Question: Question: Describe and demonstrate how you gained a root shell by exploiting the security flaw in the program from Code Listing 5 and Suggest how
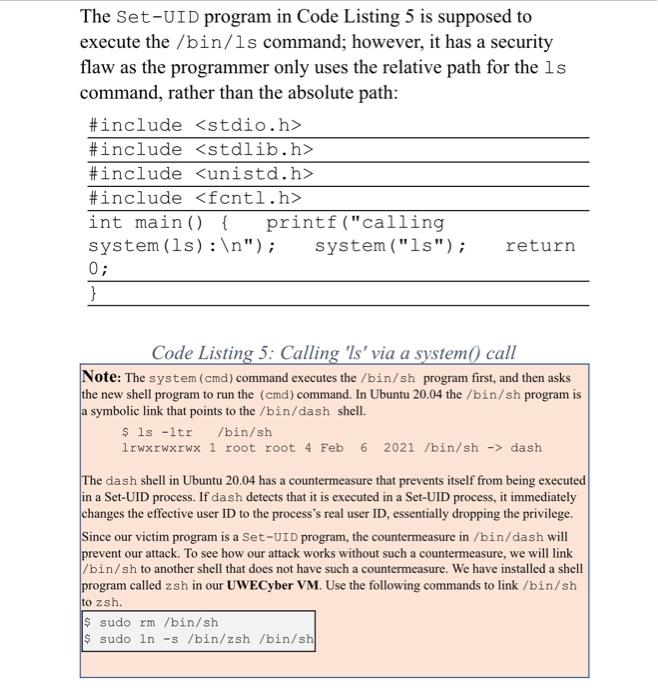
The Set-UID program in Code Listing 5 is supposed to execute the /bin/ls command; however, it has a security flaw as the programmer only uses the relative path for the ls command, rather than the absolute path: #include
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


