Question: Substitution method: The message given by the user is encrypted by substitute its characters to another characters based on an encryption dictionary (table) hard-coded in
Substitution method:
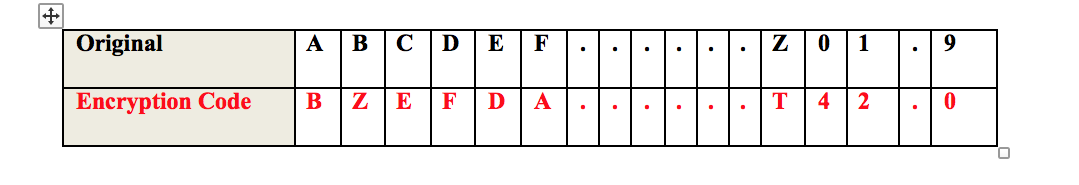
The message given by the user is encrypted by substitute its characters to another characters based on an encryption dictionary (table) hard-coded in the project. Example of the encryption dictionary is illustrated in table 1.
Table 1 Encryption Dictionary
Encryption Example:
Person 1 enters a message: HELLO
Encryption project will produce: ODIIY
Which could be sent over a communication media to the corresponding receiver Person 2.
Person2 should have the same system with the same Encryption Dictionary to decrypt the message and get back the original message.
The decryption is the reverse operation of the encryption. It uses the same encryption dictionary, but starting from the Encryption Code towards the Original to re-build the original message.
Back to our example above the message HELLO will be encrypted according to our dictionary (H O, ED, LI, O Y) the encrypted message will be (ODIIY). Now to retrieve the original message we have to use the same dictionary in opposite direction (O H, DE, IL, Y O)
Transposition Encryption Method:
The transposition encryption is based on an encryption key that can be changed by the user or randomly by the program. The encryption key could have different order but with a fixed size (program specific) to encrypt and decrypt messages.
Encryption Example:
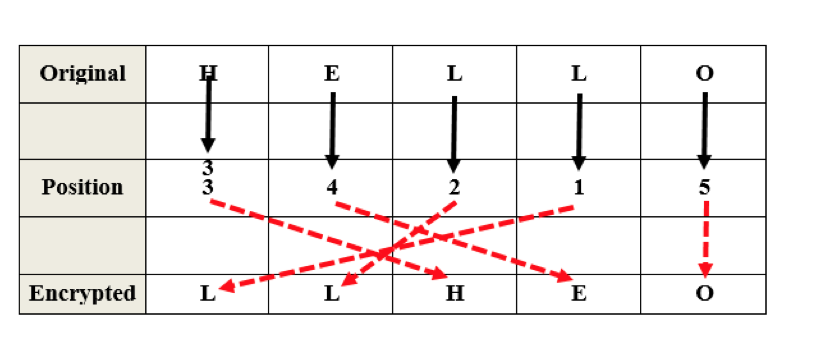
Suppose we have a key of 5 digits as ( 3 4 2 1 5 ) to encrypt a word HELLO. The key transforms the first letter from the original message to the third position, the second letter from the original message to the fourth position, the third letter from the original message to the second position and so on. Table 2 illustrtes the transposition encryption to the message "HELLO" to " LLHEO".
Table 2 Transposition Encryption Example
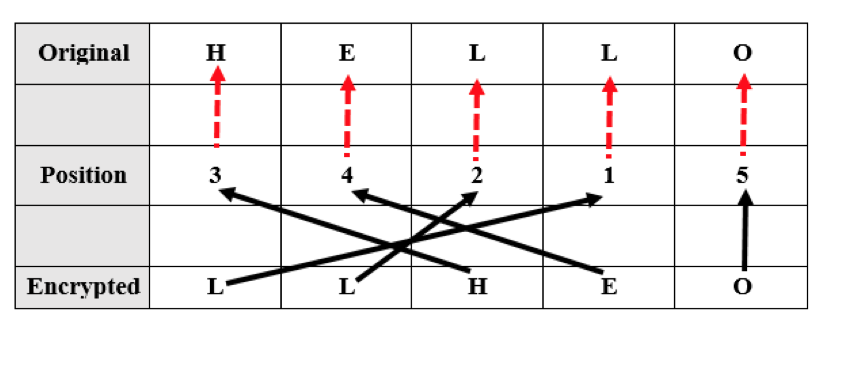
The transposition decryption is the opposite operation to the encryption. It starts by the Encrypted message towards the original message following the path of the arrows in Table 2 we notice the decryption key is ( 4 3 1 2 5).
Table 3 Decryption Transposition
Solving specifications:
Your solving should be constructed in modular way. So the main function will be simple and all the real work should be organized in functions.
Your solving should show an instruction message explaining the purpose of the program
Your solving should not stop automatically, it should have an option that allow the user to terminate the program.
The user will select what encryption method to use.
There should be two options to input a message to your program:
Allow the user to type his original message and your program will produce the encrypted version (instance typing)
Allow the user to specify a filename1 containing the original message. The program will read that file and uses the encryption method selected by the user to encrypt the message. The output will be in another file named filename1_encrypt.
The user can select either encryption or decryption to the messages!
the solving should use only #include
Any help is acceptable. thank u :)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


