Question: Questions: 1. Suppose Advanced Communications has a new application development project with projected revenues of $2 million. Using the following table, calculate the ARO and
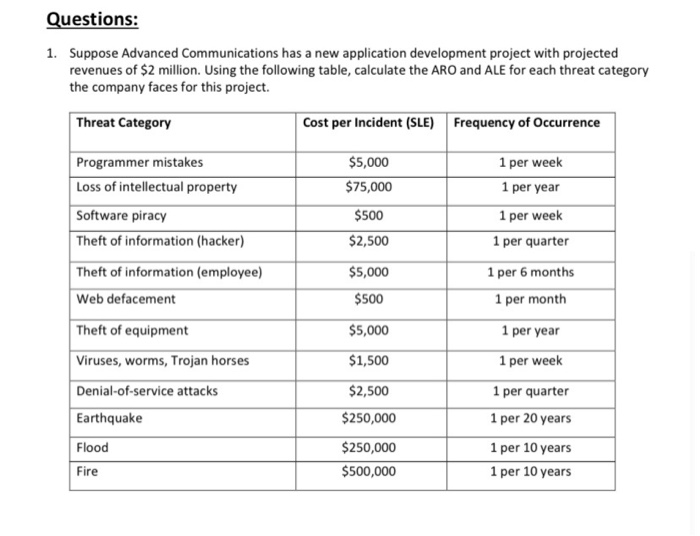
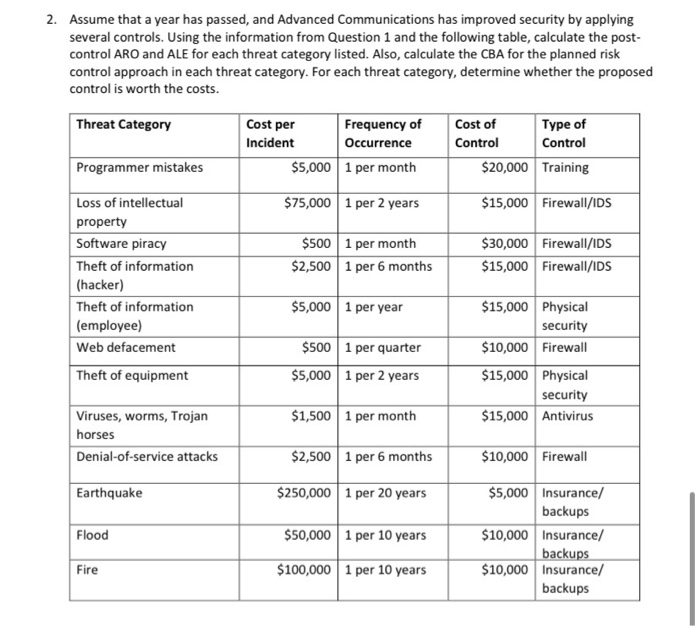
Questions: 1. Suppose Advanced Communications has a new application development project with projected revenues of $2 million. Using the following table, calculate the ARO and ALE for each threat category the company faces for this project. Threat Category Cost per Incident (SLE) Frequency of Occurrence 1 per week Programmer mistakes Loss of intellectual property 1 per year $5,000 $75,000 $500 $2,500 Software piracy Theft of information (hacker) 1 per week 1 per quarter Theft of information (employee) $5,000 $500 1 per 6 months 1 per month Web defacement Theft of equipment $5,000 1 per year Viruses, worms, Trojan horses $1,500 1 per week 1 per quarter Denial-of-service attacks Earthquake $2,500 $250,000 1 per 20 years Flood Fire $250,000 $500,000 1 per 10 years 1 per 10 years 2. Assume that a year has passed, and Advanced Communications has improved security by applying several controls. Using the information from Question 1 and the following table, calculate the post- control ARO and ALE for each threat category listed. Also, calculate the CBA for the planned risk control approach in each threat category. For each threat category, determine whether the proposed control is worth the costs. Threat Category Cost per Frequency of Incident Occurrence $5,000 1 per month Cost of Control $20,000 Type of Control Training Programmer mistakes $75,000 1 per 2 years $15,000 Firewall/IDS $5001 per month $2,5001 per 6 months $30,000 $15,000 Firewall/IDS Firewall/IDS Loss of intellectual property Software piracy Theft of information (hacker) Theft of information (employee) Web defacement $5,000 1 per year $15,000 Physical security Firewall $5001 per quarter $10,000 Theft of equipment $5,000 1 per 2 years $15,000 Physical security $15,000 Antivirus $1,5001 per month Viruses, worms, Trojan horses Denial-of-service attacks $2,5001 per 6 months $10,000 Firewall Earthquake $250,0001 per 20 years Flood $50,000 1 per 10 years $5,000 Insurance/ backups $10,000 Insurance/ backups $10,000 Insurance/ backups Fire $100,000 1 per 10 years 3. Using the Web, search for "software firewalls." Examine the various alternatives available and compare their functionality, cost, features, and type of protection. Create a weighted ranking according to your own evaluation of the features and specifications of each software package. 4. Access the firewall available on your personal computer (e.g. Windows Defender Firewall). Read the firewall documentation to determine how to configure inbound and outbound rules for it and practice defining rules for some applications of your choice. Write about your experience