Question: -Source A- -Destination B- Compare (a) Message authentication Cu(MD) Compare EXIMICx,(M) Ek [M] KK Compare K2 CkEx,(M)] What different mechanisms are being used in each
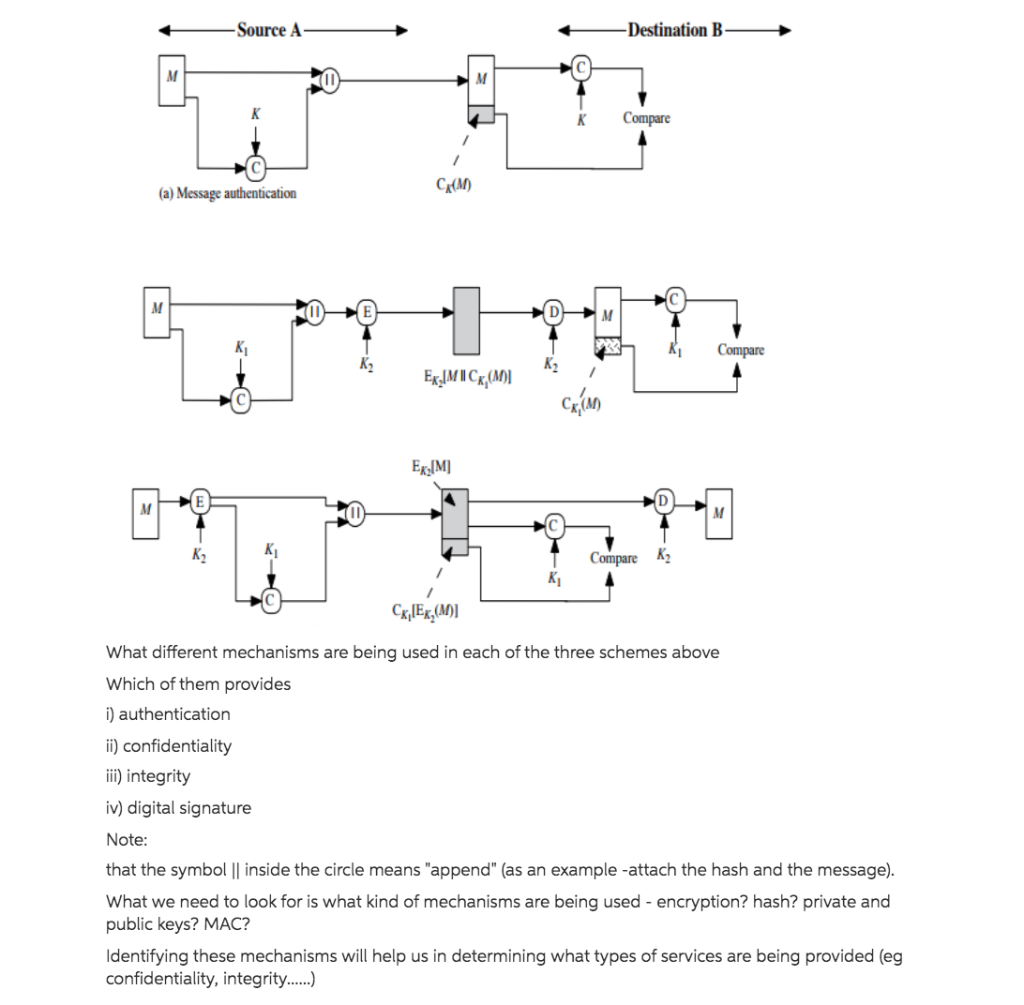
-Source A- -Destination B- Compare (a) Message authentication Cu(MD) Compare EXIMICx,(M) Ek [M] KK Compare K2 CkEx,(M)] What different mechanisms are being used in each of the three schemes above Which of them provides i) authentication ii) confidentiality iii) integrity iv) digital signature Note: that the symbol || inside the circle means "append" (as an example -attach the hash and the message). What we need to look for is what kind of mechanisms are being used - encryption? hash? private and public keys? MAC? Identifying these mechanisms will help us in determining what types of services are being provided (eg confidentiality, integrity......)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


