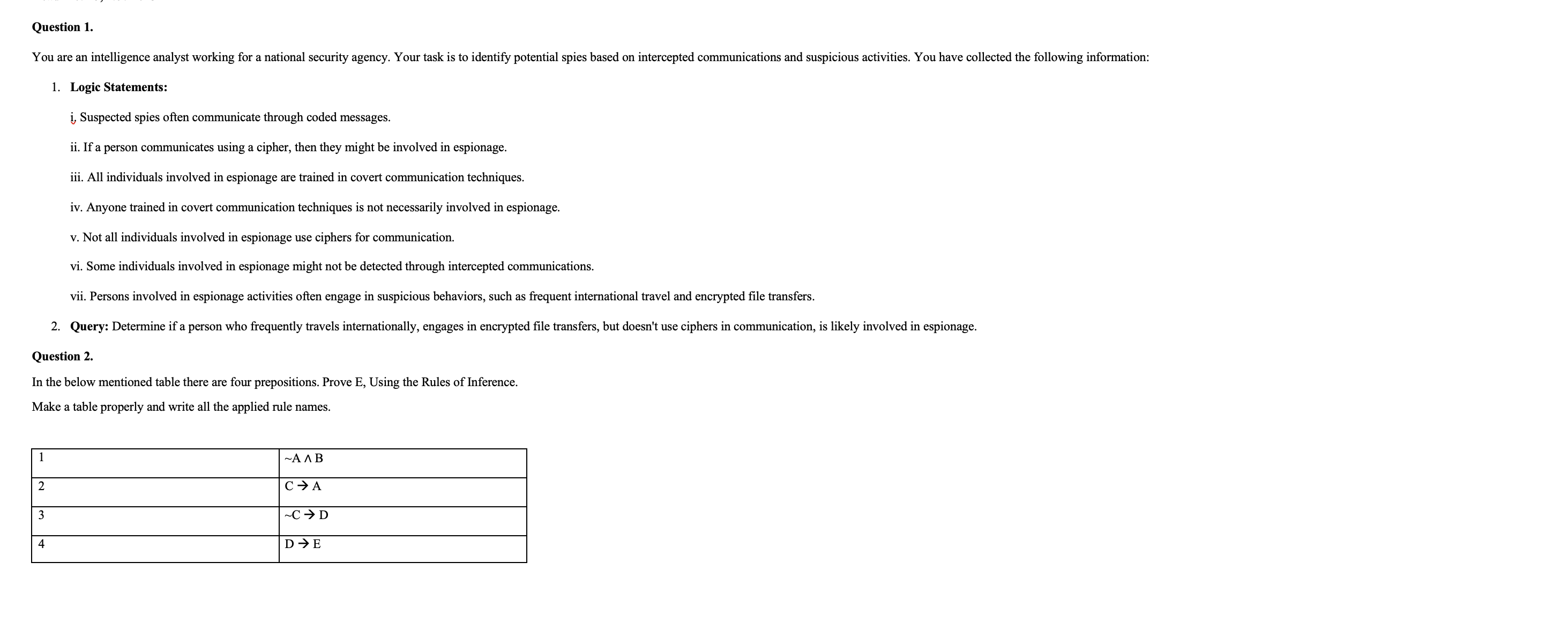
Question: Question 1 . Logic Statements: i , Suspected spies often communicate through coded messages. ii . If a person communicates using a cipher, then they
Question
Logic Statements:
i Suspected spies often communicate through coded messages.
ii If a person communicates using a cipher, then they might be involved in espionage.
iii. All individuals involved in espionage are trained in covert communication techniques.
iv Anyone trained in covert communication techniques is not necessarily involved in espionage.
v Not all individuals involved in espionage use ciphers for communication.
vi Some individuals involved in espionage might not be detected through intercepted communications.
vii. Persons involved in espionage activities often engage in suspicious behaviors, such as frequent international travel and encrypted file transfers.
Query: Determine if a person who frequently travels internationally, engages in encrypted file transfers, but doesn't use ciphers in communication, is likely involved in espionage.
Question
In the below mentioned table there are four prepositions. Prove E Using the Rules of Inference.
Make a table properly and write all the applied rule names.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


