Question: Question 21 (6 points) BASTION Inc. has changed their encryption practice from AES-128 to AES-256. Suppose that you happen to eavesdrop their network traffic and
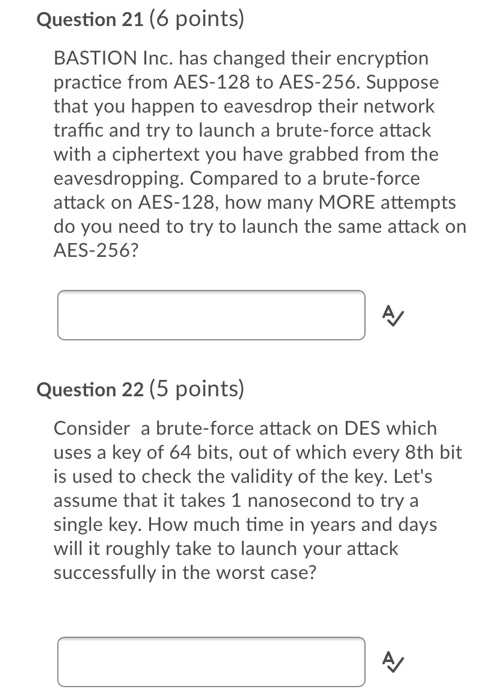
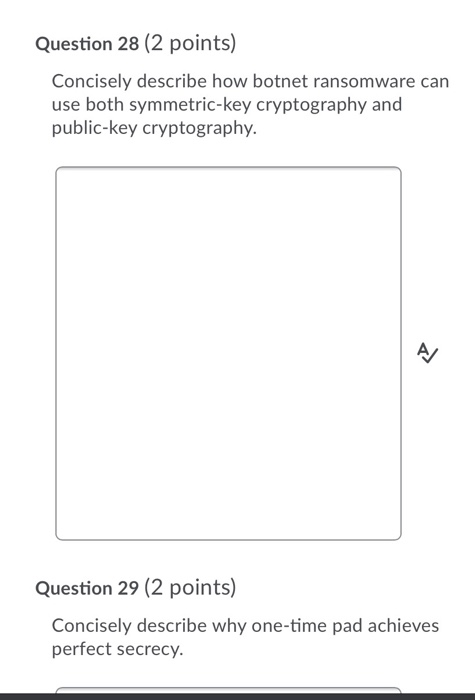
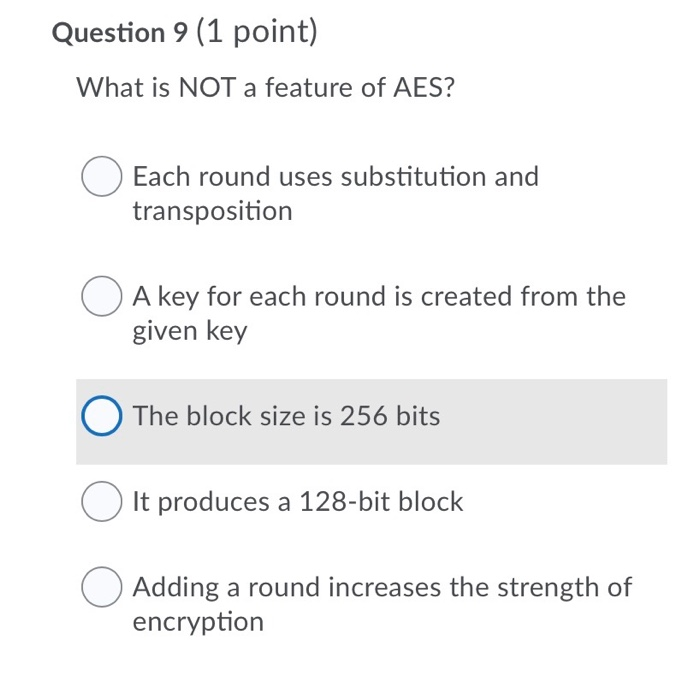
Question 21 (6 points) BASTION Inc. has changed their encryption practice from AES-128 to AES-256. Suppose that you happen to eavesdrop their network traffic and try to launch a brute-force attack with a ciphertext you have grabbed from the eavesdropping. Compared to a brute-force attack on AES-128, how many MORE attempts do you need to try to launch the same attack on AES-256? Question 22 (5 points) Consider a brute-force attack on DES which uses a key of 64 bits, out of which every 8th bit is used to check the validity of the key. Let's assume that it takes 1 nanosecond to try a single key. How much time in years and days will it roughly take to launch your attack successfully in the worst case? Question 28 (2 points) Concisely describe how botnet ransomware can use both symmetric-key cryptography and public-key cryptography. Question 29 (2 points) Concisely describe why one-time pad achieves perfect secrecy. Question 9 (1 point) What is NOT a feature of AES? Each round uses substitution and transposition O A key for each round is created from the given key O The block size is 256 bits O It produces a 128-bit block O Adding a round increases the strength of encryption
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


