Question: Question 28 (2 points) Concisely describe how botnet ransomware can use both symmetric-key cryptography and public-key cryptography. Question 29 (2 points) Concisely describe why one-time
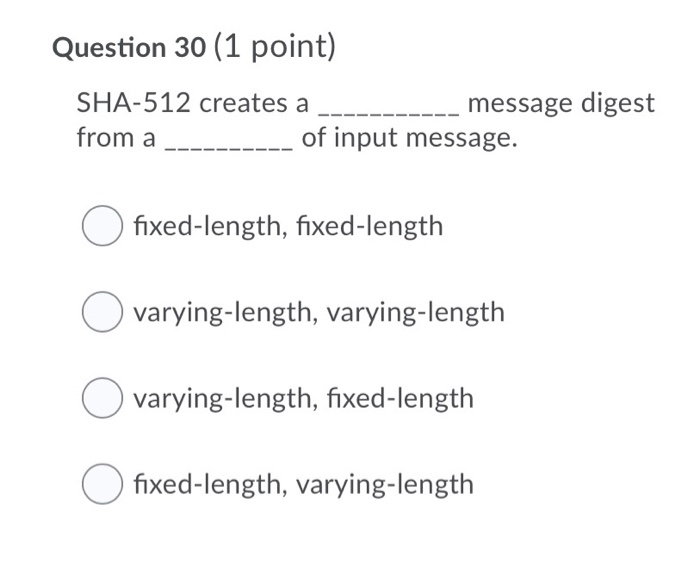
Question 28 (2 points) Concisely describe how botnet ransomware can use both symmetric-key cryptography and public-key cryptography. Question 29 (2 points) Concisely describe why one-time pad achieves perfect secrecy. Question 30 (1 point) SHA-512 creates a _ ---------- mes _ message digest from a ----------- of input message. O fixed-length, fixed-length O varying-length, varying-length O varying-length, fixed-length O fixed-length, varying-length
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


