Question: Research: Please explain in-detail the typically traffic flow from your browser to a web site that uses a trusted certificate (https). Please include firewall rules,
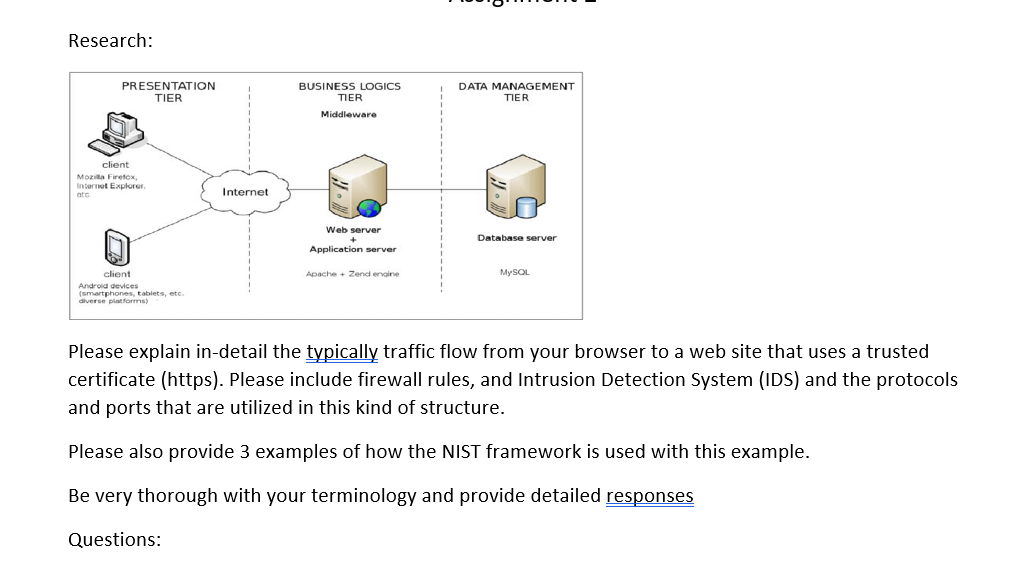

Research: Please explain in-detail the typically traffic flow from your browser to a web site that uses a trusted certificate (https). Please include firewall rules, and Intrusion Detection System (IDS) and the protocols and ports that are utilized in this kind of structure. Please also provide 3 examples of how the NIST framework is used with this example. Be very thorough with your terminology and provide detailed responses Questions: 1) You are troubleshooting some anomalies with network communication on your network. You notice that some communication isn't taking the expected or most efficient route to the destination. Which layer of the OSI model you should troubleshoot? Your company uses VolP for internal telephone calls. You are deploying a new intrusion detection system and need to capture traffic related to internal telephone calls only. Which protocol should you capture? You are performing a security audit for a customer. During the audit, you find several instances of users gaining access to data without going through a formal access approval process. As part of the remediation, you recommend establishing a formal access approval process. Which role should you list to approve policies that dictate which users can gain access to data
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


