Question: Software Vulnerabilities Analysis Consider an authentication protocol that enables a reader to authenticate a user based on sharing a pair of 3-bit keys, Si and
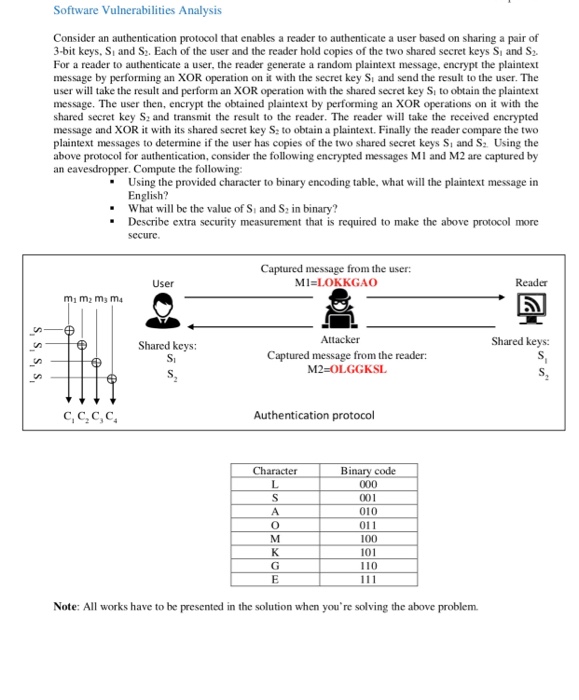
Software Vulnerabilities Analysis Consider an authentication protocol that enables a reader to authenticate a user based on sharing a pair of 3-bit keys, Si and S. Each of the user and the reader hold copies of the two shared secret keys Si and S For a reader to authenticate a user, the reader generate a random plaintext message, encrypt the plaintext message by performing an XOR operation on it with the secret key Si and send the result to the user. The user will take the result and perform an XOR operation with the shared secret key Si to obtain the plaintext message. The user then, encrypt the obtained plaintext by performing an XOR operations on it with the shared secret key S and transmit the result to the reader. The reader will take the received encrypted message and XOR it with its shared secret key S: to obtain a plaintext. Finally the reader compare the two plaintext messages to determine if the user has copies of the two shared secret keys Si and S. Using the above protocol for authentication, consider the following encrypted messages MI and M2 are captured by an eavesdropper. Compute the following: Using the provided character to binary encoding table, what will the plaintext message in English? What will be the value of Si and S in binary? Describe extra security measurement that is required to make the above protocol more Captured message from the user: M1-LOKKGAO m1 m2 m3 m4 Shared keys: Attacker Shared keys: Captured message from the reader: M2-OLGGKSI C,C,C,C, Authentication protocol Character Binary code 001 010 100 110 Note: All works have to be presented in the solution when you're solving the above
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


