Question: Data Security Incident at the Florida Orthopedic Institute A) Analysis of Threats to the Organization's Information Systems Add few sentence introduction paragraph here... New Para(s):
Data Security Incident at the Florida Orthopedic Institute
A) Analysis of Threats to the Organization's Information Systems
Add few sentence introduction paragraph here...
New Para(s): Description of potential threats and vulnerabilities...
New Para(s): Risks to the confidentiality, integrity, and availability (CIA) triad...
New Para: Determine deviations from acceptable configurations, enterprise, or local policy; assess the level of risk.
New Para(s): Brief Summary of threats FOI could face. Address insider threats, intrusions, hacker psychology, and other weaknesses that may result in a data breach. Relate the threats to the CIA. **Consider adding Russian cyberattacks on the United States major industries due to current world conflicts.
Tips for question A
Short introduction - few sentences
Description of potential threats and vulnerabilities
Risks to the CIA triad
Step Note:
Provide a brief summary of the kinds of threats that an organization could face, addressing insider threats, intrusions, hacker psychology, and other weakness that might provide opportunities to breach the system. Relate these threats to the vulnerabilities in the CIA triad.
B) Proposed Mitigation Strategy
Add few sentence introduction paragraph here...
New Para(s): Proposed identity management system. Include authentication, authorization, and access control.
New Para(s): Managing roles, access, restrictions, and conditions.
New Para(s): Unknown risks and costs.
Tips for question B
Short introduction - few sentences
Proposed identity management system
Include a description of an identity management system, which will include authentication, authorization, and access control.
Managing roles, accesses, restrictions, and conditions
Unknown risks and costs.
Step Note:
Review the following resources:
Authorization
Access control
Passwords
Authentication
Multifactor authentication
To conduct a vulnerability assessment, a trained specialist would assess threats and vulnerabilities; determine deviations from acceptable configurations, enterprise, or local policy; assess the level of risk, and develop and/or recommend appropriate mitigation countermeasures in operational and nonoperational situations. Your team will not carry out all of these tasks, but you will assess the potential threats and vulnerabilities and the risk to your organization.
To complete this section of your report, start by reviewing the following resources:
Information System Architecture
Web Security Issues
Insider Threats
Intrusion Motives/Hacker Psychology
Explain how your organization should restrict access to protect billing and PHI. Explain the organization's processes and workflows to safeguard PHI, including the use of passwords, password management, and password protection. Define types of authorization and authentication and the use of passwords, password management, and password protection in an identity management system. Describe common factor authentication mechanisms to include multifactor authentication.
Finally, review the mission and organization structure of your organization as well as roles within it, and recommend accesses, restrictions, and conditions for each role. What will happen if the CIO and the leaders do nothing and decide to accept the risks? Could the CIO transfer, mitigate, or eliminate the risks? What are the projected costs to address the risks?

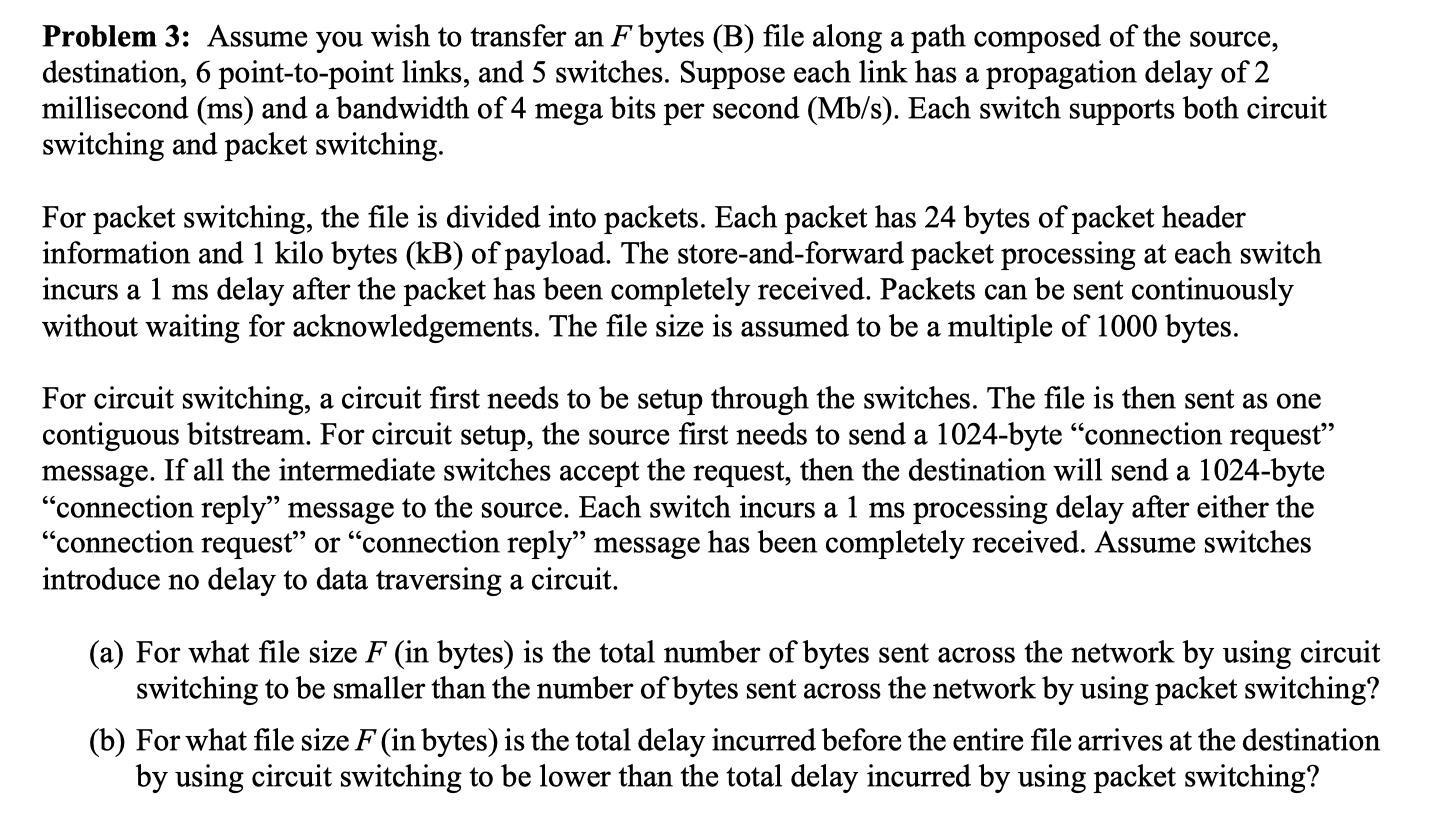
Questions Assume you want to transfer an n-byte file along a path consisting of the source, destination, four point-to-point links, and three switches. Suppose each link has a propagation delay of 2ms, bandwidth of 4 Mbps, and that the switches support both circuit and packet switching. Note that you can either break the file up into 1 KB packets, or set up a circuit through the switches and send the file as one contiguous bit stream. Suppose that packets have 24 bytes of packet header information and 1000 bytes of payload, that store-and-forward packet processing at each switch incurs a 2 ms delay after the packet has been completely received, that packets may be sent continuously without waiting for acknowledgments, and that circuit setup requires a 2 KB message to make one round-trip on the path incurring a 2 ms delay at each switch after the message has been completely received. Assume switches introduce no delay to data traversing a circuit. You may also assume that file size is a multiple of 1000 bytes. Calculate 1. For packet switching a) For what file size n bytes is the total number of bytes sent across the network b) For what file size n bytes is the total latency incurred before the entire file arrives at the destination network 2. For Circuit switching a) For what file size n bytes is the total number of bytes sent across the network b) For what file size n bytes is the total latency incurred before the entire file arrives at the destination network
Step by Step Solution
3.51 Rating (154 Votes )
There are 3 Steps involved in it
Assume you want to tr... View full answer

Get step-by-step solutions from verified subject matter experts


