Question: Queston 3 : Data Network and SecurityQueston 3 : Data Network and Security QUESTION 3 30 MARKS In year 2020, the world has been effected
Queston 3 : Data Network and SecurityQueston 3 : Data Network and Security

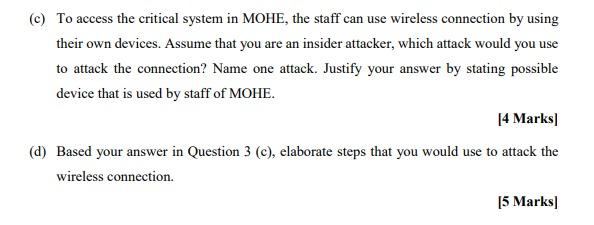
QUESTION 3 30 MARKS In year 2020, the world has been effected by Covid-19 Pandemic. In Malaysia to avoid the spreading of Covid-19, the government has announced to implement the new norms operation that should be followed by all citizens in all sectors. Malaysia's Ministry of Higher Education (MOHE) is not excluded in implementing the new norms. MOHE should provide responsive service to all education institutions, parents, and students. Thus MOHE has decided to provide new applications to improve the network design and connection within two months. The connection should consider the defend in-depth including physical and logical. MOHE has 5 high end servers for the portal that have been improved, 3 existing systems and 3 new applications. The building has 3 levels. The farm server is located at the 2nd level. This server will serve all the requests by all clients, insider or outsider. The internet connection includes wireless and wired networks. The devices that are attached to the network are not only the organization computers, but also the services allowed from personnel devices such as mobile phones, tablet, and laptop. Most of the personal devices will be attached to wireless connection. In MOHE there are 100 staff. 10 staff are located in the IT department. The wireless connection can be used by MOHE guests. (a) Based on the given scenario, identify suitable defend-in-depth that should be considered by MOHE to ensure the secured network connection. Identify THREE (3) technologies, TWO (2) procedures and ONE (1) awareness training. 16 Marks (b) Draw a network design and show the location of the technologies that has been identified in Question 3 (a). [15 Marks (c) To access the critical system in MOHE, the staff can use wireless connection by using their own devices. Assume that you are an insider attacker, which attack would you use to attack the connection? Name one attack. Justify your answer by stating possible device that is used by staff of MOHE. [4 Marks (d) Based your answer in Question 3 (c), elaborate steps that you would use to attack the wireless connection. (5 Marks QUESTION 3 30 MARKS In year 2020, the world has been effected by Covid-19 Pandemic. In Malaysia to avoid the spreading of Covid-19, the government has announced to implement the new norms operation that should be followed by all citizens in all sectors. Malaysia's Ministry of Higher Education (MOHE) is not excluded in implementing the new norms. MOHE should provide responsive service to all education institutions, parents, and students. Thus MOHE has decided to provide new applications to improve the network design and connection within two months. The connection should consider the defend in-depth including physical and logical. MOHE has 5 high end servers for the portal that have been improved, 3 existing systems and 3 new applications. The building has 3 levels. The farm server is located at the 2nd level. This server will serve all the requests by all clients, insider or outsider. The internet connection includes wireless and wired networks. The devices that are attached to the network are not only the organization computers, but also the services allowed from personnel devices such as mobile phones, tablet, and laptop. Most of the personal devices will be attached to wireless connection. In MOHE there are 100 staff. 10 staff are located in the IT department. The wireless connection can be used by MOHE guests. (a) Based on the given scenario, identify suitable defend-in-depth that should be considered by MOHE to ensure the secured network connection. Identify THREE (3) technologies, TWO (2) procedures and ONE (1) awareness training. 16 Marks (b) Draw a network design and show the location of the technologies that has been identified in Question 3 (a). [15 Marks (c) To access the critical system in MOHE, the staff can use wireless connection by using their own devices. Assume that you are an insider attacker, which attack would you use to attack the connection? Name one attack. Justify your answer by stating possible device that is used by staff of MOHE. [4 Marks (d) Based your answer in Question 3 (c), elaborate steps that you would use to attack the wireless connection. (5 Marks
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


