Question: SQL Injection AttacksImplement two different web sites having login pages with the following difference: 1 . In the first one, SQLi attacks should be possible
SQL Injection AttacksImplement two different web sites having login pages with the following difference:In the first one, SQLi attacks should be possibleIn the second one, prevent SQLi attacks with parameterized query insertion.Loading Details of the first Web siteCreate a simple Web application having two pages:The first page will be a user authentication page requiring correct user ID and password.If the user Id and password are entered correctly or if user is a registered user then he will be able to see the second page. Second page will include sensitive data you will decide the content of the pageYou add other pages if required for example, user registrationsign in page Details of the first Web siteInstall a Web server and a DBMS For example, XAMPPCreate a database and a user table for authentication.User password should be stored as a hash value You can use MD for exampleFor server side programming, you can use PHP or any other language.A browser should be used to connect to your application.LoadingYou will develop such a systemUser should be able to write the fields of the SQL query on formstextbox The content of the textbox should be used to build SQL queries as follows:uName getRequestStringusername;uPass getRequestStringuserpassword;sql 'SELECT FROM Users WHERE Name uName AND Pass uPass On the server side:Build SQL query using sent formExecute SQL queryIf SQL returns the specified user, then accept user for login and see the second page Details of the first Web siteModify your first Web app to prevent SQLi attacks.You are expected to prevent SQLi attacks with parameterized query insertion. Details of the second Web site Details of the second Web siteSQL parameters are values that are added to an SQL query at execution time, in a controlled manner.
:
All iCloud
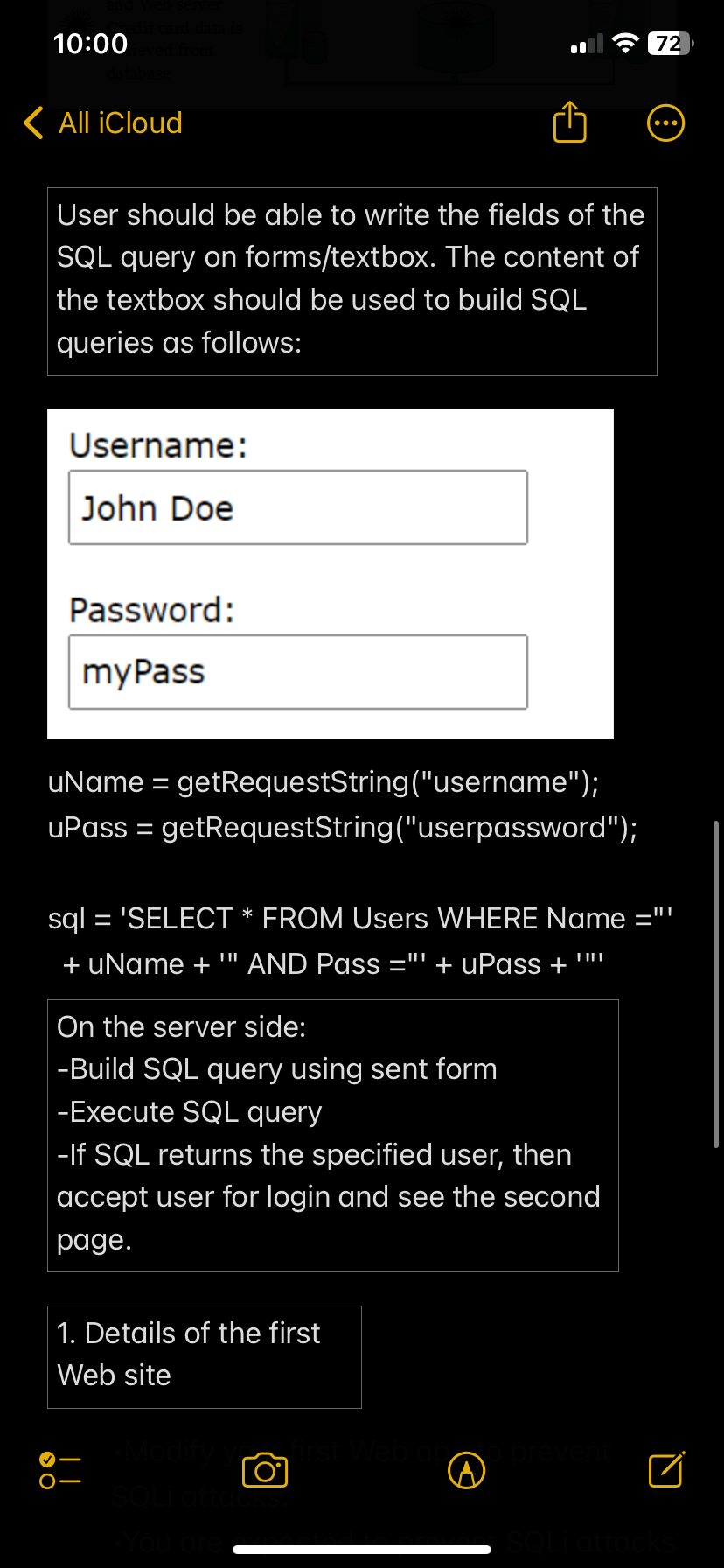
User should be able to write the fields of the SQL query on formstextbox The content of the textbox should be used to build SQL queries as follows:
Username:
John Doe
Password:
uName getRequestString username;
uPass getRequestStringuserpassword;
'SELECT FROM Users WHERE Name
uName AND Pass uPass
On the server side:
Build SQL query using sent form
Execute SQL query
If SQL returns the specified user, then accept user for login and see the second page.
Details of the first
Web site
o
A
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


